Managed Security Services (MSS)
With 22 years in cybersecurity, ScienceSoft builds, maintains, and customizes cloud-first security infrastructures, so our clients can focus on their businesses with full confidence in the defense against ever-evolving cyber threats.

Dmitry Kurskov
ScienceSoft's Cybersecurity Director and Principal Architect
Managed security services (MSS) aim to protect your IT infrastructure and applications in a continuous and cost-effective manner by outsourcing your security tasks to an expert. As a mature MSSP, ScienceSoft offers full-scale services from security infrastructure design and implementation to incident response.
Key Areas We Take Care Of
- Endpoints: desktops, laptops, mobile devices, and more.
- Connecting devices: routers, switches, gateways, Wi-Fi access points, etc.
- Email services.
- Customer-facing applications: e.g., customer portals, ecommerce websites, online and mobile banking, SaaS applications.
- Internal applications: e.g., ERP, CRM, EHR/EMR, document management, business intelligence apps.
Data storage
- Databases.
- Data warehouses.
- Data lakes.
- On-premise data centers.
What Our Managed Security Services Cover
Security infrastructure planning
- Evaluating the existing security policies, procedures, and technologies.
- Designing cloud-first cybersecurity infrastructure and a comprehensive, future-proof security program or security policies and procedures.
- Regular vulnerability assessments, penetration testing, social engineering testing, and security policy reviews to identify and prioritize security issues.
- Remediation of detected vulnerabilities.
Compliance management
- Regular compliance assessments against HIPAA, PCI DSS, GDPR, NIST SP 800-53, SOC 2, NYDFS, and other security standards and regulations.
- Remediation of detected gaps.
Network security management
- Setup and maintenance of network protection technologies like firewalls, routers, and DDoS protection solutions.
- Management of web filtering/SWG, antivirus, anti-malware, and other endpoint protection solutions.
- Email security system management
- Architecture design to seamlessly integrate SIEM solutions into your IT environment.
- Deployment and customization to centralize security monitoring and eliminate false positives.
- Management to ensure proper functioning of the SIEM solution and detection of emerging attacks.
Security monitoring and threat detection
- Continuous (365 days a year) security monitoring, analysis of security events, and early threat detection.
- Threat intelligence (e.g., provided by ServiceNow Security Operations) to stay informed about new vulnerabilities and threats related to your infrastructure.
Intrusion detection and prevention
IDS/IPS deployment to swiftly identify and protect against intrusion attempts and cyberattacks in real time.
Incident response and remediation
Helping contain the incident, investigate its scope, and work with your organization to remediate the issue and prevent future security events.
Other services our MSS clients are interested in
To efficiently handle user requests and issues related to apps and IT infrastructure on the following support levels:
- L1 – For basic issues (e.g., software setup, granting and revoking access rights based on the company’s policies).
- L2 – For complex technical problems and common infrastructure requests (e.g., server upgrades and patching management, MFA management).
- L3 – For advanced problems and requests (e.g., code changes, network configuration).
To ensure stability, safety and high performance of the IT infrastructure with 24x7x365 support services, including:
- Proactive monitoring, management, and troubleshooting.
- Designing and implementing IT infrastructure changes (e.g., optimization, expansion, cloud migration).
- Finding and resolving root causes of incidents.
Cyber Threats We Shield You From
Viruses, worms, and trojans
Injection attacks
Man-in-the-middle attacks
Spyware and keyloggers
Identity theft
Unauthorized access
Insider attacks
Well-oiled security processes are integral to mitigating cyber risks associated with fast-evolving apps and dynamic IT infrastructures. To bring cybersecurity into every SDLC stage, ScienceSoft adopted a SecOps approach of effective collaboration between software developers, security experts, and IT operations specialists.
What Makes ScienceSoft a Go-To Managed Security Provider
Vast experience and multi-faceted expertise
- 22 years in IT security, a cloud-centric MSSP advocating the Prevent–Manage–Detect–Respond model.
- Proficiency in security standards and regulations: HIPAA, PCI DSS, GDPR, SOC 2, NIST SP 800-53, NYDFS, and more.
- 13 years in cloud services; a Microsoft Partner, an AWS Select Tier Services Partner.
- Hands-on experience with IoT, blockchain, AR/VR, AI/ML development and security.
-
Deep understanding of the specific business needs and goals thanks to the multi-industry expertise, including healthcare, BFSI, manufacturing, retail, and professional services.
Dedication to quality
- A structured approach to cybersecurity managed services based on 17 years of ITSM experience.
- A mature quality management system backed by ISO 9001 certification that guarantees tangible value of our services, predictable results, and cost optimization that doesn’t happen at the expense of quality.
- ISO 27001-certified cybersecurity management based on field-tested security knowledge, comprehensive security policies, and well-coordinated security team work.
-
We guarantee transparent collaboration with regular updates on the conducted activities (security testing, vulnerability remediation, incident response, etc.) and flexible communication frequency.
Recognized credibility
- 62% of our revenue comes from long-term customers that stay with us for 2+ years.
Our awards, certifications, and partnerships
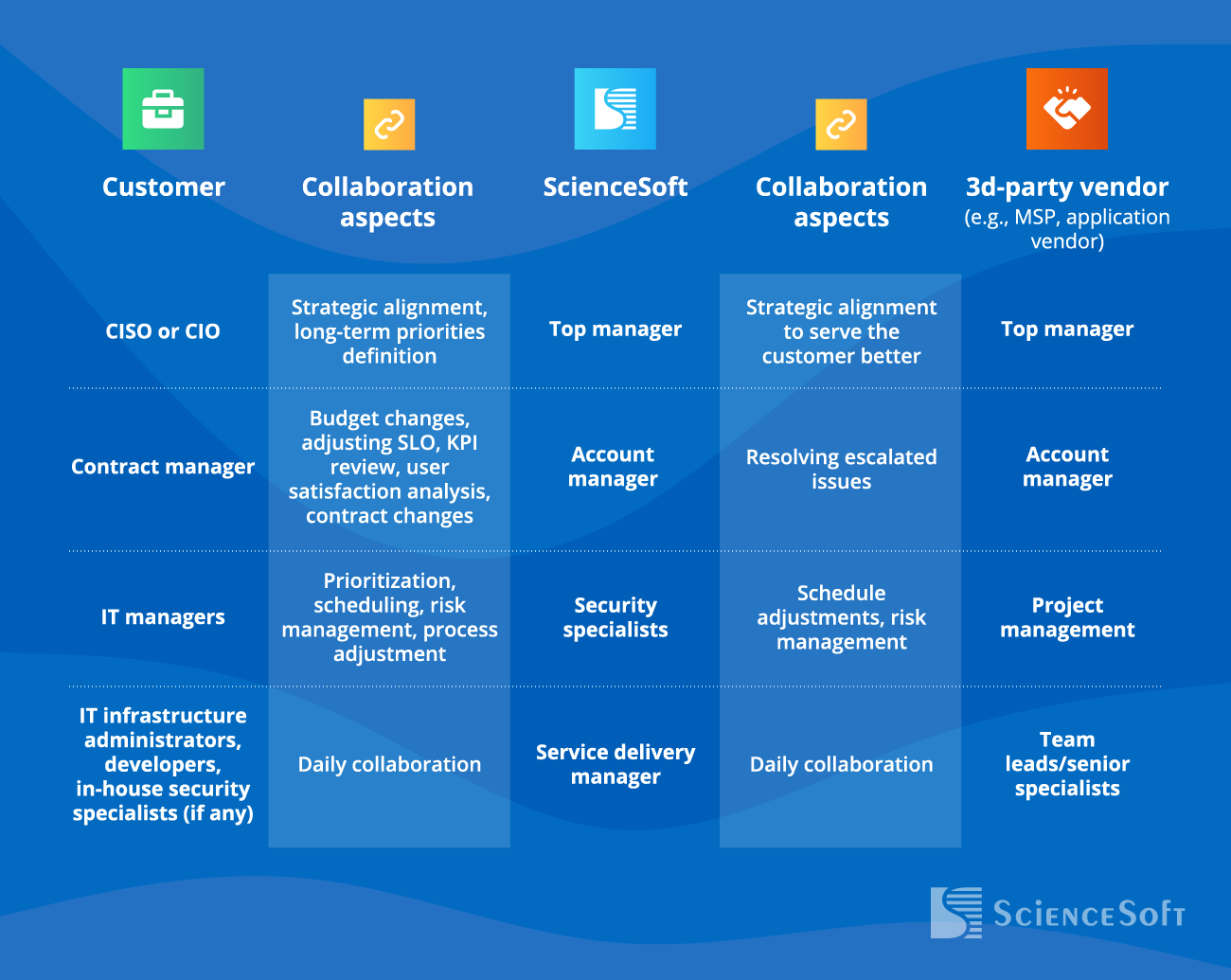
Like Clockwork: How Our Collaboration Runs
To deliver the best value for our clients, we build our cooperation on the following principles:
- SecOps approach: working together with IT operations specialists and software developers to build optimal cyber protection, taking into consideration your budget and technical limitations.
- Minimizing managerial efforts on the client’s side.
- Result-oriented collaboration with smart KPIs.
Check our sample KPI system
Our sample KPI system:
Output:
- Devices monitored.
- Endpoints monitored.
- Events gathered.
- Events stored.
- Log data retained.
Outcomes:
Security incidents:
- Incidents detected.
- Incidents resolved.
- Incident response time.
Protection level:
- Vulnerabilities found.
- Vulnerability fixes delayed.
- Overall cybersecurity level (assessment-based).
Changes in cybersecurity components:
- Implemented.
- Waiting in a backlog.
- Waiting in a backlog longer than the threshold set by SLA.
Hide
This is how our collaboration may look
Our key cooperation steps
1
Discovery and service planning
- Analyzing the customer’s IT landscape and the cybersecurity tools in use.
- Eliciting the security needs based on the incident history, change backlogs, business plans, and input from IT and business departments.
- Developing and presenting a service plan.
2
SLA creation
- SLA preparation and negotiation.
- Contract signing.
3
Transition
- Gathering exhaustive knowledge of the client’s IT environment: IT assets, configurations, documentation, policies, process descriptions, etc.
- Transfer of responsibility to our security experts.
4
Service delivery
- Providing the security services requested by the customer.
- Reporting on the results of our work according to the schedule (e.g., weekly, every 2 weeks, monthly) to ensure complete service visibility.
5
Improvements
- Quarterly proposals on how to enhance the security management processes in place.
Any security infrastructure we build, any policies and procedures we develop are our client's property. If their plans regarding our cooperation change, we are always ready to hand over all the service deliverables and transfer our knowledge to a new team.
Pragmatism and Flexibility: Pricing Models We Offer
Fixed monthly fee
For security technology management and IT infrastructure monitoring (based on the estimated number and type of log sources and security tools).
Time and Material
- For large-scale consulting and transformation services (e.g., security program development, shifting to cloud security tools).
- For incident response activities (depending on the damage done).
Fixed price
For small-scale activities with a defined scope (e.g., setting up and configuring a new firewall).
Benefits You Get with Our Expert Managed Security Services
Cyber protection efficiency instead of complexity
Why important: Organizations juggle an average of 83 security solutions from 29 vendors, and 52% of executives say complexity limits their ability to deal with cyber threats, according to IBM and Palo Alto Networks.
What we do: ScienceSoft carefully investigates each client’s unique IT infrastructure and analyzes attack vectors. With a clear vision of the client’s needs, we set up and properly configure best-fitting security tools and establish well-defined security policies and procedures.
Timely detection and remediation of vulnerabilities
Why important: 48,448 new software vulnerabilities were published in 2025.
What we do: We conduct regular security and compliance assessments to ensure software releases, integrations, and other changes in your networks, applications, and systems don’t compromise your security. ScienceSoft’s security experts constantly hone their skills and keep up-to-date with emerging cyber threats.
Rapid security incident detection and mitigation
Why important: $4.4M is the global average cost of a data breach, according to IBM.
What we do: As an ISO 27001-certified company, ScienceSoft has profound knowledge and experience in all aspects of security management. Our security experts are trained in incident response and follow established processes of handling potential and occurring incidents according to their nature and severity.
Set Your Objectives. We’ll Make It Happen!
Aim #1: Building proper cyber defenses within a few months.
- Consultants ready to start the discovery without delay.
- Standardized processes and policy templates to streamline security planning.
- Fast-to-deploy cloud security tools.
Aim #2: Covering all security needs with minimized investments in security tools and personnel.
- Cost optimization strategies and targeted security infrastructure improvements (pay only for what you need).
- On-demand availability of skilled security architects, admins, analysts, testers, and compliance consultants.
- Primarily cloud-based security components, which is typically cheaper.
Aim #3: Resisting advanced persistent threats.
- Advanced event and flow analysis.
- SIEM and log management.
- Protection against the external and insider threats
Aim #4: Continuous compliance with the applicable security standards and regulations.
- The software and network security controls required by the standards and regulations you must comply with.
- Regular compliance assessment.
- If needed, designing the security program, policies and procedures aimed to ensure compliance.
Aim #5: No vendor lock-in.
- Service not bound to a specific technology, but tailored to your needs and the existing tech landscape.
- Smooth transfer of the deliverables and knowledge to another team in case you stop our cooperation.






