Healthcare Penetration Testing Services
With 20+ years of experience in IT security and healthcare IT, ScienceSoft delivers pentesting services to verify the security of healthcare apps, IT infrastructures, and medical devices. Our experts go beyond common checklists and explore all possible attack vectors. We help organizations understand the cyber risks and prioritize remediation efforts.
Healthcare penetration testing enables healthcare providers, medical software product companies, and other organizations in the field to get a clear view of security issues in their networks, applications, and medical devices and prevent compliance breaches.
At ScienceSoft, we apply our combined expertise in security testing and healthcare IT to guarantee reliable protection for healthcare systems of any complexity.
Who We Serve
|
|
What We Test
Healthcare IT infrastructure components
Our experts examine public networks and intranets to identify vulnerabilities to external attacks and insider threats.
Software and firmware
We test solutions of any complexity, from patient portals and mHealth apps to highly integrated EHR/EMR solutions and connected medical devices.
Data storage
We spot security and compliance issues in on-premises and cloud data storage and processing systems (healthcare data warehouses, data lakes, etc.).
Healthcare solutions powered by advanced technologies
Penetration Testing Types We Cover
Request a Custom Set of Pentesting Services
We are ready to adapt the scope of penetration testing to your specific security and compliance requirements as well as time and budget constraints.
Why Healthcare Companies Choose ScienceSoft
- Since 2003 in cybersecurity.
- Since 2005 in healthcare IT and compliance.
- Certified Ethical Hackers on board.
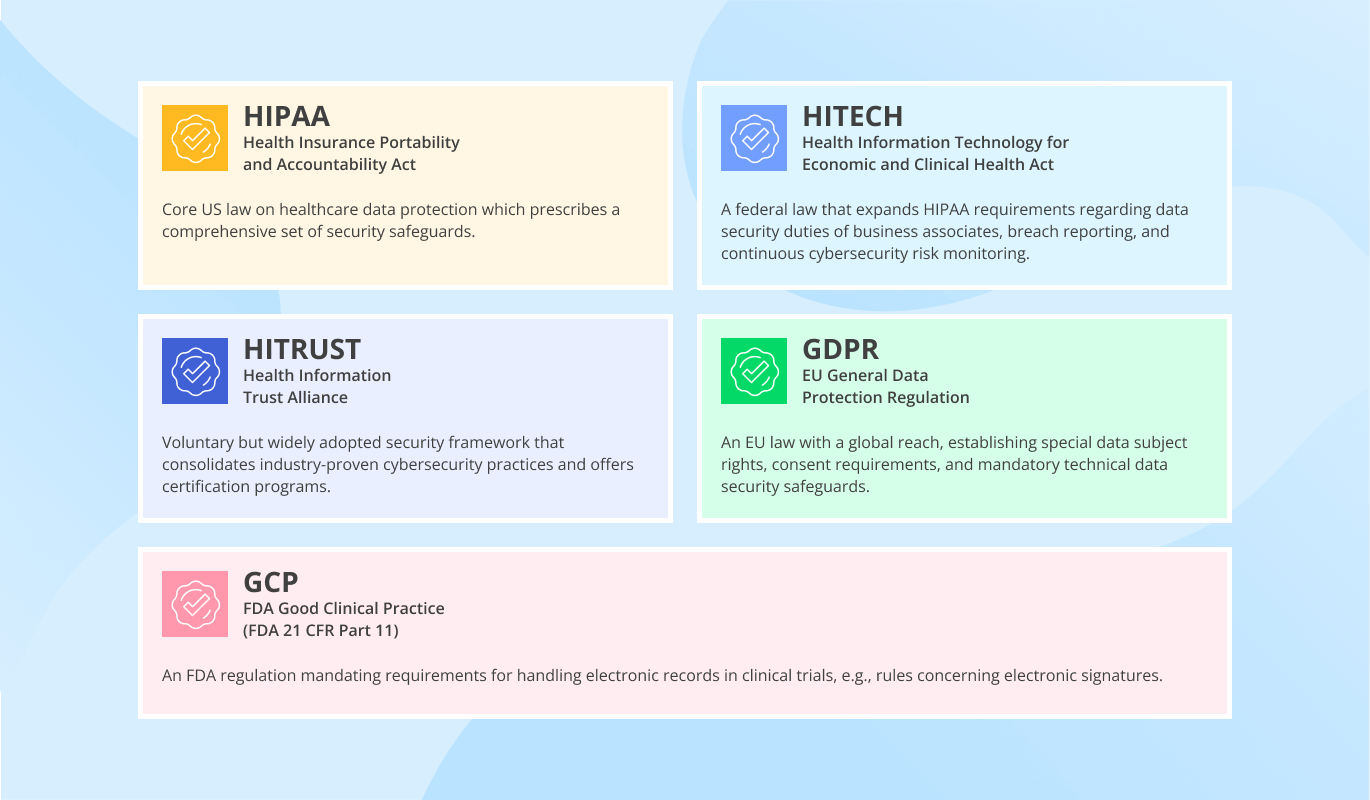
- Compliance consultants well-versed in HIPAA, HITECH, HITRUST CSF, FDA, MDR, 21 CFR Part 11, GDPR, SOC 2, NIST, PCI DSS, and more.
- Certified cloud security experts (AWS Certified Security – Specialty, Microsoft Certified: Azure Security Engineer Associate).
- Quality-first approach and a mature quality management system confirmed by ISO 13485 and ISO 9001 certifications.
- Robust data security management supported by an ISO 27001 certificate.
Our Three Main Penetration Testing Methods
We simulate an outsider attack without prior knowledge of the target.
With only publicly available information about your company or solution and using ethical hacking tools, our pentesters explore and exploit vulnerabilities in an attempt to breach the security perimeter.
Key benefit: This is often the fastest and the most cost-effective pentesting method.
Our pentesters act as a skilled attacker who has limited access to or knowledge of the target.
Using architecture diagrams, network design documents, or low-privileged user credentials, ScienceSoft's team explores internal vulnerabilities and their impact.
Key benefit: This method balances cost- and time-effectiveness with exploration depth.
Our experts imitate the actions of a malicious insider or an intruder who gained full access to the target.
We assess the security of your internal systems and meticulously examine the source code to spot the most intricate vulnerabilities.
Key benefit: This is the most exhaustive method.
Proven Techs & Tools We Use for Healthcare Pentesting
Vulnerability assessment and penetration testing
Secure code review
Smart contract security review
The Process of Healthcare Penetration Testing
1.
Contact & planning
This is how we start:
- Within 24 hours upon receiving your request, our rep will contact you to schedule an introductory call to discuss your case. Before the call, we can sign an NDA (Non-Disclosure Agreement) to ensure the legal protection of your confidential business information.
- Based on the analysis of your security and compliance needs, we prepare a proposal that specifies the testing approach, scope, methodology, team composition, timelines, and estimated costs.
- We are ready to sign a BAA (Business Associate Agreement) in case we have access to systems that handle PHI.
- After signing a service contract, we assemble a pentesting team and launch the project within one week.
2.
Testing
- Our pentesting team applies open-source intelligence (OSINT) techniques to gather publicly available info about your IT infrastructure or software.
- Based on the collected data and available documentation (depending on the selected method, it can be software specifications, source code, or architecture diagrams), ScienceSoft's team determines possible threat vectors and attack scenarios.
- After automated vulnerability scanning, ScienceSoft's pentesters manually verify the vulnerabilities detected in the target networks, apps, devices, and source code to ensure accurate results with no false positives.
- Our team follows best security testing practices established by OWASP, PTES, and NIST SP 800-115 when conducting such penetration testing activities as:
- Brute-forcing of standard or default credentials.
- Exploiting insufficient input validation (directory traversal, injections, overflows).
3.
Reporting & remediation
- Our pentesting team delivers a comprehensive report that describes the completed testing activities and the found vulnerabilities. We follow NIST CVSS and OWASP classifications to assess and prioritize found security issues based on their severity and breakthrough likelihood.
- We clearly describe the corrective measures needed to fix each of the found vulnerabilities.
- Upon the client's request, we can implement the required fixes to software code and healthcare IT infrastructure or establish the necessary procedures and policies to achieve compliance with security standards and regulations.
- Finally, our team follows up with a retesting round to verify the applied fixes.
Wondering How Much a Professional Pen Test Will Cost You?
Answer a few simple questions about your pentesting needs. This will help our team provide a tailored estimate for your case much quicker.
Thank you for your request!
We will analyze your case and get back to you within a business day to share a ballpark estimate.
In the meantime, would you like to learn more about ScienceSoft?
- 21 years in cybersecurity: check what we do.
- 4,000 successful projects: explore our portfolio.
- 1,300+ incredible clients: read what they say.

Security Gaps Most Likely to Cause HIPAA Violations
ScienceSoft's experts share issues that they most often detect in healthcare security projects and that may lead to PHI being accessed, altered, or destroyed unauthorizedly.
Cryptographic failures
Use of weak or vulnerable cipher suites, weak RDP encryption, insecure cryptographic protocols like TLS 1.0, and missing or weak data encryption at rest.
Identity and access management (IAM) flaws
Broken access control, violation of the principle of least privilege, missing two-factor or multifactor authentication.
Security misconfigurations
Insecure missing or poorly configured IDS/IPS, DLP, anti-malware, firewall, VPN, and other security tools.
Poor binary protection
Lack of protections against reverse engineering or tampering with software or firmware that handles PHI.
Input validation and sanitization flaws
Vulnerabilities that allow SQL injection, code injection, XSS, and other attacks.
Insecure software and network design
Use of vulnerable versions of software (including programming languages and third-party libraries), weak network segmentation, inefficient placement of security tools.