Vulnerability Management Services
Long-Term Protection of Your IT Ecosystem
With 36 years in IT and 22 years in cybersecurity, ScienceSoft offers end-to-end vulnerability management services to proactively identify and mitigate potential risks. We help midsize and large organizations in 30+ industries, including healthcare and finances, keep their IT environments free of security and compliance gaps.
Vulnerability management services represent a continuous process of identification, analysis, prioritization, and remediation of security weaknesses in a company's IT infrastructure and software. This proactive and consistent approach helps reliably protect an ever-changing IT environment.
Do you need vulnerability management services?
While consistent vulnerability management is part and parcel of any mature security program, it can be a lot to handle on your own. Vulnerability management will likely be a wise investment if:
- Your IT environment is growing bigger and more complicated, with the tech stack getting more diverse.
- Your company experiences regular intrusion attempts.
- Your company operates in a highly regulated field and needs to protect sensitive data.
4 Key Fields We Take Care Of
Internal procedures
- Policies: incident response plan, access control policy, remote access policy, change management policy, and more, depending on your business specifics and IT environment.
- Cybersecurity awareness among your employees.
Network defense
- Endpoints: PCs, laptops, mobile devices.
- Email services.
- Preventive and detective tools: firewalls, IDS/IPS, network access controls, DLP systems, VPNs, SIEM, IAM.
Application protection
- Web apps.
- Mobile apps.
- Desktop apps.
Data safety
- Data repositories.
- Data encryption.
- Data backup.
- Data transfer.
Applying cybersecurity measures once and forgetting about them forever is not a viable strategy. A corporate security system should be regularly monitored, assessed, tested, and improved.
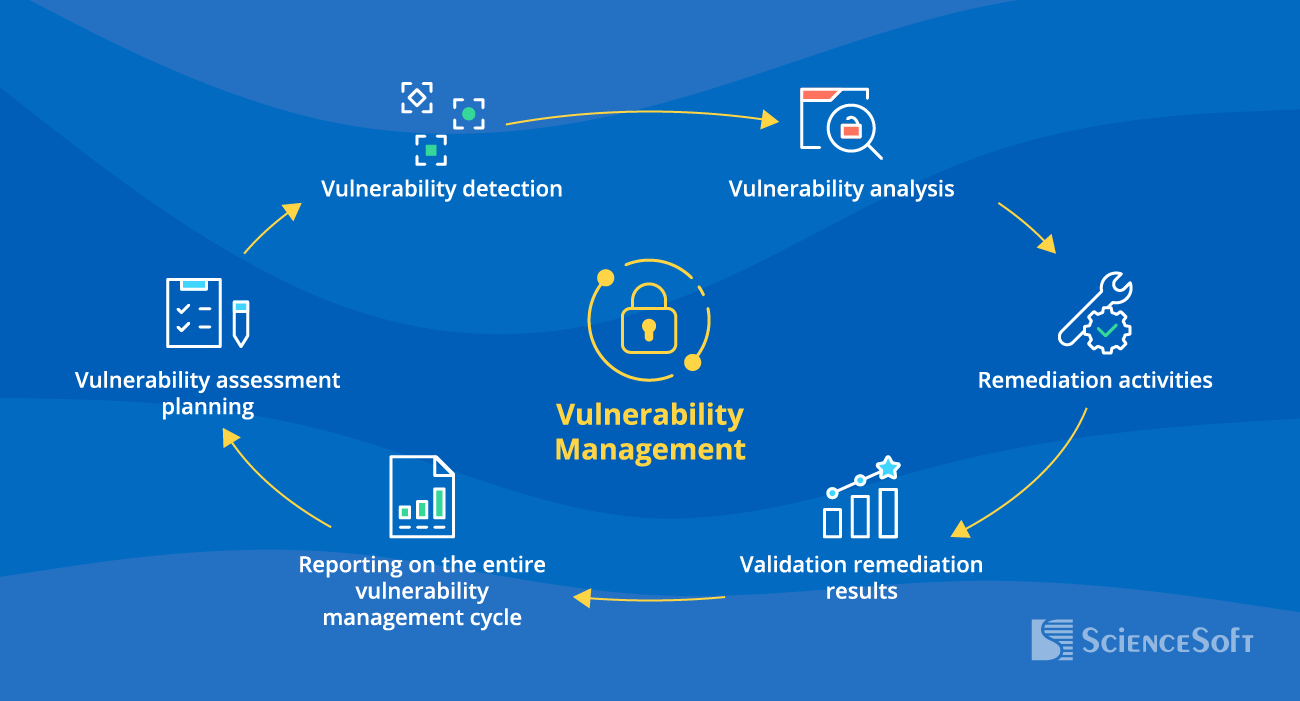
Step-by-Step Vulnerability Management at ScienceSoft
1
Planning
For each vulnerability assessment cycle, our security engineers define specific requirements and goals, scope the target IT assets, and decide on the assessment approaches and tools to be used.
2
Detection
We use different security assessment techniques to get a full view of security weaknesses in the IT assets. ScienceSoft’s experts explore every security aspect that standard checklists may miss like non-obvious, industry-specific attack vectors.
3
Analysis
Our cybersecurity experts evaluate the likelihood of vulnerability exploitation and its potential impact and classify the detected security issues by their severity.
4
Remediation
Our security engineers define and prioritize remediation steps and implements corrective measures to address the identified vulnerabilities.
5
Validation
We re-assess vulnerable assets to confirm that the detected flaws have been appropriately fixed.
6
Reporting
We prepare detailed reports that cover the vulnerability management process, including the assessment findings, actions taken, and outcomes.
Cyber Threats We Keep Away
Viruses, worms, and trojans
Ransomware
Code injections
Man-in-the-middle attacks
Spyware and keyloggers
Identity theft
Unauthorized access
Insider attacks
Compliance breaches
Tried and True Approaches We Are Confident In
ScienceSoft as a Vulnerability Management Service Provider
- 22 years in information security, a solid portfolio of completed projects.
- A structured approach to managed security services based on 17 years of ITSM experience.
- 62% of our revenue comes from long-term clients that stay with us for 2+ years.
- Experienced security engineers, compliance consultants, and Certified Ethical Hackers on board.
- ScienceSoft’s QLEAN App Suite is a finalist of the 2021 IBM Beacon Award for Outstanding Security Solution.
- A mature quality management system and full safety of data entrusted to us are proven by ISO 9001 and ISO 27001 certificates.
Common Questions About Vulnerability Management Services
How do vulnerability assessment and vulnerability management differ?
Vulnerability assessment identifies security flaws in software and IT infrastructure components at a specific point in time. It is part of a comprehensive and continuous vulnerability management process that includes analyzing, prioritizing, remedying, and monitoring emerging vulnerabilities to ensure sustained security.
How much does vulnerability management as a service (VMaaS) cost?
While VMaaS pricing varies significantly depending on the size and complexity of the IT environment and a company's specific security requirements, a typical package that includes vulnerability management with regular scans costs around $30,000–$200,000 annually. To get a precise service cost estimate, you can request tailored quotes from VMaaS providers.
What if a fixed team that provides managed vulnerability scanning service will overlook the same vulnerabilities over and over?
We use advanced automated tools and manually validate, thoroughly analyze the findings, ensuring there are no false positives or negatives. Instead of only relying on standard checklists, we apply practical knowledge of the client's sector (e.g., healthcare, banking, ecommerce) and technology specifics (e.g., medical devices, IoT, blockchain) to spot both common and hidden vulnerabilities, logic flaws, and chained exploits. So, the situation where a vulnerability gets repeatedly overlooked is highly unlikely.
Won’t the vendor get lazy and approach vulnerability management formally, thus reducing their efforts and exposing us to new threats?
We rely on a mature quality management system confirmed by ISO 9001 certificate — it enables us to consistently deliver high-quality service. We know how to work as a part of our clients’ teams and have a proven record of long-term cooperation: check out our projects that have lasted 10+ years, 10 years, 5+ years.
Stronger Together: How We Make an Invincible Team
Choose the Pricing Model that Works Best for You
Fixed price
You pay for a specified number of vulnerability management cycles a year.
Best for: Companies with well-established IT environments that want to test their cyber defense against emerging threats and reinforce their reputation as a secure business by undergoing regular checkups.
T&M
The frequency and scope of vulnerability management cycles are agreed on individually.
Best for: Companies with dynamically changing IT environments that are experiencing rapid expansion or digital transformation.
Why Does Your Business Need Consistent Vulnerability Management?
|
40K+ new vulnerabilities were reported in 2024. (CVE Details) |
44% was the increase in worldwide cyberattacks in 2024 compared to 2023. (Check Point) |
$4.88M was the average total cost of a data breach in 2024, according to IBM. |











