How Phishing Simulation Prevents Phishing Attacks
Editor’s note: The number of cybercrimes based on social engineering techniques has increased in the age of remote operations. Uladzislau introduces real examples of phishing attacks simulated by ScienceSoft’s security experts to assess the awareness level of our clients’ employees and outlines our best practices to prevent them. And if you are interested in a similar check of your corporate security level, feel free to consider our vulnerability assessment services.
Companies having effective security systems sometimes pay less attention to cybersecurity threats associated with a human factor. However, a person cannot be programmed to respond to social engineering threats in a predefined way, which is a good chance for result-driven fraudsters. Below, I describe several actual phishing attacks, which may not seem too dangerous until you find out how many people took the bait. Read on to stay cautious and learn our remediation tips.
What is phishing anyway?
Phishing is a form of social engineering fraud where attackers send an email on behalf of a service or a person familiar to a recipient. Such emails encourage users to enter their authorization data, click on a link that installs malware or provide sensitive information that will help attackers build a further attack vector.
Currently, the majority of phishing attacks in the world are targeted at organizations, not individuals. Moreover, according to the Verizon Data Breach Investigations Report, 90% of security incidents and data breaches faced by companies involve phishing.
Such attacks on an ill-prepared organization usually lead to serious financial and reputational losses, as well as to a decrease in customers' trust.
Actual Phishing Simulation Examples
A picture is worth a thousand words, so let me show two phishing attacks carried out by ScienceSoft’s cybersecurity team for a large organization working with a wealth of private information.
Case 1. Phishing request to register in an external system
We retrieved several email addresses of our customer’s financial department representatives and sent them phishing emails signed with the corporate address. In the emails we introduced a new financial reporting system and stated the need for compulsory registration in it.
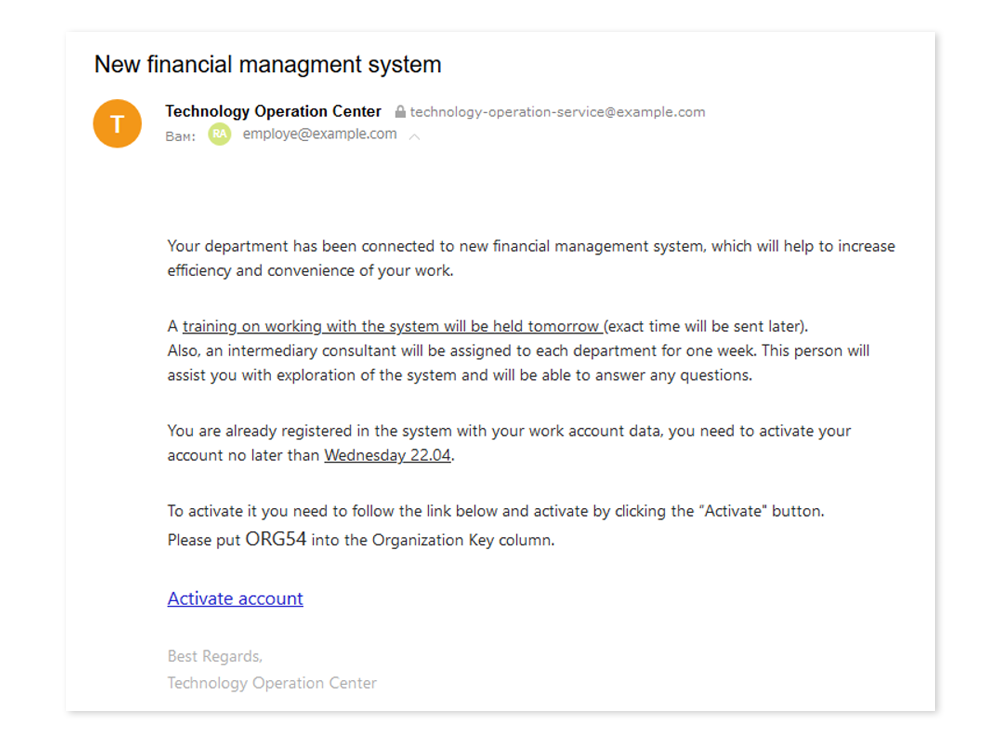
Guided by the instructions, they were invited to follow the link to the website specifically created by us and log in using their corporate email access data.
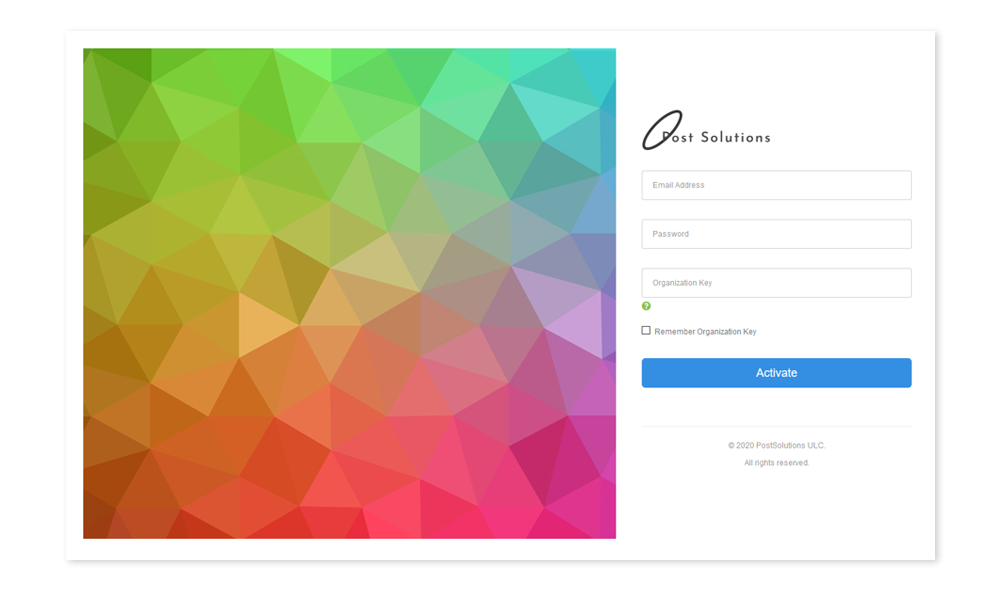
As a result of this attack, 75% of recipients clicked on the malicious link indicated in the email, 20% of them entered their authorization data, thereby giving us (potential attackers) access to their corporate email and correspondence.
Case 2. Phishing attack suggesting to resolve technical issues.
In this case, we made an exact copy of a corporate email sign-in page.
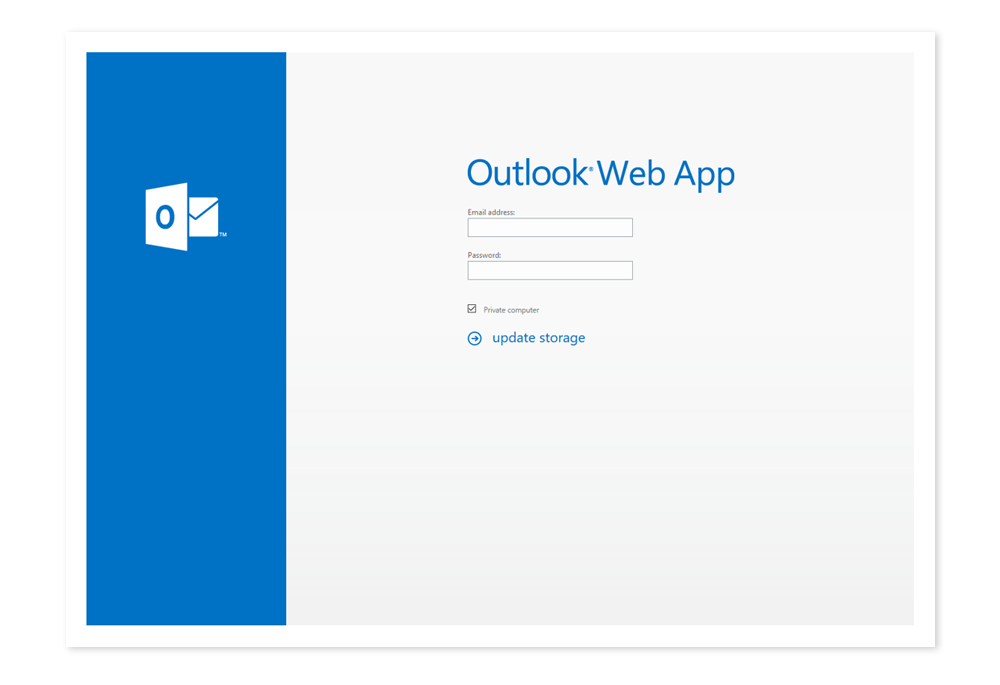
Then we sent emails to employees stating their need to reload mailbox storage as soon as possible by clicking on our link to reauthorize.
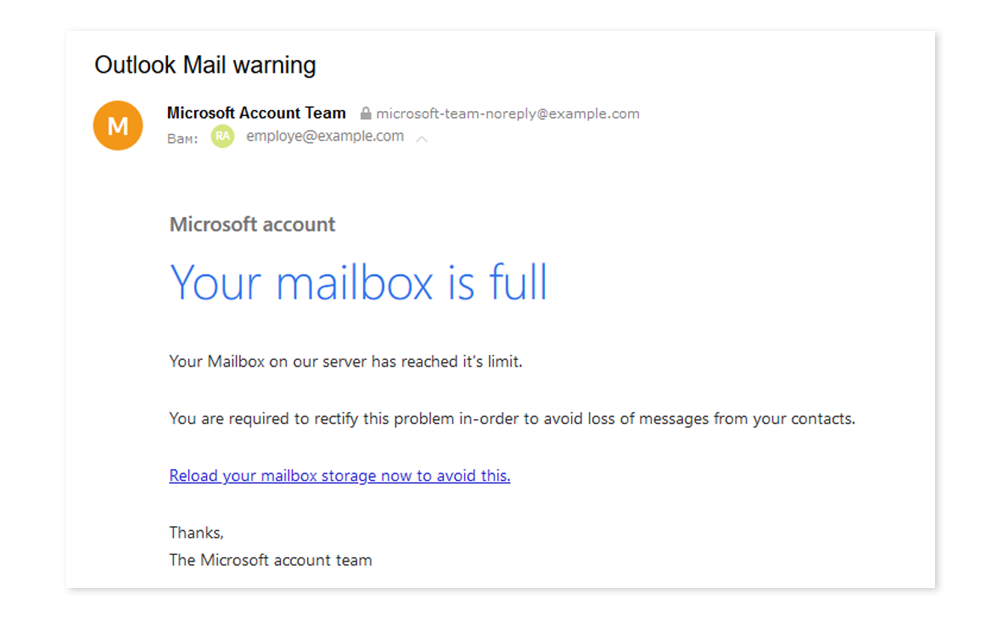
As a result, about 10% of the recipients provided us with their personal data.
Based on those “successful” results, we suggested adjustments to the customer’s access management system, held training sessions for the employees and pointed out the aspects to pay heed to when handling the incoming correspondence.
Read on to grab some useful anti-phishing techniques from ScienceSoft.
So, how to withstand phishing?
I’d like to highlight that cybercriminals carefully prepare their attacks and study information about a company and its employees so that emails do not look suspicious. For that, attackers hold by several rules:
- A sender of such a phishing email should inspire confidence.
- The email should contain reliable facts.
- A request in the email should be logical and address a specific person or a group of people.
In such circumstances, to successfully withstand phishing attacks against your company, I advise you to follow some well-proven recommendations below.
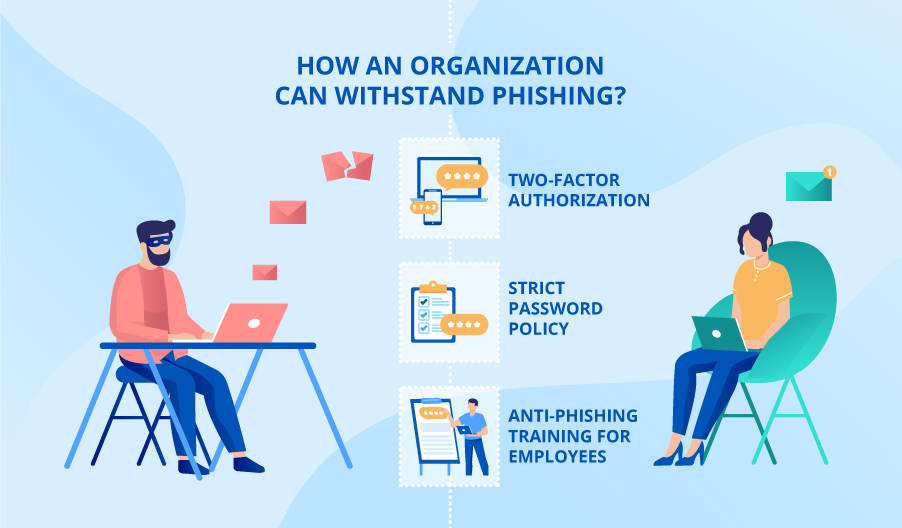
In addition to phishing simulation, anti-phishing measures for an organization shall include:
- Introduction of two-factor authorization. Two-factor authentication is an added security level, where a user must provide extra authentication evidence to gain access, for example, a one-time code messaged to a user’s cell phone by a sign-in system.
- Strict password policy. Prohibit using one password for multiple applications.
- Anti-phishing training for your employees. Organize anti-phishing training to educate your employees on how to recognize phishing emails and where to report them.
For users:
- Check the source of each email you receive. Some malicious emails may have the outbound address resembling popular or credible ones, but after taking a closer look, you may notice mistakes intended to mask fraud.
- Do not follow any website via a direct link in an email. Hover and check whether the URL of the link somehow correlates with the pretended sender or the contents of an email. Even if the link doesn’t raise your suspicions, avoid clicking it – type the link in the address line of your browser instead: malicious links may contain executable scripts you would never like to activate.
In case of emergency, dial S for Security
Attackers use subtle practices to sneak into your system. They aggregate corporate data as well as personal data of your employees to commit successful phishing attacks causing substantial damage to your company via disclosure of confidential information, blackmailing, data loss, etc. That’s why we at ScienceSoft always prioritize preventive practices over reactive measures in what pertains to social engineering threats. Be welcome to contact us for a full-fledged social engineering assessment of your organization.

