Cloud Security Assessment
Evaluating and Improving Cloud Cyber Defense
In IT security since 2003 and in cloud services since 2012, ScienceSoft helps enterprises and SaaS providers ensure full protection of their cloud environments. Equipped with advanced tools, cross-industry expertise, and testing methods that go beyond standard checklists, we provide a clear and accurate picture of your cyber resilience without false positives or missed threats.
Cloud security assessment involves analyzing cloud assets and processes to uncover potential vulnerabilities. It results in a customized remediation plan to address security gaps and establish robust cloud security controls.
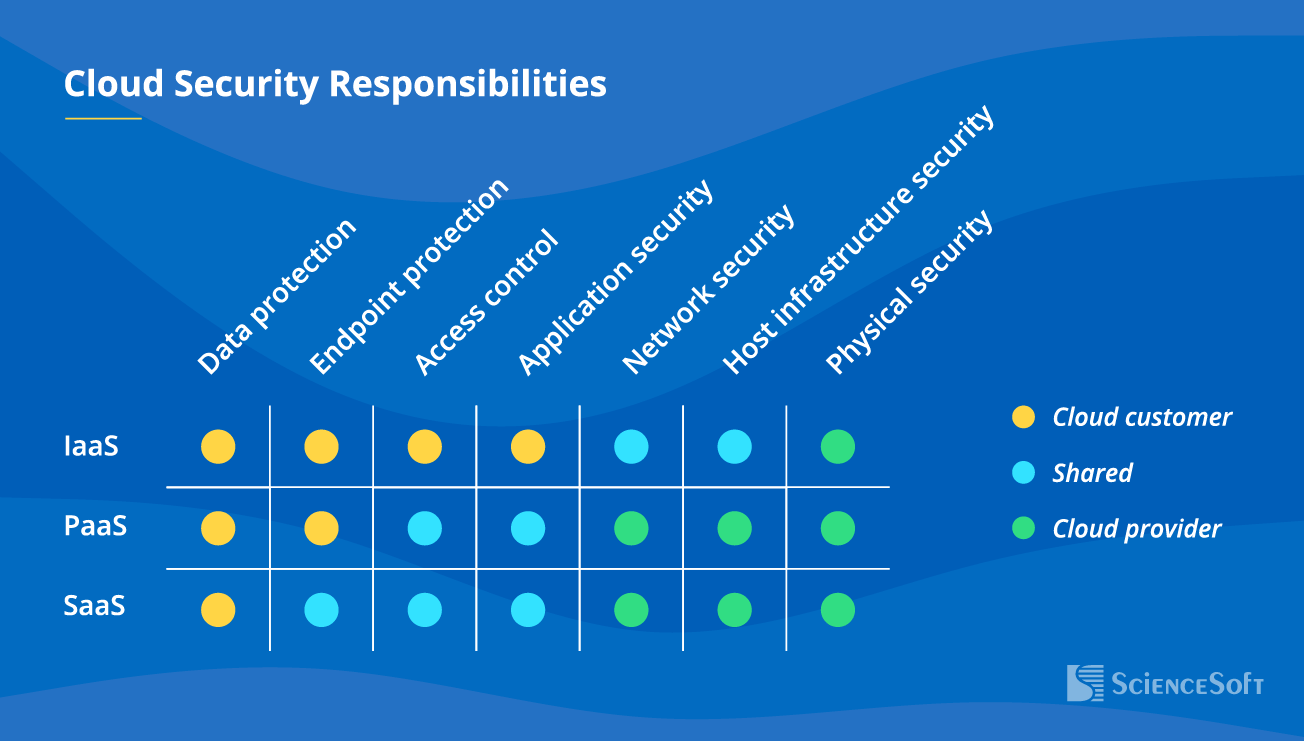
Know Your Cloud Security Responsibilities
When it comes to cloud, security responsibilities are usually shared between the customer and the cloud provider. The rules of who is in charge of what will depend on the chosen service model: with more flexibility for the customer comes greater security and compliance responsibility. SaaS is the easiest to manage since the cloud vendor is largely in charge of your security, but with PaaS and especially IaaS, you will be in charge of your own cyber defense.
When assessing your individual case, we define the cloud environment components within your responsibility to evaluate and improve their security as well as help achieve compliance with relevant security standards.
Make Sure All Cloud Security Controls Are in Place
Relying on ISO 27001, ISO 27002, NIST SP 800-53, and cloud-specific best practices, ScienceSoft's team helps implement optimal preventive and detective security controls.
Secure Your Cloud Apps Inside Out
We check your cloud app from different angles to find any loopholes that potential attackers may use. Cloud application security assessment typically includes:
SAST — automated source code review
We analyze the code of your cloud app to reveal the existing vulnerabilities that hackers can find and exploit at any moment.
DAST — application penetration testing
We test out potential scenarios of real-world hacker attacks and estimate their consequences for your cloud app.
Security patching
We apply the missing security updates to protect your apps from known vulnerabilities.
AWS, Azure, GCP Security Comparison
Cloud service providers offer ever-evolving portfolios of security services to cover their customers’ compliance and security needs: identity and access management, web and email security, monitoring and threat detection, data loss prevention, compliance management, and more. Major cloud providers share documented guidance on their best security practices: AWS Well-Architected Framework Security Pillar, Azure Security Benchmark, and Google Cloud Security Foundations Guide.
ScienceSoft’s consultants are ready to navigate you through the advantages and challenges of each cloud provider to help you leverage the best security opportunities available.
AWS
- Mature documentation on security and compliance services.
- Relatively secure default settings (e.g., restricted access to the network by default).
- Enhanced security due to isolated accounts. If an attacker hacks one AWS account within your system, they won’t be able to access other accounts.
- Granular IAM.
- Highly customizable security groups.
- Complicated and decentralized security management at the enterprise level because of account isolation.
Azure
- Unified management of authorization and permissions.
- Built-in privileged access management (PAM) functionality.
- Centralized log monitoring.
- Less secure default configurations compared to AWS (e.g., open ports in a newly created virtual network).
- Poor documentation making security services difficult to understand and efficiently configure.
Google Cloud Platform
- The security of default configurations is acceptable (on par with AWS).
- Easy configuration of security services.
- Fewer advanced security features compared to AWS and Azure.
- It is harder to find experienced GCP security specialists as the service is not as widely adopted as AWS or Azure yet.
Why Choose ScienceSoft for Your Cloud Security Assessment
- Since 2003 in IT security, a solid portfolio of cybersecurity projects.
- Since 2012 in cloud services, vast experience with AWS, Azure, Google Cloud.
- Microsoft Solutions Partner, dedicated Azure consulting services.
- AWS Select Tier Services Partner, dedicated AWS consulting services.
- ISO 9001-certified mature quality management to guarantee smooth cooperation and value-driving results.
- 100% security of our clients' data ensured by ISO 27001-certified security management system.
Our Clients Say
ScienceSoft’s cybersecurity experts helped us build a plan for two penetration tests: (1) review of our corporate networks and (2) review of our cloud AWS services. In their review of our AWS services (Identity and Access Management (IAM), VPC Service Controls, AWS Config, CloudTrail, etc.) they checked the security of cloud environment configurations and our corporate data stored in the cloud and the effectiveness of our security practices in AWS. After that, we received another report with clear recommendations on how to enhance the cybersecurity of our AWS environment.
Joel B. Cohen, President, USPlate Glass Insurance Company

Enhancing Cloud Cyber Resilience: Success Stories by ScienceSoft
How Our Cloud Security Assessment Unfolds
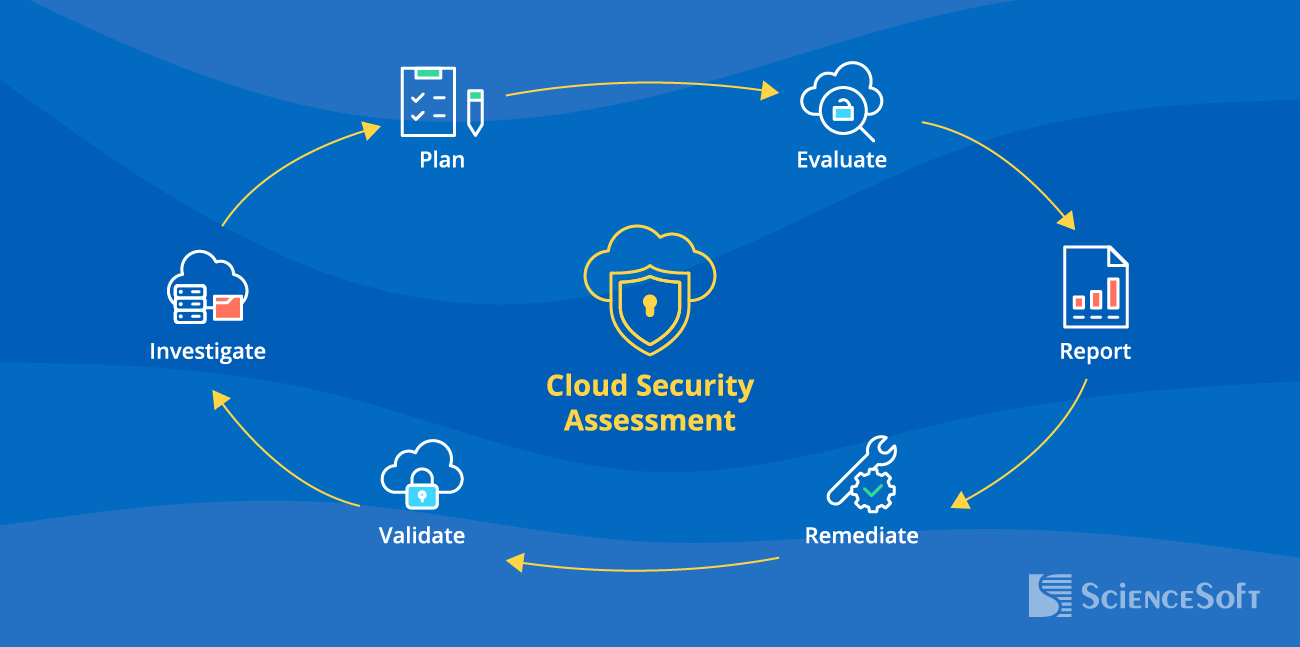
While the scope and the flow of a cloud security checkup is adjusted to the client's specific needs, a full-cycle security assessment by ScienceSoft typically includes the following steps:
1. Initial investigation
- Discussing the client's cloud security concerns, goals, time and budget expectations.
- Analyzing the client's cloud services, applications, and data stored within the cloud environment.
It is important to map out dependencies between different cloud services and resources to clearly understand how they interact. It may help reveal hidden vulnerabilities and evaluate the potential impact of a security breach more accurately. As a result, you'll be able to make better decisions about efficient risk mitigation strategies for your cloud environment.
2. Planning
- Creating a customized assessment checklist covering such aspects as identity management, encryption, monitoring, network security, data backup, and more.
- Defining the methodology and optimal cloud security assessment tools.
3. Execution
Depending on the assessment scope, it may include:
- Auditing the cloud security controls in place.
- Vulnerability scanning and penetration testing.
- Cloud compliance evaluation.
- Questionnaires and social engineering testing for the staff, and more.
Attackers can exploit the ability of cloud resources to scale up and down based on demand. This means they can launch attacks that lead to excessive consumption of cloud resources, resulting in increased costs for their victims. Additionally, they may use these dynamics to overwhelm the victim's defenses and sneak into the cloud environment undetected. Traditional static security testing methods struggle to identify these threats. That's why it is essential to incorporate a behavioral approach in penetration testing.
4. Reporting
- Delivering a comprehensive report on the assessment process, findings, and the required corrective measures.
- Providing an executive summary.
5. Remediation
- Implementing the missing controls or tuning the ones in place to achieve maximum protection of the cloud assets.
- Validating the results of remediation activities.
Needs Covered with a Professional Cloud Security Assessment
Security of complex cloud environments
Cloud infrastructures are dynamic and complex, with numerous services, configurations, and access points. While assessing your organization's cloud landscape, ScienceSoft's experts look for cloud-native threats like container vulnerabilities, API security concerns, serverless function weaknesses, and misconfigured IAM roles.
Transparency of cloud responsibility
Within cloud security assessment, our team will clearly outline which security aspects lie within your organization's responsibility and which are covered by your cloud service provider.
Full compliance
During the assessment, we reveal the gaps that can result in non-compliance with applicable regulations (HIPAA, PCI DSS, GDPR, etc.). As we reflect the needed corrective measures in the remediation plan, organizations can tackle these issues proactively.
Optimized security spending
Be sure to get professional remediation guidance from us. We prioritize the identified vulnerabilities based on their criticality and recommend cost-effective security measures that align with your organization's cloud resources and processes.
Security Assessment vs. Security Risk Assessment in Cloud Computing
Security assessment and security risk assessment for cloud computing are often used interchangeably. However, these activities differ in their objectives and scope. Security assessment evaluates the existing security measures. Cloud security risk assessment focuses on identifying and proactively managing potential risks and vulnerabilities associated with cloud computing. Whatever service you need, ScienceSoft can provide both.
Make Sure Your Cloud Security Is Not an Afterthought
While cloud computing makes digital infrastructures more agile and less costly, it also brings new security challenges that cannot be overlooked.
|
$5.17M was the average cost of data breaches solely involving public clouds, making it the most expensive type of data breach. (IBM’s Cost of a Data Breach Report 2024) |
47% of PwC’s 2024 Global Digital Trust Insights respondents named cloud security as the No. 1 cyber risk concern. |
|
28% of security incidents were caused by compromised cloud credentials, making it the second most common initial access vector after phishing. (2024 IBM X-Force Cloud Threat Landscape Report) |
65% of organizations experienced a cloud security incident in 2024. (Check Point's Cloud Security Report 2025) |






