ATM Security & Network Protection
ATM security comprises the set of measures to protect ATMs against cyberattacks and hacks. In cybersecurity since 2003 and specializing in the banking and finance industry, ScienceSoft renders ATM security services to prevent our clients’ financial losses, reputation damage, and client churn.
ATM physical protection alone fails to provide an adequate security level.
Why ScienceSoft?
- Since 2003 in cybersecurity.
- A competent team of IBM Certified Security Specialists.
- A solid portfolio of cybersecurity projects in BFSI, Healthcare, Public Sector, Retail, Telecom, Oil & Gas and other industries.
- Our expertise covers security information and event management (SIEM), identity and access management, penetration testing, as well as development and maintenance of ScienceSoft’s proprietary QLEAN for QRadar.
- ScienceSoft’s fraud protection service ensures identification of more than 40 fraud patterns, including unauthorized software running on ATM.
- Mature quality management system confirmed by the ISO 9001 certification allowing to implement projects fully meeting customers' quality, time, and budget expectations.
- Guaranteed security of the customers’ data we access, proved by ISO 27001 certification.
What We Offer
ScienceSoft’s information security consultants are ready to address your ATM network security challenge with the approach customized to the security needs of your ATM network.
ATM network audit
We carry out an in-depth infrastructure analysis of your ATM network service to identify flaws in design leading to insufficient network security level. One of the most frequent pitfalls is the absence of adequate ATM network coverage by a security information and event management (SIEM) system.
ScienceSoft’s security intelligence services include IBM® Security QRadar® SIEM system implementation and fine-tuning. Our IBM certified SIEM consultants are ready to design and deploy the solution, whose intelligence provides real-time visibility of the entire ATM network infrastructure.
Incident data collection and analysis
ScienceSoft’s information security consultants cooperate with your security team to collect data about reported ATM security incidents. Armed with professional experience and best practices of ATM protection, our consultants analyze security incident history to improve security level of ATM network design.
Security assurance of ATM network design
We suggest how to improve the existing design of your ATM network to make it security breach resistant.
ATM protection checklist
Recommendations on ATM security improvement are supported by an ATM protection checklist – a document with essential configurations to be set on each ATM network server. The document suggests how to fine-tune your ATM network, so that QRadar SIEM system could collect logs from crucial log sources, which is the cornerstone of a well-timed threat detection.
We understand that successful banks extend their ATM network year by year, so our information security consultants enhanced an audit baseline with instructions on how to configure additional ATM endpoints to make them an integral part of the network.
QRadar custom correlation rule creation
ScienceSoft’s SIEM consultants have created four QRadar correlation rule categories which address the existing and potential threats to your ATM network. Correlation rules allow monitoring of all the entries into the network, launching of unsolicited services, software integrity, antivirus feed and DMZ router logs and flows.
Correlation rule categories
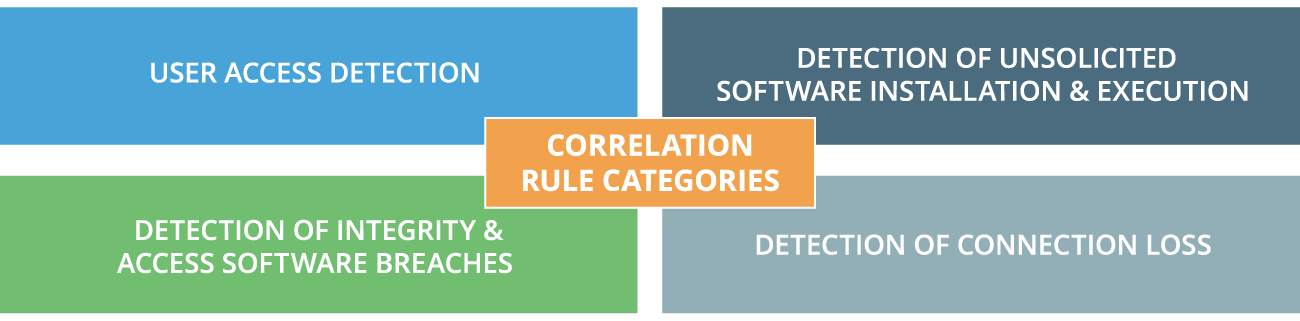
- User access detection (to monitor every privileged access to ATM endpoints).
- Detection of unsolicited software installation and execution (to monitor privileged users’ attempts to install and execute the software that is not allowed).
- Detection of integrity and access software breaches (to monitor digital signature validation in software components; to detect the instances of unauthorized access to ATM network via non-standard communication exploits between software components).
- Detection of connection loss (to spot the cases of suddenly losing connection with ATM endpoints).

