Code Review Services
Spotting Imperfections, Driving Improvements
In software development since 1989, ScienceSoft offers all-around code review services to help improve all aspects of code quality: from clarity and maintainability to security and compliance.
Code review services involve manual and/or automated examinations of application source code, performed by independent IT professionals able to identify the flaws that can compromise code quality and security. Expert code review helps improve source code performance, clarity, scalability, and maintainability as well as fortify software against cyberattacks.
The Scope of Our Code Review Services
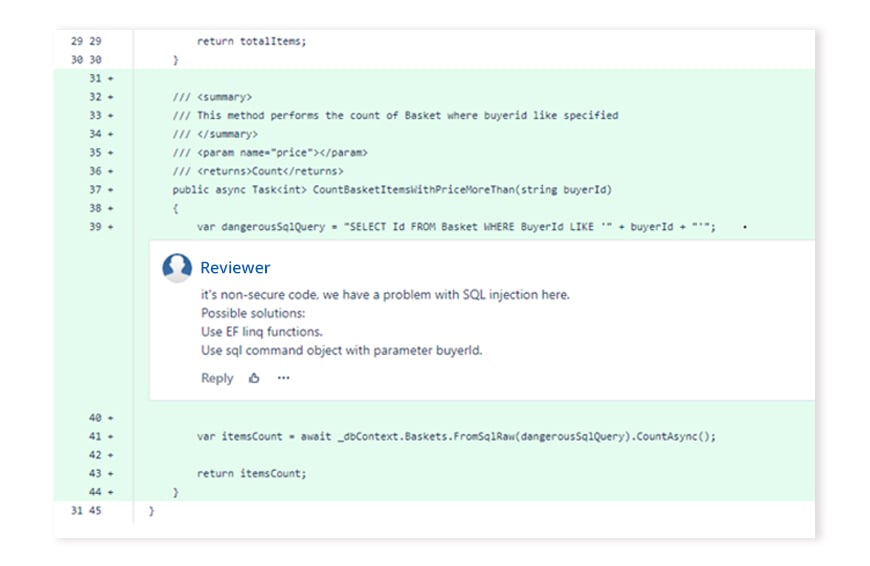
SAST – automated security code review
We reveal:
- Encryption errors: weak encryption algorithms or strong encryption algorithms with weak implementation (e.g., insecure key storage).
- Code injection vulnerabilities.
- XSS (cross-site scripting) vulnerabilities.
- Buffer overflows: more data is put into the buffer than it can handle.
- Race conditions: performing two or more operations at the same time.
Manual security-focused code review
We check:
- Auditing and logging mechanisms.
- Input/data validation mechanisms.
- Impersonation/delegation mechanisms.
- Session management.
- Communication security.
- The security of connection strings.
- Input/output operations security.
- The presence of serialization filtering.
- Reflection mechanisms.
- The presence of obfuscation.
- If the code is thread-safe.
See more
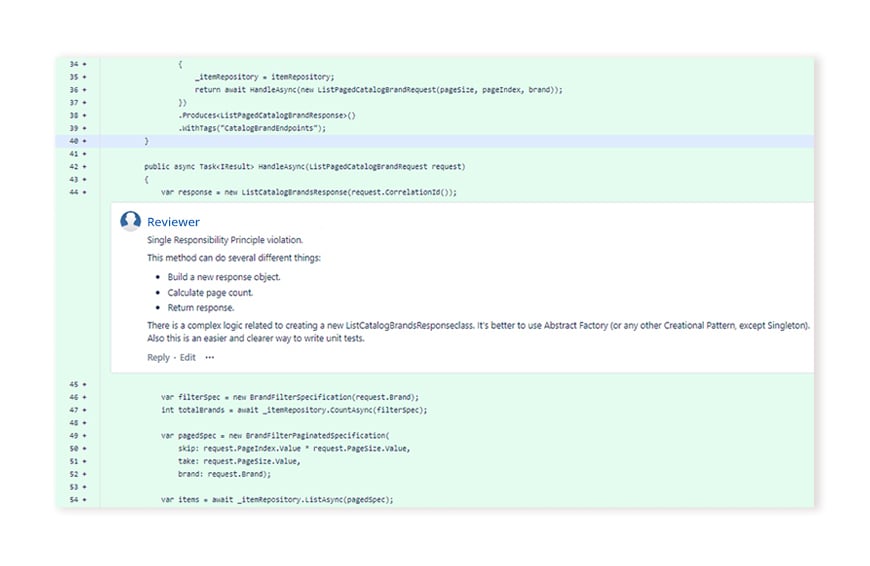
All-around code review
In addition to SAST and manual review of code security, we check:
- If descriptive names for code variables are in place.
- If comments about what particular code functions and methods do are present.
- If documentation on what the whole code does and what its dependencies are is in place.
- If the developers can take advantage of ready frameworks and reusable components to get work done faster.
- If the practice of splitting code into shorter units is observed.
- If the code is portable.
- If effective version control is implemented.
- If linter tools (SonarQube, ESLint) are used.
- If exception-handling mechanisms are effective.
- If the required security mechanisms are in place, and more.
Why ScienceSoft
Decades-long experience:
- Since 1989 in software development and IT consulting, over 4,200 success stories across over 30 industries.
- Since 2003 in information security, a solid portfolio of completed projects.
- Since 2013 in DevOps and CI/CD.
Competent code reviewers:
- Senior developers proficient in a broad variety of programming languages and frameworks.
- Seasoned security engineers and compliance consultants.
- Proficiency in static code analyzers (e.g. SonarQube, Roslyn), database profilers (e.g. Microsoft SQL Server Profiler), memory and performance profilers (e.g. dotTrace, dotMemory).
- Adherence to OWASP Application Security Verification Standard.
Guaranteed service quality:
- A mature quality management system confirmed by ISO 9001 certification.
- Complete security of the sensitive data we access proven by ISO 27001 certification.
- A leading outsourcing provider recognized by IAOP.
Our awards, certifications, and partnerships
Do We Share the Same Values?
Result-oriented approach
To ensure that you receive tangible results, we base our reviews on code quality KPIs: e.g., Cyclomatic Complexity, Maintainability Index for manual reviews. We also help you improve project-level KPIs, such as cycle time, deployment frequency, and more.
Cost efficiency
We analyze your unique needs, time and budget constraints to suggest the approach (e.g., manual or automated) that offers the best benefit-cost ratio for you. In needed, we are ready to enhance the project team with software architects, compliance consultants, PMs, or any other IT talents to provide the best results for you.
Knowledge transfer
Dedicated to fostering our clients’ digital success, we are eager to share our software development expertise and help your team members adopt best coding practices.
Building solid business relationships
With 62% of our income coming from the customers that have been with us for 2+ years, we know the value of long-term cooperation. We are ready to stay with you as a tech partner for as long as you need and offer flexible SLAs.
Code Review as a Service: Get Exactly What You Need
Automated code review
To offer quick and cost-efficient code review that still yields highly accurate results, we combine automated code scanning with manual validation of the findings.
Security-focused manual code review
Examining the source code line by line, we provide deeper insight into the root cause of your code issues and take into account the security of your architecture and data flow.
All-around code review
To deliver holistic improvements to your code quality and coding practices, we are ready to conduct continuous code review throughout the SDLC (ad hoc and peer review, walkthrough, inspection) or provide one-time/periodic code audit.