MITRE Windows Integration App
MITRE ATT&CK tactics for Microsoft Windows by ScienceSoft are based on logs provided by properly configured Microsoft Sysmon tool.
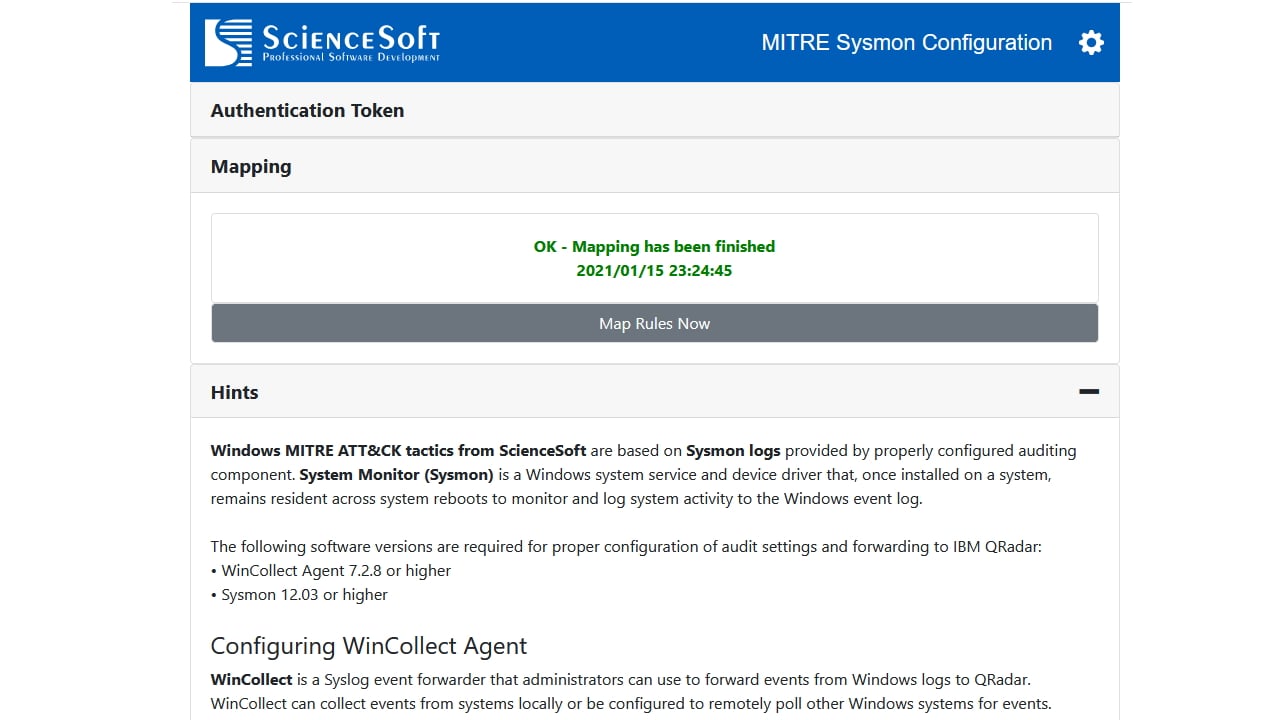
System Monitor (Sysmon) is a Windows system service and device driver that, once installed on a system, remains resident across system reboots to monitor and log system activity to the Windows event log. It provides detailed information about process creations, network connections, and changes to file creation time.
By collecting its events into the SIEM and subsequently analyzing them, you can identify malicious or anomalous activity, and understand how intruders and malware operate on your network.
While being thoroughly tested and tuned, some rules are disabled by default to prevent potential false-positives in the production SIEM environment, so make sure to enable them after configuring Sysmon.
The rules can be easily mapped to MITRE Techniques using QRadar Use Case Manager.
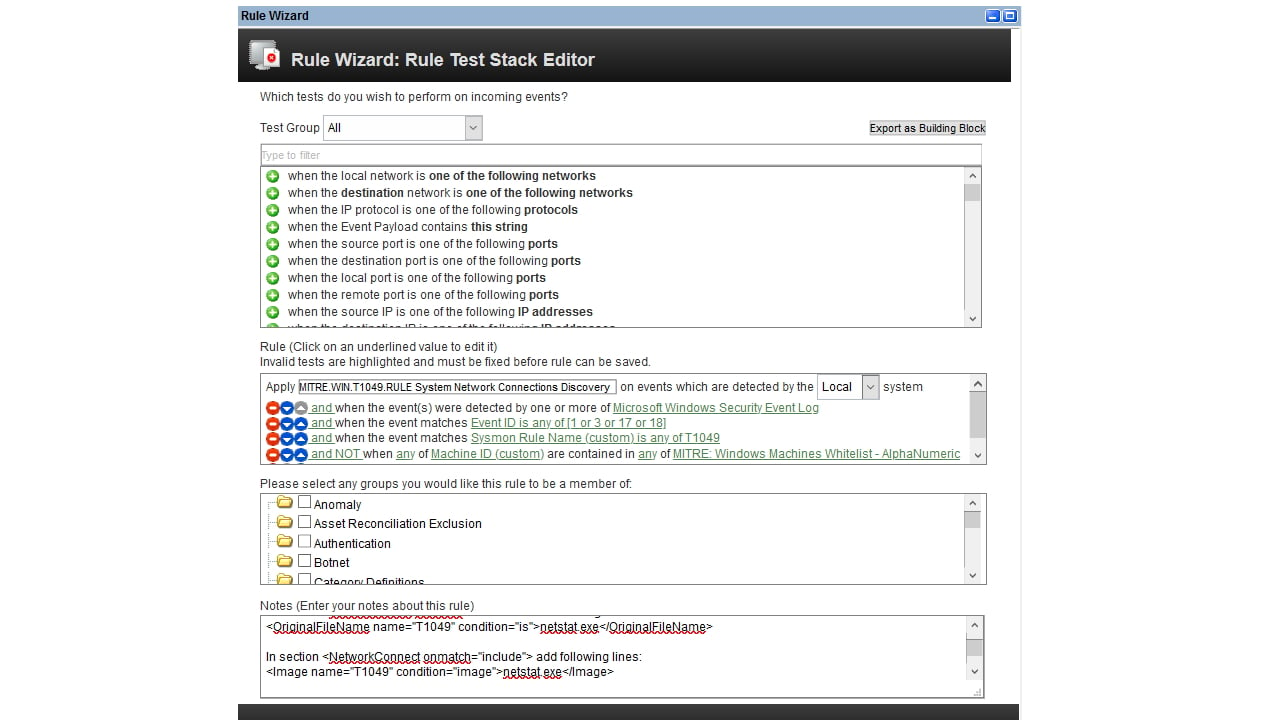
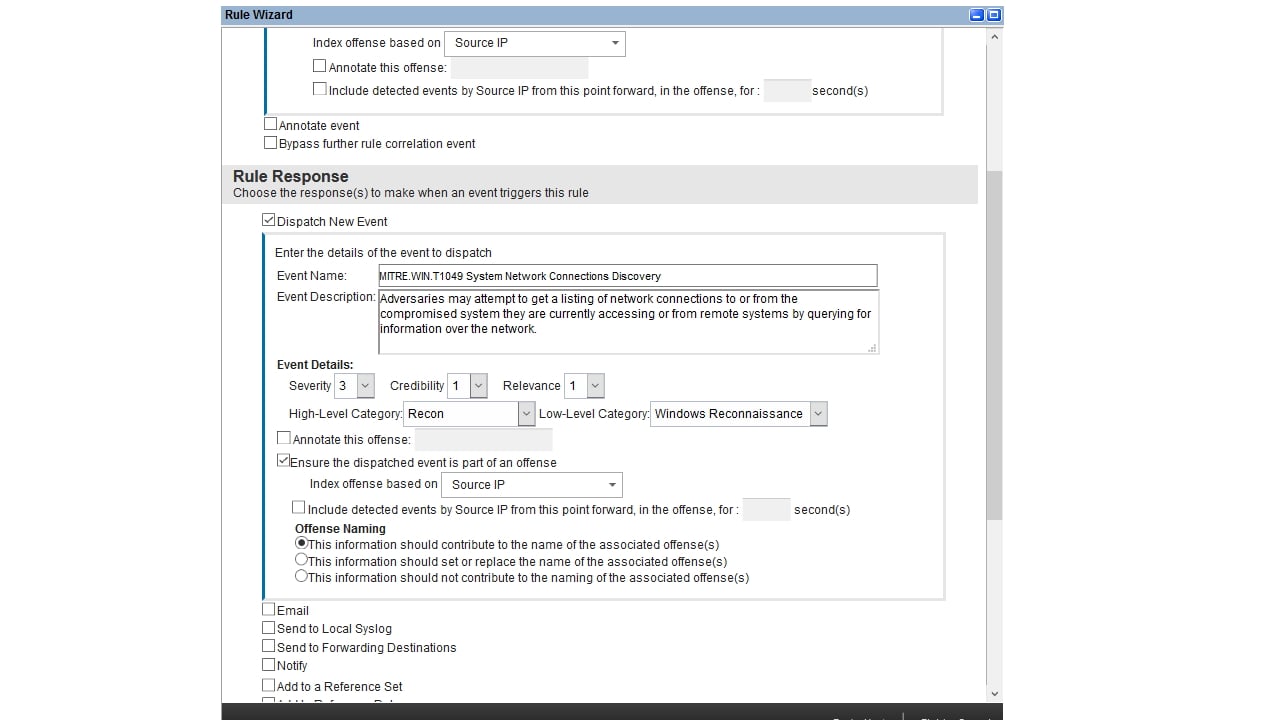
The app includes detailed instructions and prepared configuration files to properly set up Sysmon and WinCollect services on target systems.
QRadar Native Alternatives
There is no such native functionality in QRadar. All correlation rules must be developed and corresponding configuration of target systems must be investigated and performed manually.
License
MITRE Windows Integration App is a commercial application by ScienceSoft with some of its functionality available for free. The free version contains 78 correlation rules whereas the paid one provides 155 tactics.
IBM App Exchange
MITRE Windows Integration App is officially available at IBM Security App Exchange. Please, follow the link to download it now.
