Network Vulnerability Assessment
Protect Your Network from Cyberattacks
Since 2003, ScienceSoft has been providing vulnerability assessment and management services to help companies locate and mitigate network vulnerabilities. Using a combination of scanning tools and expert manual validation, we provide an accurate picture of the cybersecurity posture, with no false positives.
Network Security Vulnerability Assessment: Summary
Network vulnerability assessment includes scanning for, detecting, and analyzing security vulnerabilities within a corporate network infrastructure and aims to ensure its resilience to cybersecurity threats.
It is required to carry out vulnerability assessment of the network to comply with the majority of regulatory standards (HIPAA, PCI DSS, etc.). Usually, assessment is followed by network penetration testing to exploit identified vulnerabilities and define the most probable attack scenarios.
This engagement may take from 3–4 days (for a small network) to 2–3 weeks (for midsize and large networks). It requires a team of a lead security engineer and a security engineer, and its cost starts from $5,000. Use our cost calculator to get a free ballpark estimate for your case.
ScienceSoft’s security experts help midsize and large companies evaluate network security and unearth present security flaws. We can define the nature and criticality of network vulnerabilities and offer a remediation plan.
Risks of Network Security Flaws
Vulnerabilities in a network may enable cybercriminals to launch a variety of attacks to gain partial or full control of your IT assets.
Malware
Man-in-the-middle attacks
Brute-force attacks
Insider threats
Advanced persistent threats
As a result, they may disrupt your IT operations and damage or misuse your sensitive data. The risks of neglected network vulnerabilities include:
- Operational downtime.
- Financial losses.
- Litigations.
- Reputational damage.
According to security best practices, a company should undergo network vulnerability assessments quarterly. In case of strict compliance requirements, it may be necessary to scan your network monthly or even weekly. Also, you should consider vulnerability assessment after introducing any significant changes to the network: e.g., adding or removing critical hardware and software components. Our cybersecurity consultants warn that if you neglect proper vulnerability assessment for longer than a year, you are likely to become an easy target for hackers.
Network Vulnerability Assessment Methods
Depending on your network vulnerability testing needs, we apply the black-box, white-box, or gray-box approach.
Black-box
Scanning for vulnerabilities without any information on a target network. The external network perimeter is a starting point for scanning.
Assessing the network vulnerability ‘from the inside’ (having all the knowledge about the network).
Searching for vulnerabilities in the network, having some information about it (e.g., user login details), but without access to the entire network.
Network Vulnerability Assessment Checklist
Use this checklist to determine whether your existing network defenses meet today’s security standards and identify gaps that warrant remediation.
Have you implemented role-based access control to ensure that the users only have access to the network resources necessary to perform their tasks?
Are there strong authentication measures, such as complex passwords and multi-factor authentication (MFA), to control access to network resources?
Are critical assets, including sensitive data, isolated in separate network segments with increased security?
Is a demilitarized zone (DMZ) set up properly and isolated from the internal network?
Have strong encryption protocols been implemented to protect client-server communication?
Do you use a VPN for a secure connection between remote devices and your central network?
Do you have properly configured firewalls to control network traffic?
Is anti-malware installed across the network devices?
Do you use email security solutions for email encryption and malware scanning, spam filtering, etc.?
Have you implemented efficient network monitoring and traffic analysis tools (e.g., IDS/IPS, SIEM)?
Is network hardware and software regularly patched and updated?
Do you perform regular network vulnerability assessments and pentests?
Does your organization provide consistent training to educate employees about network security threats and ways to handle them?
Have you assessed the cyber resilience of your staff through social engineering testing?
Oops...
Sorry, we can't provide the results, unless you answer the questions.
Your network security level is high
Your adherence to best security practices is impressive. Keep up the good work! ScienceSoft's security experts are ready to check your network for hidden vulnerabilities and offer advanced measures to keep your assets hack-proof.
Your network security level is medium
Your cybersecurity efforts are showing positive results! However, there is room for further improvement. Turn to ScienceSoft, if you want to strengthen your network protection quickly and effectively, without unnecessary expenses.
Your network security level is low
It's time to prioritize your cybersecurity. If you need field-tested advice, efficient tools, and enthusiastic security team to bolster your network protection, ScienceSoft has it all.
Steps to Perform Network Vulnerability Assessment
ScienceSoft plans vulnerability assessment of a network according to its size and complexity and size and the type of the target environment (production, development, etc.). You are welcome to check out our sample plan below and use it as your network vulnerability assessment checklist.
1.
Network vulnerability scan planning and design
- Defining the assessment goals: e.g., network segmentation check, malware scanning, preparing for HIPAA compliance audit.
- Creating a list of the network segments and software to be assessed.
- Selecting a vulnerability scanning tool that can be configured to bypass specific network firewall rules and restrictions.
- Choosing between an external vulnerability scan (for the part of the network exposed to the internet) and an internal vulnerability scan (for the internal corporate network).
- Scheduling the vulnerability scan (usually for non-business hours).
2.
Configuring the scan
- Defining target IPs by specifying the hardware or software they belong to.
- Adding the list of target IP addresses to the vulnerability scanning tool.
- Scanning the network for open ports and defining port ranges and protocol types (TCP or UDP).
- Setting up the aggressiveness level of the scan, its duration, and completeness notifications.
We typically set up scanning aggression at the medium level. It helps avoid the disruption of network operations, as a high scanning aggression level requires increased consumption of network resources.
3.
Scanning for vulnerabilities
- Checking the target network components with a manually tuned automated scanning tool.
4.
Analysis of the scan results
At this stage, we perform manual analysis of the scan findings:
- To filter out false positives and validate the identified security vulnerabilities.
- To analyze root causes and potential impact of the found vulnerabilities.
We recommend reaching out for penetration testing to see whether a real-life attacker can exploit the detected vulnerabilities.
5.
Reporting the vulnerabilities discovered
We deliver an executive summary with the project highlights and a final report, which contains:
- A list of detected vulnerabilities with their description and classification by their criticality.
- Corrective measures for each flaw.
- The assessment methodology and tools.
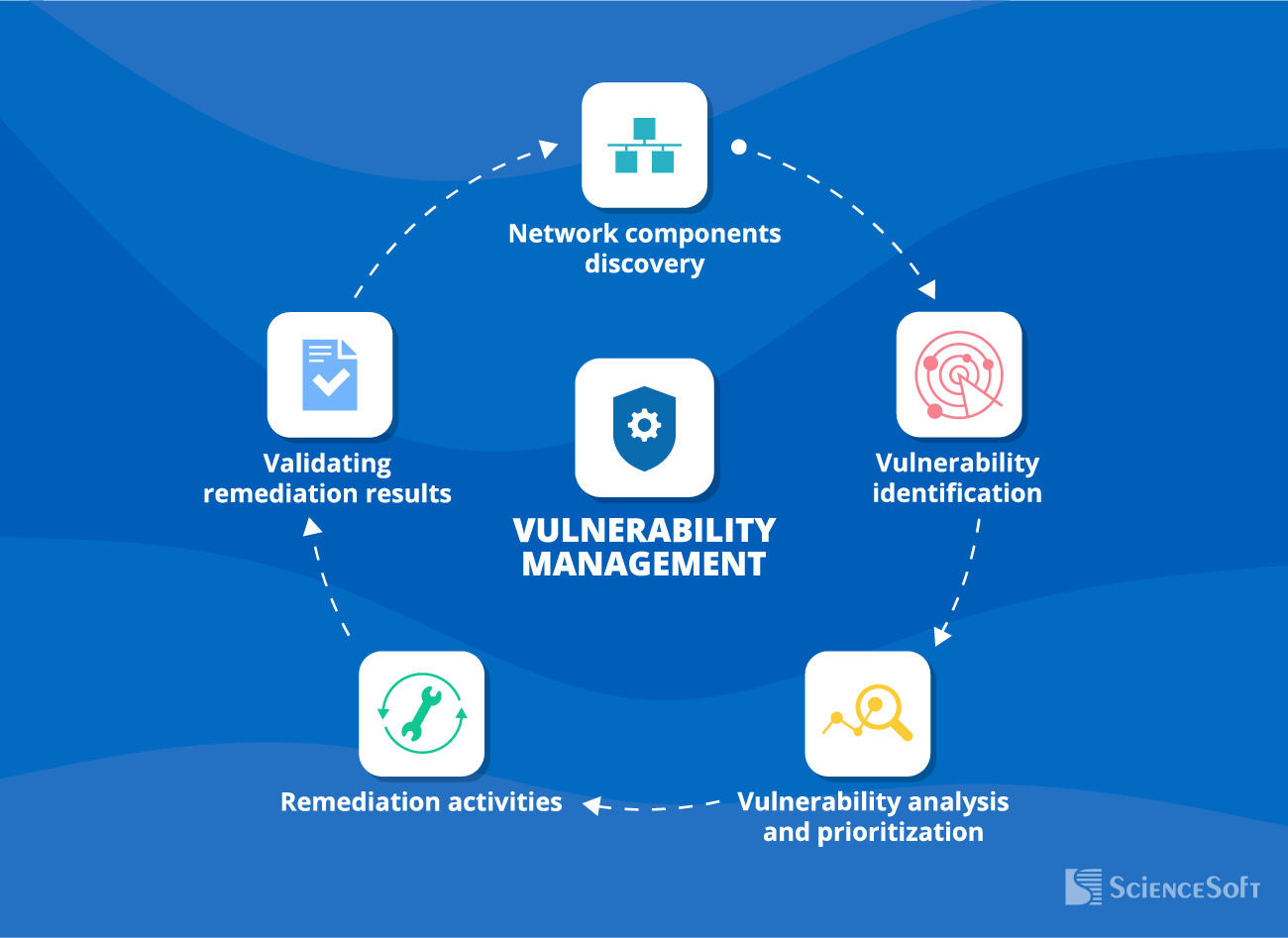
Network Vulnerability Management Steps
An integral part of a sound security strategy, network vulnerability management is a continuous process of keeping an up-to-date inventory of network assets, assessing network security, and eliminating vulnerabilities.
Top Network Vulnerabilities and Ways to Handle Them
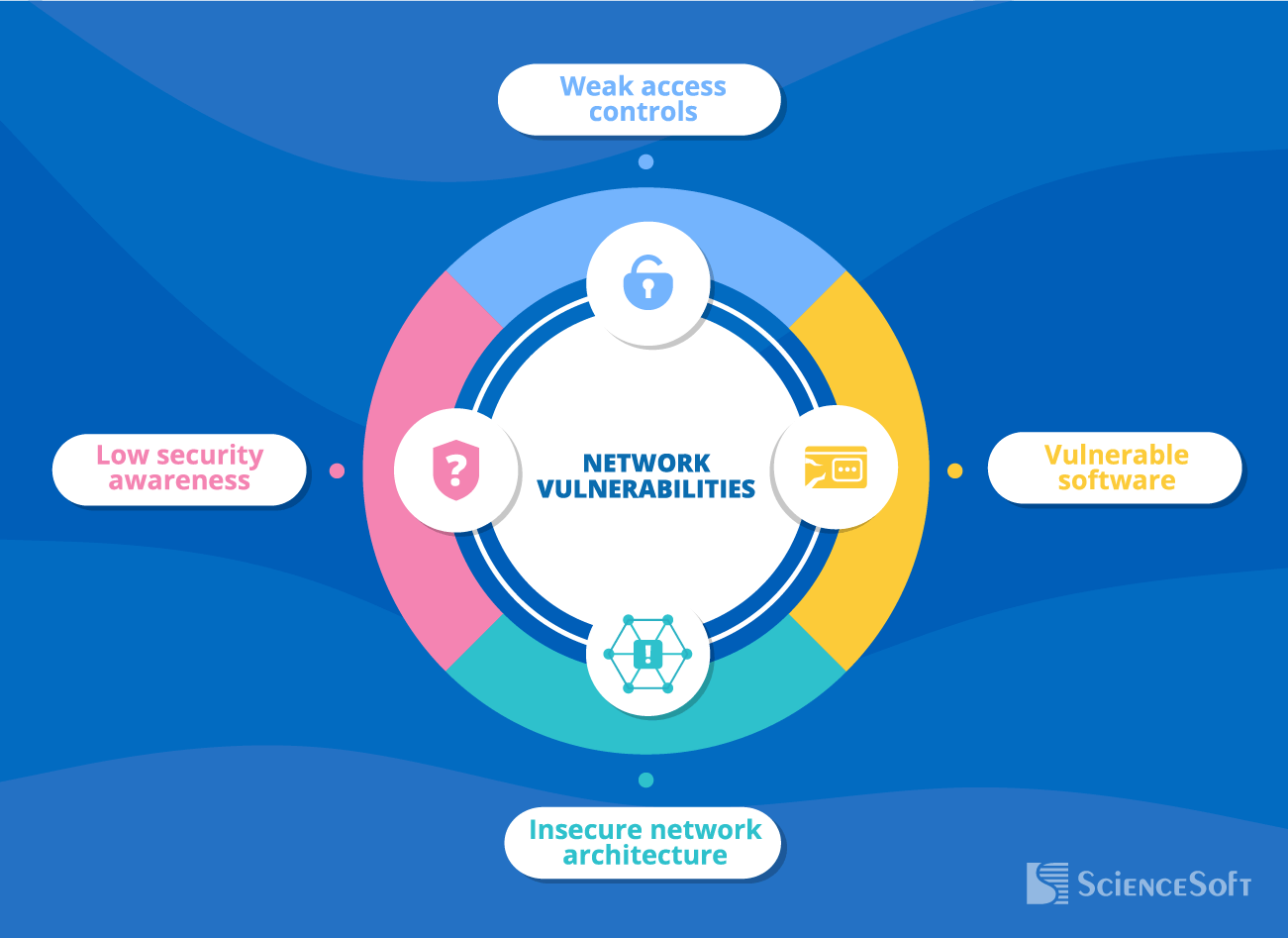
Weak access controls
- Easy-to-guess passwords.
- Single-factor authentication.
- Unrestricted or poorly restricted access to sensitive information or critical network components.
How we can help
Vulnerable software
- Deprecated or unpatched software.
- Misconfigured software, including security services and tools.
How we can help
Insecure network architecture
- Absent or inefficient network segmentation that, in case of a breach, will enable intruders to freely move around the network and easily reach its critical components.
How we can help
Low security awareness
- Employees breaking security rules due to negligence or ignorance: e.g., clicking malicious links, connecting unsecured devices to the network, accessing corporate IT network via public Wi-Fi without VPN, etc.
How we can help
Consider Professional Network Vulnerability Assessment Services
Equipped with best security practices of NIST SP 800-115, OWASP Web Security Testing Guide, CIS Benchmarks, CIS Controls, and other authoritative sources, our team is ready to help you pinpoint and eliminate network vulnerabilities.
Why Businesses Choose ScienceSoft for Network Vulnerability Testing
- In cybersecurity since 2003.
- Competent security team, including Certified Ethical Hackers and compliance consultants.
- A solid portfolio of successful cybersecurity projects in healthcare, BFSI, retail, energy, manufacturing, public sector, and telecoms.
- Recognized as Top Penetration Testing Company by Clutch.
- ISO 27001-certified security management based on comprehensive policies and processes, advanced security technology, and skilled professionals.
- A quality-first approach based on a mature ISO 9001-certified quality management system.
ScienceSoft’s Vulnerability Assessment Team
Lead security engineer
- Leads the vulnerability assessment team.
- Mentors security engineers in assessment techniques.
- Develops vulnerability scan schedules.
- Suggests remediation strategies for discovered security vulnerabilities.
Security engineer
- Performs the necessary activities from configuring the scan to reporting scan results.
- Configures and operates vulnerability assessment tools.
- Reports on technical and procedural findings of vulnerability tests.
- Manually validates vulnerability findings for false positives and documents the findings.
|
|
One security engineer is enough to tackle vulnerability assessment of a small network (up to 50 IPs). |
Vulnerability Assessment Sourcing Models
The Perks of Vulnerability Assessment by ScienceSoft
Precise assessment scoping
We analyze your request and study testing targets to define the optimal testing scope. We aim to save your resources by not going beyond the necessary scope.
A complete view of vulnerabilities
We detect maximum vulnerabilities in your network, but we don’t stop at that. We identify the criticality of the flaws and help you prioritize remediation activities.
Facilitated regulatory compliance
We will provide you with a detailed roadmap to fixing security gaps to achieve compliance with HIPAA, PCI DSS, SOX, GDPR, GLBA, and other major security standards and regulations.
Beneficial long-term partnership
We value solid business relationships and are happy to offer flexible billing plans and favorable terms for repeat business.
Trusted Tools We Employ to Detect Network Vulnerabilities
Network vulnerability scanning implies the use of automated tools that examine network structure, endpoints, network devices, and services to identify weaknesses that may enable unauthorized access to the network.
During vulnerability assessment projects, ScienceSoft’s cybersecurity engineers often use the following tools. They provide high-quality reports and frequently update their vulnerability databases.
Network Vulnerability Assessment Costs

Network vulnerability assessment pricing generally ranges from $5,000 to $15,000. Here, we highlight the essential cost factors:
- The complexity of the network infrastructure.
- Network size (the number of IPs, applications scanned, etc.).
- Applied assessment method (automated scanning, manual assessment, or a combined approach).
- Service provision model (one-time or long-term, as long-term relationships with a vendor may reduce subsequent costs).
- The need for a follow-up penetration testing to investigate the potential impact of the detected vulnerabilities’ exploitation.
Need to estimate vulnerability assessment costs?
|
|
Note: In case of in-house network vulnerability assessment, additional costs also include vulnerability scanning tool licensing (usually charged as a subscription-based fee). |
Common Questions About Network Security
What are the pillars of network security?
- Full visibility of network components that enables their timely vulnerability management.
- Strong network access controls.
- Properly configured security tools: firewalls, antivirus, DLP, IPS, SIEM, and others.
- Adherence of all network users to security rules and best practices.
- Regular security checkups: vulnerability assessment and penetration testing.
What is the most vulnerable part of the network?
Mobile devices, such as smartphones, laptops, and tablets, especially those used by remote employees, are considered the major sources of network vulnerabilities: outdated software, weak passwords, misconfigured firewalls and other security tools, insecure connections, etc. With these devices, it is difficult to control if the necessary security measures, such as vulnerability patching or security updates, are applied consistently. In addition, mobile devices often get lost or stolen.

About ScienceSoft
ScienceSoft is a global IT consulting and software development company headquartered in McKinney, TX. Since 2003, ScienceSoft has been providing vulnerability assessment and security testing services to help companies locate and mitigate network vulnerabilities and meet compliance requirements. Being ISO 9001 and ISO 27001 certified, we rely on a mature quality management system and guarantee data security to our clients during cooperation.















