Big Data Security: Issues, Challenges, Concerns
While the snowball of big data is rushing down a mountain, gaining speed and volume, companies are trying to keep up with it. And down they go, completely forgetting to put on masks, helmets, gloves, and sometimes even skis. Without these, it’s terribly easy to never make it down in one piece. And putting on all the precaution measures at high speed can be too late or too difficult.
Prioritizing big data security low and putting it off till later stages of big data adoption projects isn’t always a smart move. People don’t say “Security’s first” for no reason. Big data security is needed to prevent data breaches that can result in data loss, regulatory non-compliance, reputational losses, and wrong business decisions driven by corrupted data. According to the IBM 2024 Cost of a Data Breach Report, the global average cost of a data breach in 2024 amounted to $4.88 million, which is a 10% increase over 2023 and the highest average cost to date. The industries with the highest costs of data breaches include healthcare, BFSI, manufacturing, technology, and energy.
The report also states that organizations that used AI and automation security tools saved an average of $2.22 million thanks to data breach prevention. You can explore one of ScienceSoft’s projects to see how an AI-powered security tool can identify vulnerabilities overlooked by human professionals.
And as ‘surprising’ as it is, almost all security challenges of big data stem from the fact that it is big. Very big. According to Statista, the total amount of data created and consumed globally will reach 394 zettabytes by 2028.
Short Overview
Problems with security pose serious threats to any system, and businesses constantly adapt security measures to protect their data. For example, there is a tendency to replace the traditional perimeter-based security model with zero-trust architectures (ZTA). According to CxO Institute, enterprise adoption of ZTA doubled from 35% in 2020 to 70% in 2025. The essence of such an approach comes from its name — the system doesn’t “trust” anyone but authenticates, authorizes, and monitors every single access request. It validates users and devices in real time and grants users only the permissions they need to perform their tasks.
But big data is special, and so are the big data security challenges. Below, our big data experts cover the most vicious big data concerns associated with security:
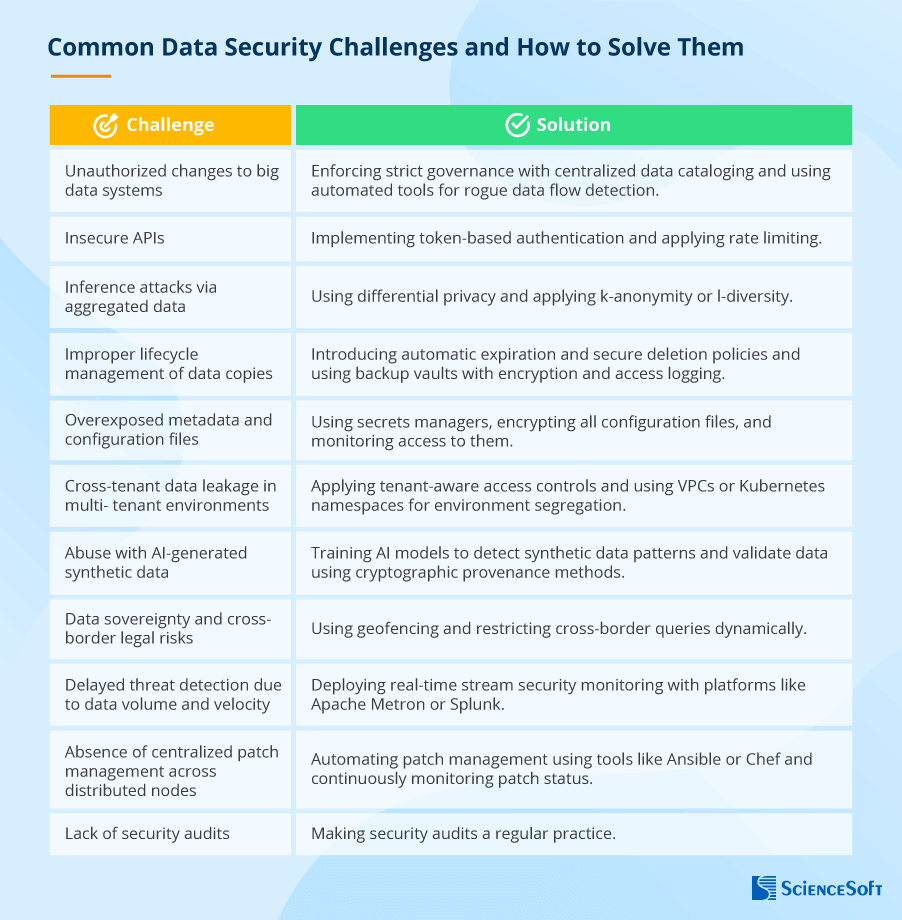
Now that we’ve outlined the basic big data security concerns, let’s look at each of them a bit closer.
#1. Unauthorized Changes to Big Data Systems
In large organizations, teams or individual employees often create unsanctioned tools, scripts, or data pipelines without the knowledge of IT or security teams, which is known as “shadow IT.” The introduced changes may not adhere to security standards and thus create a vast attack surface, leading to untracked data movements, insecure connections, or sensitive data exposure.
Solution:
The processes for creating new data pipelines and scripts should be centralized and continuously monitored. The basis for this should be a data governance framework with a centralized data catalog (to document all data assets of your organization) and clearly described processes for adding adjustments to the system with mandatory security vetting. You can also implement discovery tools that automatically detect and flag rogue data flows.
#2. Insecure APIs in Big Data Systems
Big data frameworks like Spark, Kafka, and Hadoop feature APIs for system integration and management. These APIs may be improperly secured; for example, they might lack strict authentication, access control, and monitoring. In such scenarios, attackers can exploit them to gain unauthorized access, inject malicious commands, or extract sensitive data. One of the biggest data breaches happened due to insufficient API security. Cybercriminals got access to the database of National Public Data, a company that processes public records, including property and court records and voter registrations. As a result, personal data of 1.2 billion individuals was compromised.
Solution:
You can use the OAuth 2.0 framework that enables token-based authentication instead of requiring users to provide their passwords. Another way to protect APIs is to apply rate limiting — set the number of requests that can be sent to the API within a certain time. Monitoring is also an essential part of API protection. Make sure to log all API activity and enable alerting for anomalous API calls.
#3. Inference Attacks Via Aggregated Data
Unfortunately, even secured data can still be at risk of manipulation. One such example is related to anonymized data. Adversaries can combine multiple data sources to re-identify individuals or infer sensitive attributes. This is especially risky in the healthcare and financial domains, where seemingly harmless aggregate queries can be manipulated to extract personal information. Let’s imagine attackers get access to the demographic data of clinical trial participants without knowing their names. While harmless as it is, this data can be matched with trial-specific info in social media posts and help identify certain individuals.
Solution:
Attackers may be smart, but there are tricks that can beat them at their own game. Firstly, you can deliberately introduce statistical noise to your data, which is called differential privacy. For example, you can slightly exaggerate the number of clinical trial participants with adverse effects or change the values of customer financial transactions, thus mixing up the cards in the matching game. Things can be further complicated for attackers by utilizing k-anonymity and l-diversity. The former is about generalizing attributes (like putting age values as ranges [30-35] instead of exact figures). The latter is about making sure that no combination of identifiers (e.g., age, gender, address) has a unique differentiator. For example, in a healthcare dataset, you’ll have to make sure that there is no single person with a unique diagnosis.
#4. Improper Lifecycle Management of Data Copies
Quite often, big data management overlooks leftover data, such as temporary data extracts, transformation layers, backups, and test datasets. Just like in thriller movies, when blackmailers use receipts and paper notes from the trash bins to manipulate their victims, cybercriminals can exploit such shadow data (of course, if it is not properly tracked, encrypted, and deleted).
Solution:
Treat leftover data with due respect and precaution. Establish mechanisms for automatic expiration and secure deletion. You should also track the lineage of all data copies and use backup vaults with encryption and access logging.
#5. Overexposed Metadata and Configuration Files
Another category of data that is often not granted proper attention is configuration files and metadata. If they are not secured or encrypted, attackers can use them to compromise the entire data infrastructure, as these files contain sensitive system details, including connection strings, credentials, and access keys.
Solution:
Treat metadata and configuration files as sensitive assets. Use secrets managers (e.g., HashiCorp Vault, AWS Secrets Manager) and restrict access via RBAC policies. Encrypt all the relevant files and monitor access to them.
#6. Cross-Tenant Data Leakage in Multi-Tenant Environments
In cloud or multi-tenant big data environments, multiple clients share infrastructure. Misconfigured access controls or software bugs can lead to data leakage between tenants. Such breaches are difficult to detect and can have profound compliance implications.
Solution:
Apply tenant-aware access controls, i.e., the ones with strong user authentication and authorization mechanisms and contextual access controls (when access decisions are made taking into account various details such as user role and device type). It is also essential to use VPCs or Kubernetes namespaces for environment segregation and conduct regular penetration testing to validate tenant boundaries.
#7. Abuse With AI-Generated Synthetic Data
If your big data system uses AI for automated decision-making (for product recommendations, quality monitoring at manufacturing sites, fraud detection, etc.), those AI engines may be vulnerable to AI itself. Attackers can use generative AI to create synthetic yet realistic data that can bypass traditional validation checks. If injected into AI training pipelines, such data can do what is called model poisoning — compromise models by introducing bias or targeted behavior.
Solution:
The antidote here is to train the model to detect synthetic data patterns. For example, you can introduce supervised learning classifiers to flag unnatural data distributions. The training is performed on dedicated datasets where real and AI-generated data is tagged, allowing the model to learn how to distinguish between the two. It is also efficient to validate data using cryptographic provenance methods, such as digital signatures and hash functions.
#8. Data Sovereignty and Cross-Border Legal Risks
In large-scale big data systems, data can cross international borders, let’s say in global payment processing systems, social media, and ecommerce platforms. Such “migration” can result in legal penalties and reputational damage because many countries have laws that restrict how and where citizen data can be stored or processed (e.g., GDPR, CCPA, China’s Cybersecurity Law).
Solution:
Implement what is called geofencing: create virtual geographic boundaries that restrict data movement depending on the physical location of users and devices. This way, you can control where data is accessed, processed, and stored and get alerts on potential cases of improper data use. Datasets can also be tagged with jurisdictional metadata, which helps restrict cross-border queries dynamically. For example, if data is tagged as subject to EU GDRP regulations, the system will automatically block any attempts to access this data from other locations.
#9. Delayed Threat Detection Due to Data Volume and Velocity
The massive volume and real-time nature of big data make it difficult to detect threats promptly. Traditional security monitoring tools may be overwhelmed with heavy load or produce too many false positives, which delays incident response and leaves breaches unnoticed.
Solution:
Adapt your security monitoring tools to the specifics of big data systems. There are real-time stream security monitoring platforms that work well for the case, such as Apache Metron or Splunk. You can also reinforce SIEM systems with threat intelligence feeds. With such an enhancement, SIEM systems can get more context about attacks, automatically block their actions, and help security teams proactively search for potential threats.
#10. Absence of Centralized Patch Management Across Distributed Nodes
Big data clusters often span hundreds of nodes, each with its own components, including operating systems, databases, and applications. These components must be regularly updated (patched), which involves patch identification, acquisition, installation, and verification. Without centralized patch management, some notes are left unpatched and become vulnerable to known exploits.
Solution:
In vast big data environments, automation often becomes the cure. Tools like Ansible and Chef can automate patch management, while security teams should continuously monitor update status and simulate patch deployment in a staging environment before rollout.
#11. Lack of Security Audits
Big data security audits help companies gain awareness of their security gaps. But, while it is advised to perform audits on a regular basis, this recommendation is rarely met in reality. Working with big data has enough challenges and concerns as it is, and an audit would only add to the list. Plus, the lack of time, resources, and qualified personnel (or clarity in business-side security requirements) makes such audits even more burdensome.
Solution:
The way out is unpleasant but obvious: make security audit a regular practice no matter what stumbling blocks prevent you from doing so. Easier said than done, but here are some inspiring statistics for you: the Cisco 2025 Data Privacy Benchmark Study says that 96% of the surveyed companies report that the benefits they reaped from security initiatives outweighed the associated costs. One of the ways to lessen the burden is to outsource yearly audits to an external security partner. The hired team will take over all the responsibility and is more likely to notice issues that an internal team may overlook. Moreover, partnering with the same auditor yearly leads to cost savings in the long run. For example, we at ScienceSoft offer discounts to clients whose infrastructures we are already familiar with.
But Don’t Be Scared: They Are All Solvable
Yes, there are lots of big data security issues and concerns. And yes, they can be quite crucial. But it doesn’t mean that you should immediately curse big data as a concept and never cross paths with it again. No. The thing you should do is carefully design your big data adoption plan remembering to put security to the place it deserves – first. This may be a tricky thing to do, but you can always resort to professional big data consulting to create the solution you need.

