Nick Kurayev
CEO, ScienceSoft
How Not to Fall Victim to 4 Acute Risks of Software Development Outsourcing
Learn the ways to avoid potential project risks in software development outsourcing: poor vendor choice, ineffective vendor-customer communication, insufficient knowledge transfer and inadequate cybersecurity measures.

Nick Kurayev
CEO, ScienceSoft
Why Agile is Great for Outsourced Software Projects
The Agile approach to software development outsourcing has vivid benefits for vendors in terms of easier project planning, improved team and project management and more opportunities for preventing software quality problems.

Oleg Khmelkov
Principal Architect, ERP & CRM Expert, ScienceSoft
An Ultimate Guide to Microsoft Dynamics 365 Certifications
Find out what Microsoft Dynamics 365 certifications for CRM and ERP products exist, and how having them helps both IT businesses and dedicated specialists.

Nick Kurayev
CEO, ScienceSoft
Don’t Let Software Outsourcing Trends Provoke Risks
Software development outsourcing trends may provoke alarming outsourcing risks instead of bringing expected business benefits. See how to prevent it in your outsourcing initiative.

Irene Mikhailouskaya (Makaranka)
Data Analytics Researcher, ScienceSoft

Data Analytics & BI
Enterprises
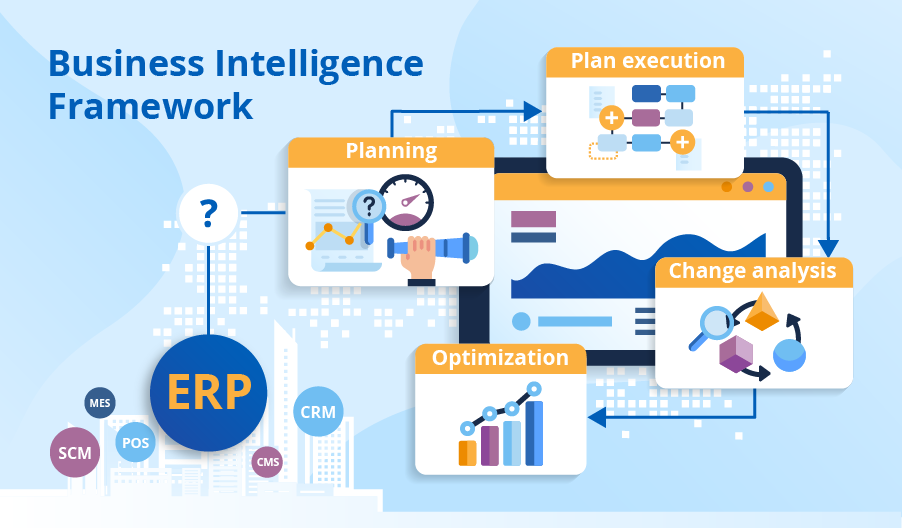
Does ERP Contain Enough Data for Business Intelligence?
Our BI implementation team describes the components of our proprietary BI framework and explains whether ERP data is enough to get valuable insights within each of them.

Tanya Yablonskaya
Ecommerce Industry Analyst, ScienceSoft
Learn to Frame Magento Projects around Your Target Audience
When developing Magento projects, we know how to choose and target promising audience. For our clients, that pays off with conversions and audience loyalty.

Ulad Murashka
Cybersecurity Expert, CEH
Beware 6 Types of Cyberattacks To Preserve Your Company’s Reliability
Find out 6 most common types of cyberattacks and read how to ensure protection against them to keep your business’s reputation solid and clients satisfied.

Sergey Golubenko
Principal Architect, Productivity Solutions Expert, ScienceSoft
What SharePoint Developers Actually Do
You know what skills SharePoint developers should have but don’t know what for? Learn about responsibilities of SharePoint developers.

Tanya Yablonskaya
Ecommerce Industry Analyst, ScienceSoft
Do You Need a Magento Code Audit? Answer 3 Simple Questions
Magento code audit may be a useful initiative even if your website functions well right now. Here are 3 cases to prove that.