Information Security Blog
Welcome to our Information Security blog!
This blog is for CIOs, managers, and security professionals who are looking to enhance their cybersecurity posture. Stay updated on emerging kinds of cybersecurity threats, cyber protection methods, and various security testing types by reading short and informative articles from our ethical hackers and security consultants.
All the articles are based on our hands-on experience in providing security and compliance services to businesses in 30+ industries, including healthcare, BFSI, retail, manufacturing, and telecoms. Bookmark to stay on top of the latest cybersecurity trends!

Dmitry Kurskov
Cybersecurity Director and Principal Architect, ScienceSoft
Healthcare IT
Information Security
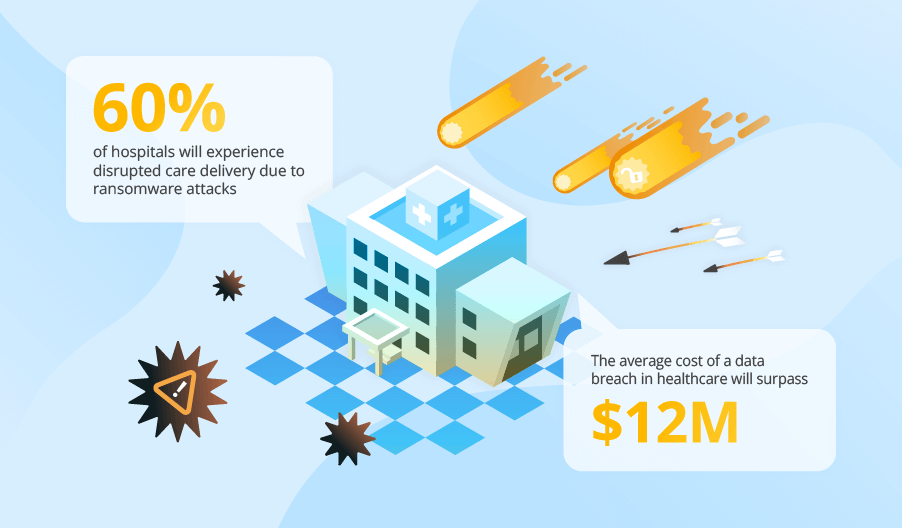
Cyber Attacks on Healthcare to Affect Almost Half of Health Systems, Threaten Patient Treatment, and Drive Up Breach Costs. Unless?

Dmitry Nikolaenya
Cybersecurity Expert
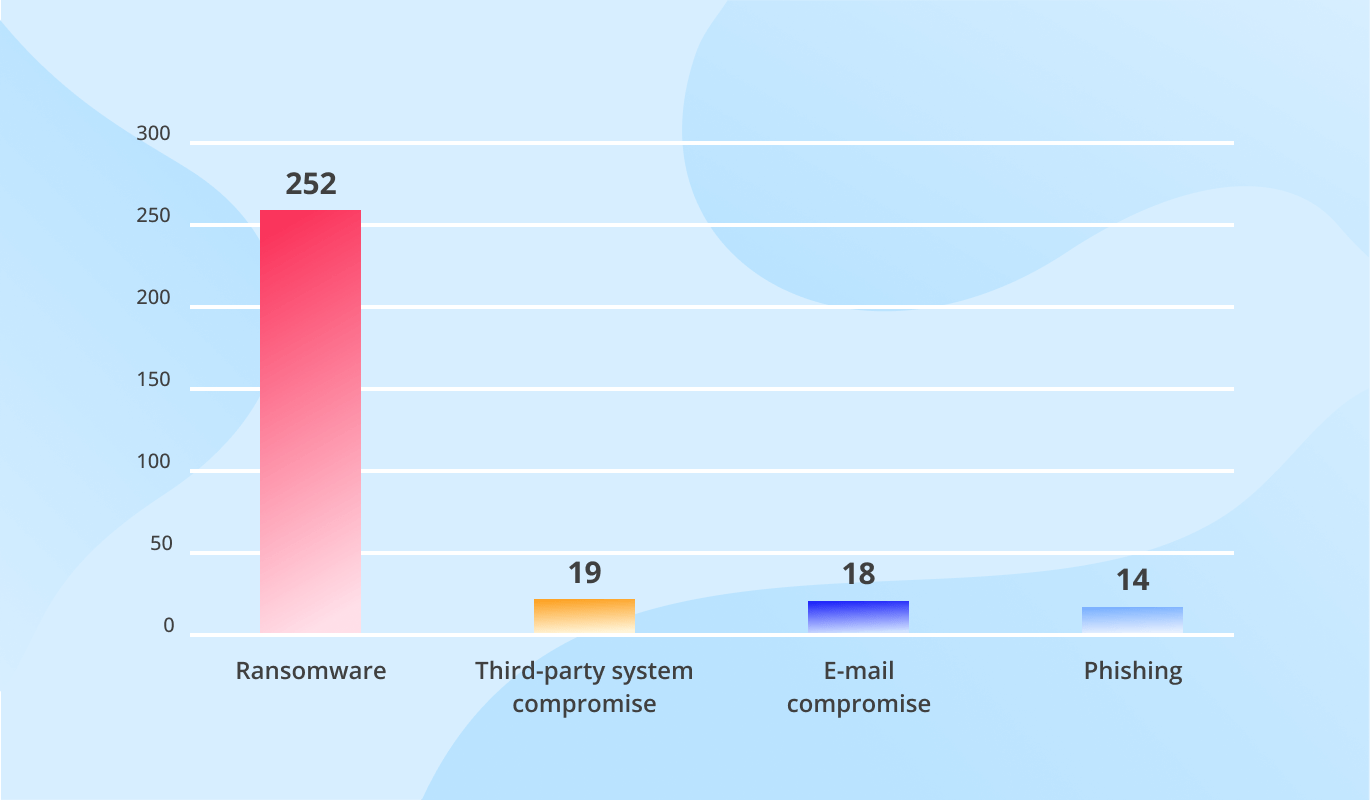
Information Security
Healthcare IT
No Head in the Clouds! How Healthcare Providers Can Avert Cloud Security Breaches

Alena Madden (Nikuliak)
Senior Business Analyst and Healthcare IT Consultant, ScienceSoft

Healthcare IT
Information Security
How to Avoid Telehealth Security and Privacy Risks

Alex Bekker
Principal Architect, AI & Data Management Expert, ScienceSoft

Big Data
Data Analytics & BI
Information Security
Big Data Security: Issues, Challenges, Concerns

Ulad Murashka
Cybersecurity Expert, CEH
Information Security
Vulnerability Assessment vs. Penetration Testing

Dmitry Kurskov
Cybersecurity Director and Principal Architect, ScienceSoft
Information Security
In-House vs. Outsourced SOC: Finding the Right Cybersecurity Strategy

Dmitry Kurskov
Cybersecurity Director and Principal Architect, ScienceSoft
Information Security
Why SOC 2 Compliance Is the Gold Standard of Security for SaaS Companies

Dmitry Kurskov
Cybersecurity Director and Principal Architect, ScienceSoft

Information Security
BYOD Security Policy Best Practices: Safeguarding Employee Devices

Dmitry Kurskov
Cybersecurity Director and Principal Architect, ScienceSoft

Information Security
