IoT Penetration Testing Strategy
Gartner expects more than 65% of enterprises (for reference, it was only 30% in 2017) to adopt IoT solutions by 2020. And the total number of connected things installed across the world will rise beyond the 20 billion mark. "IoTzation" may bring convenience to an individual’s life and numerous productivity benefits to businesses, but they all fade in comparison with security threats the IoT world poses.
Major security concerns, such as preventing loss of control over connected things, as well as breaches of sensitive information, have driven the need for IoT-specific penetration testing services.
IoT security: who’s on duty today?
A typical IoT solution is a system of connected components that can be grouped into three categories:
- Things (smart devices, sensors and actuators).
- IoT field gateways.
- The cloud (cloud gateway, streaming data processor, big data warehouse, data analytics, machine learning and control applications, client-server user applications).
So, who holds responsibility for the security of each component? Is it necessary for companies using IoT systems to conduct its own penetration testing? Or are these solutions protected enough already? Let’s straighten it out.
Things
Security of smart things equipped with sensors and actuators should be ensured by device manufacturers. These companies should specify and follow security requirements, implement security best practices and conduct security testing. In reality, device manufacturers are well experienced in mechanical and electrical engineering and physical safety, but not in software security. And you can understand them. If a company wants to make a secure smart device, it has to hire IoT security experts and organize security training sessions for their staff. Often, a company’s budget can’t allow for such expenditures. Furthermore, security of a smart device doesn’t end after it’s developed and sold. A device manufacturer has to maintain it through regular firmware updates, which also bears additional costs.
In the long run, device manufacturers, who disregard the security of smart devices in many cases become the cause of IoT customers’ security breaches. Here’s some evidence to prove that.
- A smart device may have a hidden account where the user can’t change a password. The default one is usually a "super-complex" combination like 123456. Though the account is not available through a web interface, hackers can easily access it via Telnet or SSH protocols.
For example, Trustwave reported such remotely exploitable backdoor in the Telnet interface of DblTek-branded devices. According to F-Secure, default credentials in security cameras produced by Foscam were exploited by hackers to view video feeds, download stored files, and compromise other devices connected to a local network.
- Hackers see smart devices as perfect botnets. Such devices are constantly connected to the Internet, giving cyber criminals more opportunities for hacking. Moreover, hacked IoT devices are more hacker-friendly than computers: they are always online and, due to poorly engineered update mechanisms, stay infected long after exploitation. One of the most famous cases was a 2016 DDoS attack that affected the US and Europe. IoT devices produced by a Chinese manufacturer Xiongmai were co-opted into a multi-million botnet called “Mirai”, because the compromised devices lacked the ability to set a password on some forms of connection.
If the above-mentioned manufacturers had implemented smart device penetration testing, the vulnerabilities could have been detected and patched in good time.
IoT field gateways
IoT field gateways also quite often become hackers’ targets. First of all, the gateways have high processing power. More power – more complex software, and, hence, more vulnerabilities to exploit. Secondly, these are edge devices between things and the cloud part serving as the point of entry for intruders.
Although manufacturers of IoT field gateway devices should provide security to the communicating channel and encryption for the transmission of the IoT data, your company should schedule penetration testing annually, at the least. This way, you’ll be confident that all communications between the gateways and devices are secure.
The cloud
A private cloud owner holds all the responsibility for the security of the IoT cloud. That is for all its integral parts: cloud gateway, streaming data processor, big data warehouse, data analytics, machine learning and control applications, client-server user applications.
If your company is a private cloud owner, don’t hesitate to conduct thorough pentests, including DDoS testing. In case your company is a public cloud customer, both you and your cloud provider share responsibility for IoT cloud security.
Because the cloud service market is highly competitive, cloud service providers try to maintain a strong security posture and conduct cloud penetration testing themselves. But you can never be sure whether such testing was deep enough to cover maximum vulnerabilities and covered the most critical targets:
- Cloud gateway (as it’s a border element between the Internet and the cloud).
- Streaming data processor (as it handles all data flows and is also placed near the border).
- Data analytics (as it can be accessed through the web).
- User applications (as they face the Internet).
So, usually, IoT cloud customers hire a third-party penetration testing vendors to check if their cloud providers pay due attention to security aspect.
Identifying the right IoT penetration testing vendor
Apparently, your company, as an IoT customer, should guard the security of the entire IoT ecosystem. One of the ways to address this challenge is to contract penetration testing providers, who are able to uncover security weaknesses in multiple IoT components.
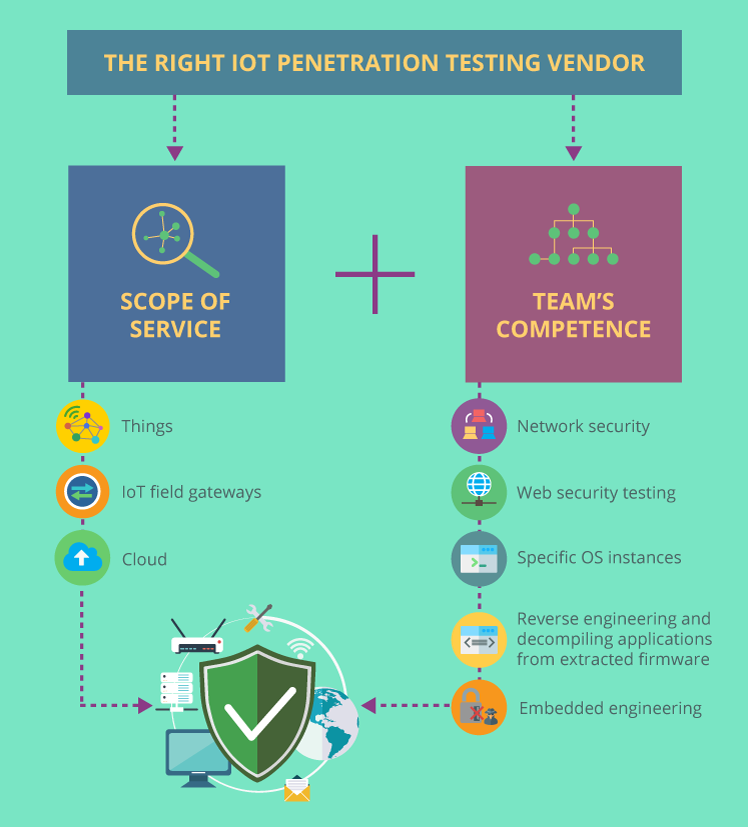
What distinguishes a good IoT penetration testing vendor? It’s the scope of service and the security team’s competence. A reputable vendor will include each element of the IoT system (things, IoT field gateways, and the cloud) into the testing scope. Such an extensive scope of service, in its turn, requires a background in different types of security assessment (such as vulnerability assessment, network and application penetration testing, security code review), plus the skills unique to smart devices.
Larry Trowell, an associate principal consultant at Synopsys Software Integrity Group, names key areas a security engineer should be good at to conduct a thorough IoT penetration testing:
- Cloud infrastructure – to know the principles of cloud architecture.
- Network security – to determine what protocols are being used and what information is at risk.
- Web security – to understand if there are vulnerabilities connected to web-based configuration interface on an embedded device.
- Specific OS instances. Although most devices run Linux, some of them work on QNX, VXworks or Windows embedded. There are also cases of custom operating systems.
- Reverse engineering and decompiling applications from extracted firmware – to determine if an IoT device running straight on the metal (having no OS) is vulnerable to attacks.
- Embedded engineering – to find backdoor interfaces.
Filtering out incompetent IoT penetration testing vendors
Both the US and European cybersecurity authorities have already admitted the need to introduce strict regulations on IoT data protection in 2018. Thus, security obligations of IoT device manufacturers and cloud providers will be defined on a federal level. Meanwhile, the responsibility for the whole IoT solution’s security lies in your hands, and the choice of the right IoT penetration testing vendor is half the battle against cybercrime.

