No Head in the Clouds! How Healthcare Providers Can Avert Cloud Security Breaches
Editor’s note: In the article, Dmitry examines the key vulnerability sources for cloud healthcare software and highlights protective measures that work best against data breach threats. Keep reading for insights on the effectiveness of traditional and advanced cybersecurity tools. And if you doubt your existing cloud deployment is secure enough, check our vulnerability assessment services.
Most US healthcare organizations have already moved their software to the cloud. A recent industry study found that 70% of the providers surveyed now use cloud computing and storage, and this number goes up to 90% among hospitals. And among those who haven’t migrated to the cloud yet, only 6% have no plans to do so in the next few years.
The top three reasons for cloud adoption include performance and reliability, ease of access and management, and the total cost of ownership (TCO). However, migration to the cloud is not all roses. Connection to the cloud opens up new attack vectors for adversaries and adds another layer of difficulty to maintaining healthcare software compliance, especially in terms of securing patient data.
Healthcare Data Breach Risks in Numbers
According to the 2024 Healthcare Data Breach Report, the number of data breaches reported to the HHS Office for Civil Rights (OCR) stayed at about 727 incidents per year over the last four years. Yet, the number of compromised patient records is increasing drastically: from 57 million in 2022 to 275 million in 2024, which equals 82% of the US population.
As for financial implications, in 2024, the HHS OCR imposed fines on 22 healthcare providers and business associates, ranging from $10,000 to $4.5 million, totaling $12,841,796. According to IBM's report, the average cost of a healthcare data breach in the US is $10.93 million, which is much higher than in any other industry.
Network servers, including cloud storage, are the most common location where protected health information (PHI) is compromised, and such breaches account for 62% of all the PHI breaches reported in the US in 2024.
Cybersecurity Threats Most Common for Healthcare Cloud Environments
The diagram below shows the most common causes of data breaches in 2024, according to the Forescout review.
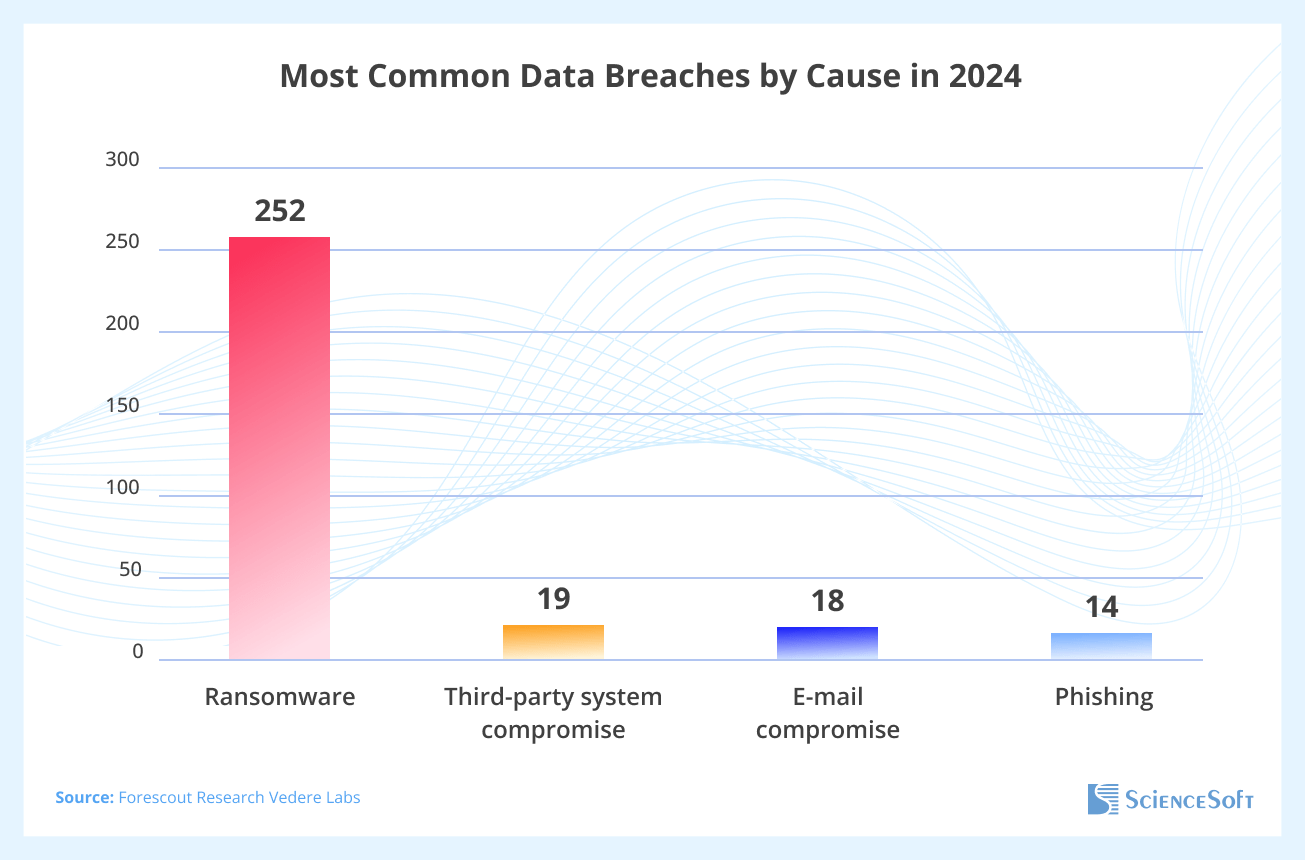
If we put together the findings of leading experts on healthcare data security (see links below), we can highlight the following four types of threats that pose the greatest risk to healthcare providers using cloud software.
- Ransomware and extortion: Attackers use ransomware to encrypt electronic protected health information (ePHI), disable healthcare systems, and demand a ransom. They also often use “double extortion”, not only encrypting the data but also threatening to publish PHI. This is the leading cause of cloud security incidents. According to a Ponemon Institute survey, 88% of the 2,547 surveyed organizations had experienced one or more ransomware attacks in 2024. The top entry attack vectors for adversaries using ransomware were phishing (45%), remote access hacks (32%), and unpatched software vulnerabilities (19%).
- Third‑party and supply-chain compromise: Cyber actors exploit vulnerabilities of a healthcare organization’s vendors and suppliers to gain access to healthcare systems. It’s the second most common cause of breaches, after ransomware. Healthcare IT systems are typically connected to a complex ecosystem of third-party vendors, and a single weak link can compromise the entire cloud infrastructure. According to the SecurityScorecard report, healthcare organizations work with an average of 15.5 third-party vendors, and in 98.3% of cases, had at least one third-party partner that suffered a data breach in 2023.
- Phishing, social engineering, and pretexting: Attackers target an organization’s employees via email or social media, using fake identities, and then pressure them to install ransomware, steal system access credentials, or disclose patient data. They increasingly use AI to produce deepfakes and sophisticated social engineering tactics. Phishing is a top threat for healthcare entities, with over 90% of cyberattacks involving phishing schemes. In 2024, over 80% of healthcare organizations experienced at least one successful phishing attack.
- System misconfigurations and IAM failures: Apart from stolen credentials, unauthorized access to healthcare data, and ransomware attacks, breaches can also occur through cloud platform misconfigurations, such as accounts with excessive privileges, lack of multi-factor authentication, open storage buckets, and weak API settings. The 2024 CSA report highlights misconfiguration and inadequate Identity and Access Management (IAM) as the two biggest cloud security risks.
Securing Healthcare Data in Cloud Environments
Choice of cloud deployment model
Data remains secure only when access is properly controlled and limited to authorized users. The level of control largely depends on the cloud deployment model used by a healthcare organization.
- Public cloud deployment implies that healthcare software is hosted by a cloud service provider who rents out data center resources to customers (tenants).
- Private cloud deployment (on-premises or externally hosted) means that data center resources belong to the customer. In addition, it can be expanded to create a community cloud, linking collaborating healthcare providers.
- Hybrid cloud deployment is a combo of the models mentioned above.
It’s obvious that private clouds offer healthcare organizations the maximum control over their information resources. Thus, systems containing PHI (protected health information), such as EHR (electronic health records), a cloud app for wearable biosensors, or cloud-connected medical devices, are typically stored in private clouds.
In a private cloud, healthcare software can be deployed either on-premises or externally. In the case of on-premises deployment, a cloud service provider has no access to the customer’s environment, which enhances the healthcare data security. Yet, this option requires healthcare providers to make significant investments in infrastructure (virtualized on-premises data center). Therefore, the most cost-efficient deployment model for healthcare software is an externally hosted private cloud, where the service provider facilitates an exclusive and fully private cloud environment.
Best practices of cloud security in healthcare
Securing patient data is a shared responsibility between the cloud provider and the healthcare entity. Both of them are required to follow industry regulations and standards on data privacy and security, such as HIPAA, HITRUST, and ISO 27001. Therefore, healthcare organizations host their systems on HIPAA-compliant cloud platforms, whose providers properly handle securing the infrastructure. Meanwhile, the organization itself is responsible for protecting its data and applications in the cloud.
Below, I provide an overview of the most crucial tasks for healthcare providers to ensure cloud cybersecurity according to the HIPAA, Cloud Security Alliance (CSA), and the National Institute of Standards and Technology (NIST) recommendations.
Strong access management
Access control in healthcare systems must go beyond basic restrictions to ensure data is only available to authorized personnel with clearly defined roles. The HIPAA Security Rule mandates unique user IDs for every employee, clear separation of privileged accounts (with access to sensitive data or administrative functions), and role-based access control (RBAC) relying on the principle of least privilege (giving users only the minimum access they need to do their job). Another mandatory safeguard is multi-factor authentication (MFA). Some of the most common security gaps in healthcare that lead to data breaches involve employees using weak passwords, a lack of policies for revoking credentials for employees who leave the organization, inadequate corporate email security, and misconfigured software access settings.
Third-party risk management
Organizations should perform a security risk assessment for every partner involved in their software ecosystem. A healthcare organization’s vendors and suppliers must comply with HIPAA and similar regulations, follow cybersecurity frameworks like NIST CSF, disclose vulnerabilities, and report security incidents. All partners who get access to or process ePHI must sign a HIPAA-compliant Business Associate Agreement (BAA) that legally obligates them to apply HIPAA Security Rule safeguards.
Asset inventory and comprehensive data encryption
Organizations should maintain an inventory of their entire data, classifying it based on sensitivity. PHI must be separated from less sensitive cloud-stored data, making it possible to apply special rules for access, data flow, encryption, and backup. All sensitive data must be encrypted at rest and in transit using NIST-approved algorithms. Organizations must also ensure that all endpoints (devices used to access cloud software), including mobile devices, use secure encryption for any ePHI they handle. Data encryption reduces the risk of insider attacks, data exfiltration through malware, and other security threats. It’s also an effective method used for APT protection.
Continuous security logging and monitoring
According to HIPAA’s audit-control requirement, every access attempt and transaction involving ePHI must be logged, so that it’s possible to detect abnormal activity such as lateral movement (moving between systems after gaining unauthorized access) or data exfiltration. It is recommended that all system logs (from network and application firewalls, servers, databases, and apps) be centralized and integrated into a Security Information and Event Management (SIEM) system. Organizations should ensure continuous (24/7) security monitoring and conduct regular log analysis. Without those measures in place, breaches can remain unnoticed for months, as is often the case. IBM reported that in 2024, only one-third of the incidents were detected by internal security teams.
Incident response planning
Under HIPAA requirements, covered entities are required to establish a healthcare data breach notification procedure plan. It should outline how to identify, assess, and report PHI breaches to affected individuals, regulators, and, when applicable, the media. Providers should also have a breach containment and recovery plan to prevent chaotic reactions that could exacerbate the damage. Such a plan can define key contacts for incident reporting, escalation paths, steps for isolating affected cloud resources, failover sites to switch to, data recovery procedures, and notification processes for communicating incidents to an organization’s departments and external partners.
Integrity control and security assessments
ePHI stores and system files require regular integrity monitoring (e.g., checksums, anti-malware scanning) with the help of cloud provider tools or third-party solutions to detect unauthorized modifications (such as malware encryption and tampering) and prevent silent data corruption. HIPAA also requires continuous monitoring of the cloud environment security (e.g., using NIST CSF frameworks). This includes regular vulnerability scans and penetration tests on cloud applications, risk reassessments when new cloud architecture components (such as microservices, containers, and APIs) are introduced, as well as proactive mitigation of detected threats and vulnerabilities.
Employee training and security policies
Since humans are often the weakest link in an organization’s cybersecurity protection, the HIPAA Security Rule requires mandatory training for all medical staff who access ePHI. The training must cover topics such as safe browsing, effective password management, reducing susceptibility to phishing and social engineering, protecting against malware, and other relevant areas. Additionally, the organization must clearly define each employee’s responsibilities for maintaining cybersecurity and regularly monitor whether employees comply with these requirements.
Redundancy and backups
Healthcare providers must guarantee the continuous availability of ePHI, which requires that their cloud infrastructure and Service Level Agreements (SLAs) are designed to support high availability and minimal downtime. It's also mandatory to regularly back up ePHI (including off-site or immutable backups) and have established data restore procedures. In cloud environments, redundancy and backups not only support HIPAA compliance but also protect against ransomware (since attackers can’t encrypt offline backups) and prevent ePHI loss when the provision of cloud services is affected by power outages or natural disasters.
AI/ML for Healthcare Cloud Security
Artificial intelligence (AI) and machine learning (ML) are increasingly used to strengthen information security in healthcare cloud systems, as they can process large volumes of cloud and network data, spot subtle anomalies that traditional tools can't detect, and automate routine operations.
There are several areas where major healthcare organizations and cloud providers can apply AI to enhance their cybersecurity defences.
- Anomaly and threat detection: AI in cloud-native SIEM systems can analyze massive cloud logs and network data in real time, comparing them with normal user and system behavior to detect anomalies, such as unusual logins or large data transfers. This helps identify intrusions that standard rules might miss, and thus respond to threats much faster.
- Automated incident response: AI/ML can automate threat containment actions. For instance, if an AI/ML engine detects ransomware encryption patterns in a cloud data store, it can isolate affected instances, revoke credentials, and roll back to snapshots without waiting for human intervention. This automation cuts response time and limits damage.
- Intelligent data loss prevention (DLP): AI-enabled data loss prevention (DLP) tools can scan unstructured data stored in cloud environments or SaaS applications and automatically detect PHI (e.g., names, SSNs, and medical record numbers). Then, it can protect this data from accidental disclosure by alerting employees trying to copy it to local storage. Unlike traditional rule-based DLP, AI/ML uses context to detect PHI more effectively and can adapt to new types of PHI.
- Configuration management: Some cloud platforms use AI/ML to constantly audit cloud configurations (e.g., checking that S3 buckets stay private) and automatically fix minor misconfigurations.
- Vulnerability assessment: An AI engine can also prioritize known cloud vulnerabilities based on how likely they are to be exploited and how critical the asset is, helping healthcare IT teams focus on fixes that protect the most sensitive patient data.
- Predictive security: Advanced AI/ML tools can predict future security risks by learning from past incidents and by correlating threat feeds and system configurations. Besides anticipating where vulnerabilities might be located and which systems are most likely to be targeted, AI can also recommend measures to strengthen cybersecurity defenses.
According to a major study by IBM/Ponemon, AI-driven security tools significantly lower both the cybersecurity costs and operational consequences of healthcare data breaches, notably reducing the breach lifecycle by 108 days on average. NIST also promotes AI (see NIST AI Risk Management Framework), as long as the AI models themselves are secure.
Reliable Multi-Layered Defense for Your Cloud Healthcare System
Implementing isolated measures, such as a private cloud deployment model, adequate data encryption, or a SIEM system, is insufficient to protect your healthcare cloud against data breaches. Only a multi-layered defense will ensure safe data storage in the cloud environment.
To provide comprehensive security for your cloud network, it’s a good idea to resort to cybersecurity services. Experienced security consultants can approach strengthening your cloud’s security holistically, recommending optimal deployment models and security monitoring tools, identifying misconfigurations, and thoroughly assessing compliance with HIPAA and other relevant regulations. They can help make your cloud setup not only secure but also adaptable to changes in IT infrastructure and emerging cyber threats.

