Vishing Simulation and Testing Services
In cybersecurity services since 2003, ScienceSoft helps organizations assess and improve employee resilience to vishing social engineering attacks.
Voice phishing, also known as vishing, is a type of social engineering attack in which a threat actor calls victims and pretends to be a legitimate entity. Social engineers use phishing techniques over the phone to obtain sensitive data like passwords, credit card details, and personally identifiable information (PII), or to manipulate victims into high-risk actions like authorizing transactions or resetting user credentials.
During vishing testing, security professionals simulate real-world vishing attacks to assess an organization's susceptibility to social engineering. These tests are conducted ethically and securely, ensuring that no actual harm or data compromise occurs.
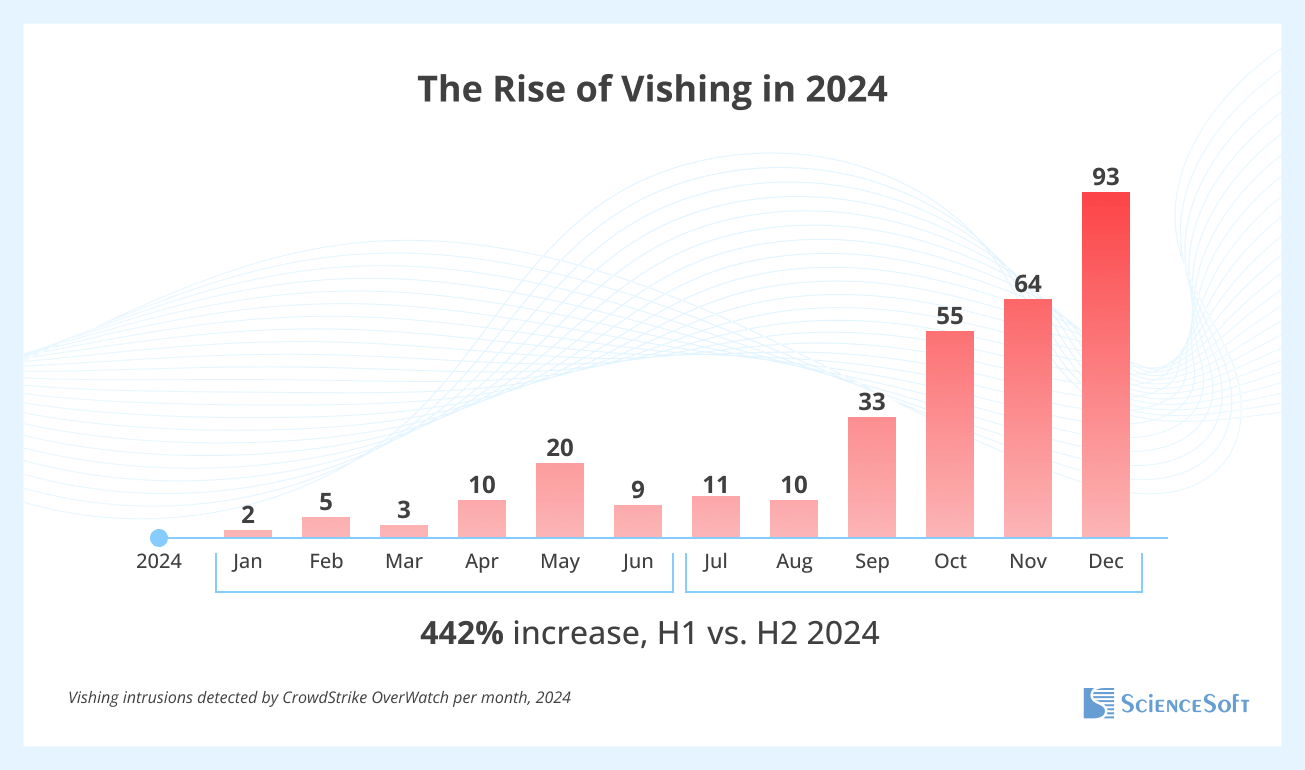
The 2025 CrowdStrike Global Threat Report reveals that the number of detected voice phishing (vishing) attacks surged by 442% from H1 2024 to H2 2024 as adversaries leveraged vishing, callback phishing, and help desk social engineering to infiltrate target networks.
Key Aspects We Test During a Simulated Vishing Campaign
Policy resilience
Before launching a simulated vishing attack, our experts analyze the client’s standard operating procedures (SOPs) for verifying caller identity and authorizing information disclosure to identify vulnerabilities that could be exploited through vishing.
Employee awareness
During a vishing test, we evaluate the staff’s ability to recognize suspicious calls and identify manipulation tactics, such as a sense of urgency, emotional appeals, or impersonation (e.g., a caller posing as an executive). We also check if the employees can effectively respond to suspicious requests by challenging the caller when something seems off.
Policy adherence
By simulating requests for personal data, account access, credential resets, and financial transactions, we determine whether employees follow the established security policies, escalate unverified requests, and report a suspected vishing attempt to security teams.
Vishing Techniques We Employ
OSINT (Open Source Intelligence)
We gather employee information from the client’s company website, LinkedIn, and other public sources. Real attackers often use such details as a base for their requests or casually mention them during the call to establish trust.
Pretexting
Based on thorough OSINT research, we create believable personas and scenarios. To achieve maximum realism, we tailor each specific pretext to the target’s role or current company events.
Spoofed calls
We use VoIP services with programmable caller ID and rotating phone numbers to mimic real-world attacker tactics. This helps us mask the caller’s identity, increasing realism while avoiding detection by the target employee.
Adaptive vishing and dynamic interaction
Our social engineers adapt their approach to the targets’ responses and apply psychological manipulation tactics. For example, if the employee hesitates, the attacker may create a sense of urgency by claiming that they need the employee’s credentials to prevent the loss of their account and business documents.
Key Stages of a Vishing Security Test at ScienceSoft
1.
Preparation
- ScienceSoft’s cybersecurity specialists collaborate with the client organization to define the vishing test scope (e.g., the departments involved and the number of employees to be tested) and goals.
- If permitted, our specialists can review the organization’s existing security policies and identify vulnerabilities that adversaries could exploit. They will then alter future vishing test scenarios to target these specific weaknesses.
- The client provides a list of staff's phone numbers to be targeted in social engineering tests. The targeted employees can be regular specialists working with sensitive data (e.g., accountants, salespeople, call center agents) as well as managers and other roles with high access permissions (e.g., system administrators).
- Our security professionals use publicly available resources to research additional information about the employees, including their position in the company’s hierarchy, working hours, and social connections.
- Based on the gathered data and the test goals, ScienceSoft’s team prepares vishing scenarios and tailors them to the client’s industry (e.g., finance, healthcare, retail).
We always work within clear limits set by the client — you decide what is okay to test and what’s completely off-limits. For example, if we’re calling a help desk, we might pretend to be someone who forgot their password. We may try to confirm if an account exists or see how much info the agent is willing to share with the caller, but we never let them actually reveal sensitive details or reset the password. In either case, there will be no real data breaches or service disruption, and we’re happy to sign an NDA (and BAA to comply with HIPAA) upfront. The goal is to safely test and educate, not to cause harm.
2.
Active testing phase
- We run the vishing simulation over the course of a month, which allows spreading calls across different days and times. This approach keeps the test realistic and helps avoid suspicion and word-of-mouth warnings among employees. The goal is to capture authentic reactions, not rehearsed ones.
- During this stage, our security experts call the target employees’ numbers and act out the prepared scenarios, analyzing the authentication and verification mechanisms used by employees. Each scenario is tailored to reflect real-world threats and current attack trends in the client’s industry, ensuring the tests are relevant and valuable. A simple test can involve calling employees, pretending to be IT staff, and asking them to check or update the current operating system (OS) version. This checks whether the staff question suspicious IT requests and take precautions before revealing information about their computer.
- Knowing that attackers often combine vishing with phishing (for example, emailing an employee, then calling to follow up, leveraging the email for credibility), we can add a phishing simulation to assess overall security awareness in digital communication. In parallel with phone calls, we will send phishing emails to a select group of staff. These emails will be crafted to look legitimate and relevant (e.g., an email from “IT Support” about password policy or a fake customer email with an attachment claiming to be updated documents). We use industry-leading phishing techniques to bypass email spam filters and observe genuine user behavior.
- After the attack simulation, ScienceSoft’s team documents and analyzes the results.
3.
Reporting
Based on the testing result analysis, we provide a final report containing:
- The logs of all phone call attempts, including the information requested and outcomes (e.g., responded calls, what information was disclosed or refused).
- Optional call recordings (with permission and within the legal boundaries of the engagement rules).
- In case vishing is combined with phishing simulation, the report also covers metrics such as opened emails, clicked links, and whether credentials were entered into fake login pages.
- An overview of the detected human vulnerabilities, like security awareness gaps and high-risk behavior.
- Remediation recommendations.
We conduct and document the testing activities following industry standards such as PTES and NIST SP 800-115, making it suitable for internal audit references or compliance evidence if needed. In addition to written reports, we offer a debrief session where our experts present the findings to your team.
4.
Remediation
Additionally, we can:
- Update or create necessary security policies and procedures.
- Conduct cybersecurity training for employees, focusing on vulnerabilities revealed during testing.
Call Centers Are the Primary Target of Vishing Attacks on Business
Contact center agents are an easy target for social engineers since the agents are expected to be engaging and do their best to help callers. Based on the 2024 Vishing Response Report by Keepnet Labs, which presents findings from the company's AI-based voice phishing simulations, customer support is at the highest risk of vishing attacks and has the highest percentage of employees who fell for vishing:
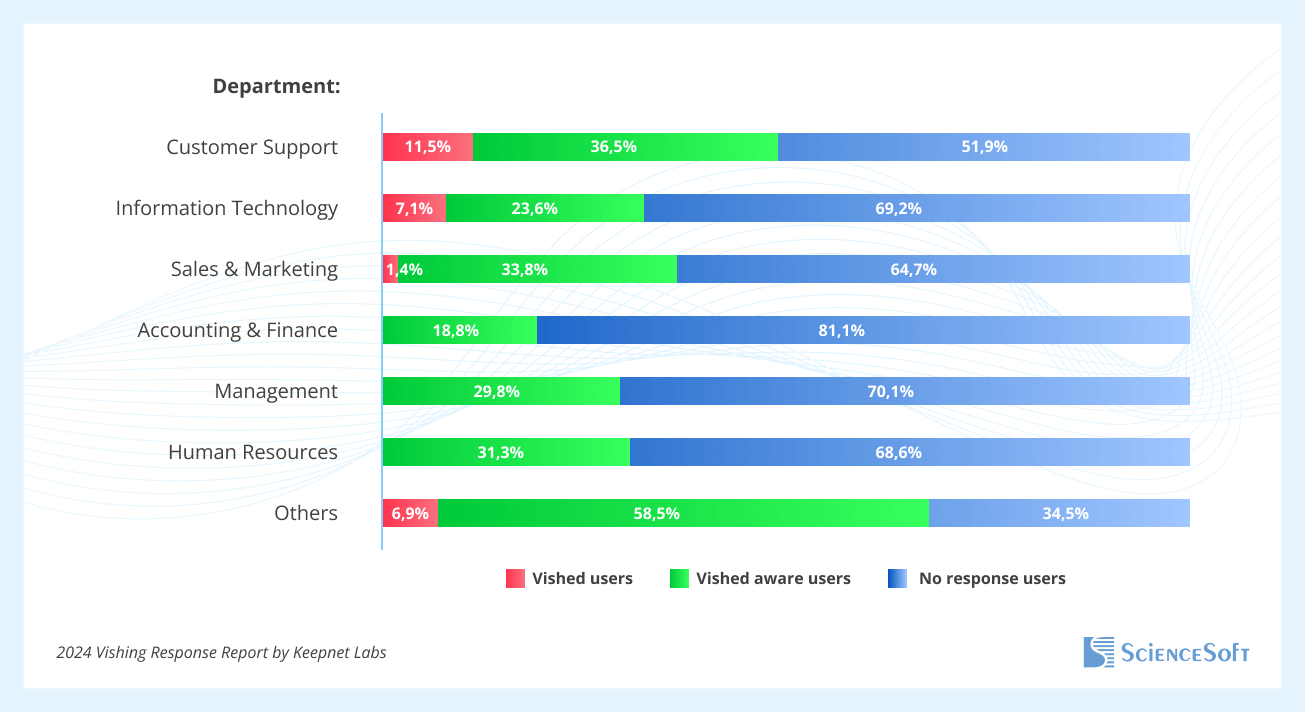
The Keepnet Labs report also shows that the healthcare industry has the lowest proportion of vishing-aware users, i.e., those who successfully recognized a vishing attempt and responded appropriately by withholding information or terminating the call to safeguard security. At the same time, the TransUnion survey found that 90% of respondents from the financial industry report an increase in call center fraud attacks.
Taking into account these trends, ScienceSoft’s security experts recommend paying special attention to the vigilance of call center employees and applying context-aware vishing scenarios when targeting call centers in high-risk industries. Below, our cybersecurity team shares some examples of vishing attack scenarios for finance and healthcare.
Vishing test scenarios for call centers in banking and finance
Bank account takeover attempt
In this scenario, the caller tries to persuade the call center agent to reset the account password or transfer funds to a fraudulent account. This checks whether the agent would follow all the required protocols even when the caller appeals to urgency or emotion.
Internal fraud pretext
This scenario involves posing as an authority figure (e.g., the company's top management or CEO) to trick your employees into violating security protocols, such as approving a wire transfer without following the usual verification steps.
Vishing test scenarios for healthcare call centers
Pretend physician query
The scenario checks if the staff will release protected health information (PHI) without proper authorization when a caller claims to be a physician.
Family member impersonation
This scenario tests the employees' ability to balance compassionate customer service with strict data protection protocols.
Insurance provider follow-up
A healthcare employee gets a call from an “insurance company” requesting information for claim processing. This scenario checks if employees release patient or billing details without proper verification.
Why Partner With ScienceSoft for Vishing Testing
- Since 2003 in cybersecurity.
- Hands-on experience with PCI DSS, NIST SP 800-53, HIPAA, FINRA, NYDFS, SOC 2, GDPR, and other security standards and regulations that require or recommend social engineering testing.
- A solid portfolio of security testing and consulting projects for companies in BFSI, healthcare, manufacturing, retail, and other industries.
- Competent multiskilled team: Certified Ethical Hackers, compliance consultants, SIEM/SOAR/XDR specialists, ITIL-certified specialists, certified ITSM Professionals, and other experts.
- Ready to sign an NDA (Non-Disclosure Agreement) before the first contact call to ensure the legal protection of your confidential information.
- Ready to sign a BAA (Business Associate Agreement) with clients who are subject to HIPAA.
Scalable Security Testing: Choose Your Campaign
Vishing
During a call-only campaign, our team will assess how well your company can withstand vishing attacks.
Phishing and vishing
Attackers often use blended methods, so using a combined approach (calls and emails) provides a holistic view of social engineering readiness.
Red team campaign
By combining social engineering and penetration testing, we can evaluate how well your company can withstand a multi-layered attack.
Vishing Testing Costs and Cost Factors
The price of a vishing testing project at ScienceSoft generally starts from $6,000 for a project targeting less than 100 employees. The exact figure will vary depending on the scope and complexity of each project. It is also affected by the following factors:
- The number of targeted employees and the diversity of their roles within the organization.
- The required number of testers and their qualifications.
- The specificity of the target organization’s industry when it comes to common vishing scenarios and regulatory limitations.
- Whether additional security assessments or tests are required (e.g., phishing, network penetration testing).
- Whether the client requires assistance with the remediation of security gaps or employee training.
Wondering How Much a Vishing Test Will Cost You?
Answer a few simple questions about your security testing needs. This will help our team calculate the cost for your unique case much quicker.
Thank you for your request!
We will analyze your case and get back to you within a business day to share a ballpark estimate.
In the meantime, would you like to learn more about ScienceSoft?
- 22 years in cybersecurity: check what we do.
- 4,200+ successful projects: explore our portfolio.
- 1,400+ incredible clients: read what they say.






