How to Support Healthcare IT Compliance with Data Security Measures
Editor’s note: Gala highlights top security threats in healthcare, core ePHI protection regulations, and measures that help meet healthcare IT compliance requirements. If you need a compliance assessment of your organization’s healthcare systems or plan to develop secure and compliant healthcare software, ScienceSoft’s healthcare IT consulting team is here to help.
The state of healthcare data security in 2024 remains deeply troubling, with record-breaking numbers of patient records compromised and escalating financial consequences. In 2024, the HHS Office for Civil Rights (OCR) tallied 734 major data breaches (affecting at least 500 patient records). That’s slightly lower than the all-time high of 747 breaches in 2023, but the number of individuals affected soared — over 275 million patient records were compromised, compared to 168 million in 2023. The Change Healthcare attack alone hit over 110 million people, meaning 1 in 3 Americans.
According to the IBM report, the average cost per breach incident in healthcare was nearly $11 million in 2023. OCR penalties for HIPAA violations also rose, with nearly $12.8 million collected in 2024, compared to $4.18 million in 2023. The OCR announced its intention to resume HIPAA audits at the end of 2025. Yet, a recent survey found just 39% of healthcare providers felt “very prepared” for HIPAA audits.
Top Healthcare Data Security Threats
To ensure compliance and safeguard sensitive information in healthcare IT systems, it's crucial to be aware of the most pressing cybersecurity threats affecting healthcare organizations. Here are some of the most common threat types.
- Ransomware: Criminals encrypt or steal sensitive patient data and demand payment in exchange. Healthcare organizations often end up having to pay. A recent study found that 67% of the surveyed healthcare organizations faced ransomware attacks in 2024. The 2024 Change Healthcare attack, which I previously mentioned, is a striking example. Hackers encrypted the records of 110 million patients, so Change Healthcare’s systems were blocked for several weeks, and they had to pay a $22 million ransom to prevent the patient data from being published. Cyberattacks involving ransomware can result in significant financial losses, including lost revenue due to system downtime, payments demanded by attackers, and high expenses associated with restoring systems and data.
- Insider threats: Protected health information (PHI) gets stolen, accessed without authorization, or disclosed because of employees within a healthcare organization or its third-party vendors who have access to patient data. Insider breaches may happen due to unintentional errors or negligence in managing patient records, or they may be malicious, with staff stealing sensitive healthcare data, which is highly valuable on the black market. Without ongoing data access monitoring, insider-related incidents are hard to prevent. According to the Verizon report, in 2024, insiders were responsible for 70% of data breaches.
- Phishing and social engineering: Hackers target an organization’s staff via email or social platforms. Their goal is typically to trick victims into giving up their business credentials or installing ransomware. This is the most common entry point for hacking, with phishing involved in over 90% of cyberattacks.
- Third-party compromise: Attacks target software vulnerabilities found in the systems of vendors, partners, or suppliers connected to a healthcare organization’s IT ecosystem. For example, a widely used healthcare scheduling or image-processing app, once compromised, can affect multiple hospitals at once. According to the Forescout report, third-party compromises as the second most common hacking method after ransomware. That’s why HIPAA and other data privacy regulations require healthcare organizations to carefully evaluate the cybersecurity of all vendors that gain access to PHI. It is also mandatory for healthcare providers to sign Business Associate Agreements (BAAs) with all vendors that handle PHI.
- Medical IoT and cloud software vulnerabilities: Among other common entry points used by hackers, it's worth mentioning IoT devices (heart monitors, infusion pumps, wearables for remote patient monitoring, etc.), misconfigurations in cloud systems (e.g., overprivileged accounts or open AWS buckets) and known software vulnerabilities that weren’t patched in time. An attacker who breaches through these weak points can then move laterally into critical systems, especially in unsegmented networks, where there are no barriers limiting access to other parts of the infrastructure.
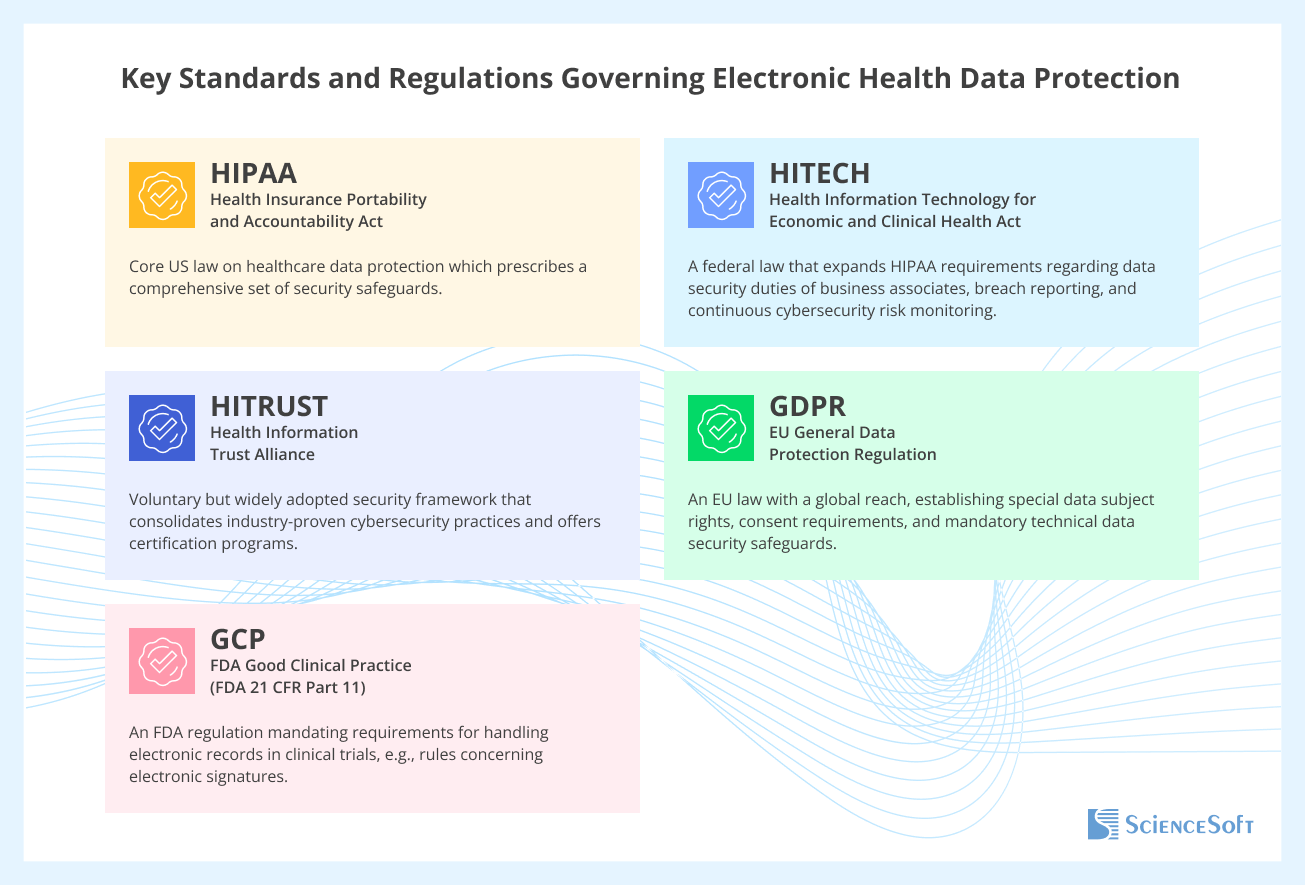
Healthcare Data Security Compliance: Main Regulations and Standards
Inadequate PHI protection incurs reputational and financial risks for healthcare providers due to potential data breaches, but, above all, it's a matter of regulatory non-compliance that may result in sanctions from national health authorities. In the USA, healthcare software has to be HIPAA-compliant, but there are also other overlapping regulations and standards that mandate patient data security controls. Let’s look at them a bit closer.
HIPAA: Health Insurance Portability and Accountability Act, 1996
HIPAA is a US federal law applicable to any entity handling PHI, including healthcare providers, insurers, clearinghouses, and their business associates (any partners, suppliers, and service providers who receive, maintain, or transmit electronic PHI). The HIPAA Security Rule includes a detailed description of the administrative, physical, and technical safeguards that must be implemented, including security measures for ePHI stored in software systems (such as access control, data encryption, and audit logs).
HITECH: Health Information Technology for Economic and Clinical Health Act, 2009
HITECH is another US federal law that incentivizes the adoption of electronic health records (EHR) and strengthens the healthcare data privacy and security provisions of HIPAA. Specifically, it places direct responsibility for health data compliance on business associates, subjecting them to equal civil and criminal penalties in the event of non-compliance. It also requires reporting data breaches to patients, the Department of Health and Human Services (HHS), and the media, and mandates regular risk assessments to identify software vulnerabilities.
HITRUST: Health Information Trust Alliance (HITRUST) Common Security Framework (CSF)
HITRUST isn’t a law, but rather a popular healthcare security compliance framework that is based on over 60 security and privacy regulations, standards, and frameworks, including HIPAA, ISO 27001, and NIST. It helps organizations systematically implement the industry's best practices for cybersecurity and HIPAA compliance. For example, it prescribes control objectives that healthcare software must meet (regarding encryption, logging, change control, etc.). HITRUST is regularly updated to maintain the effectiveness of its security controls against the evolving cybersecurity threats. Many healthcare providers pursue HITRUST certification to demonstrate that their IT environments comply with HIPAA requirements and guarantee maximum data security.
GDPR: EU General Data Protection Regulation
GDPR is an EU law with extraterritorial effect, which means it applies whenever personal data of EU residents (including health data) is processed. For example, suppose a US telemedicine provider delivers services to EU patients or collects and processes their data. In that case, the provider must comply with both GDPR and HIPAA requirements, including different breach notification and patient consent rules. As for the provider’s software, it must be designed to support GDPR data subject rights (e.g., the ability to withdraw consent, delete data, or restrict its use) and comply with specific security requirements (e.g., related to data minimization and encryption).
GCP: FDA Good Clinical Practice
GCP is an FDA regulation that applies to pharmaceutical and medical device companies involved in clinical research. It is primarily aimed at ensuring the quality of biopharmaceutical and medical products. To some extent, GCP and HIPAA intersect in their requirements for handling patient data in clinical trials. These GCP requirements are outlined in FDA 21 CFR Part 11 (Electronic Records). Under these requirements, clinical trial software must undergo system validation, restrict access to clinical data to authorized users only, maintain secure, time-stamped audit trails, and retain clinical records for a specified period.
Data Security Measures to Implement
To comply with regulations and protect sensitive patient information from unauthorized access, healthcare software has to include the following essential data security safeguards.
Data encryption
Software used by healthcare organizations should provide data encryption capabilities to prevent unauthorized parties from altering, destroying, or profiting from sensitive information. It’s important to take into account that the encryption of data at rest can reduce the performance of a healthcare application. To solve this problem, you can apply file-level and block-level encryption. As for data encryption in transit, it doesn't affect application performance in a way that users notice.
Data access control and user authentication
Restricting access to medical applications based on user roles (e.g., administrator, patient, doctor) helps protect the personal data of patients and medical personnel from unauthorized access. Different access rights can be granted to each user or user role, including full or limited rights to read, modify, or delete information. User authentication measures help check a person’s identity before granting them access to ePHI. One of the typical authentication mechanisms used for PHI protection is multi-factor authentication, which requires not only a password but also a fingerprint or a unique login code before granting user access.
Internal IT security audit
To ensure the security of medical applications, IT infrastructure, and all the transmitted and stored data, a healthcare organization should plan and conduct regular vulnerability assessments and penetration testing of the relevant IT infrastructure components and software.
Integrity controls
When implementing healthcare software, a healthcare organization should establish policies and procedures for protecting ePHI against alteration or destruction.
Transmission security
When ePHI is transmitted over an electronic communications network, it should remain inaccessible to third parties. To guard the data from unauthorized access, ePHI should be transmitted using a secure protocol and over a secure network connection.
Continuous security logging and monitoring
Every action involving ePHI, including access, modification, deletion, copying, or transfer, must be recorded to enable the detection of suspicious activity, such as repeated login failures or large data transfers. All the logs are typically consolidated in a Security Information and Event Management (SIEM) system. Modern SIEM systems can be enhanced with AI/ML capabilities to spot subtle signs of threats by detecting unusual patterns in user or system behavior.
Regular risk assessments
Ensuring HIPAA compliance also requires proactive security measures, such as conducting regular risk assessments. A comprehensive HIPAA risk assessment may include evaluating existing security policies and procedures, assessing employee security awareness, and performing technical security testing on software and IT infrastructure that handle PHI. Tools like the HHS SRA or third-party audit platforms can support this process. The assessment must be conducted at least annually and following any significant software or infrastructure changes.
Ensure Compliance of Your Healthcare Organization!
Failure to comply with regulatory requirements can result in significant financial and reputational losses for a healthcare organization. If you need professional assistance in any aspect of developing and implementing HIPAA-compliant software, ScienceSoft’s healthcare IT consultants are here to help!

