HIPAA Risk Assessment
Plan, Skills, Costs and Tools
Since 2005 in healthcare IT and since 2003 in cybersecurity, ScienceSoft helps healthcare providers and digital health companies keep PHI safe and stay HIPAA-compliant.
HIPAA Compliance Risk Assessment in Brief
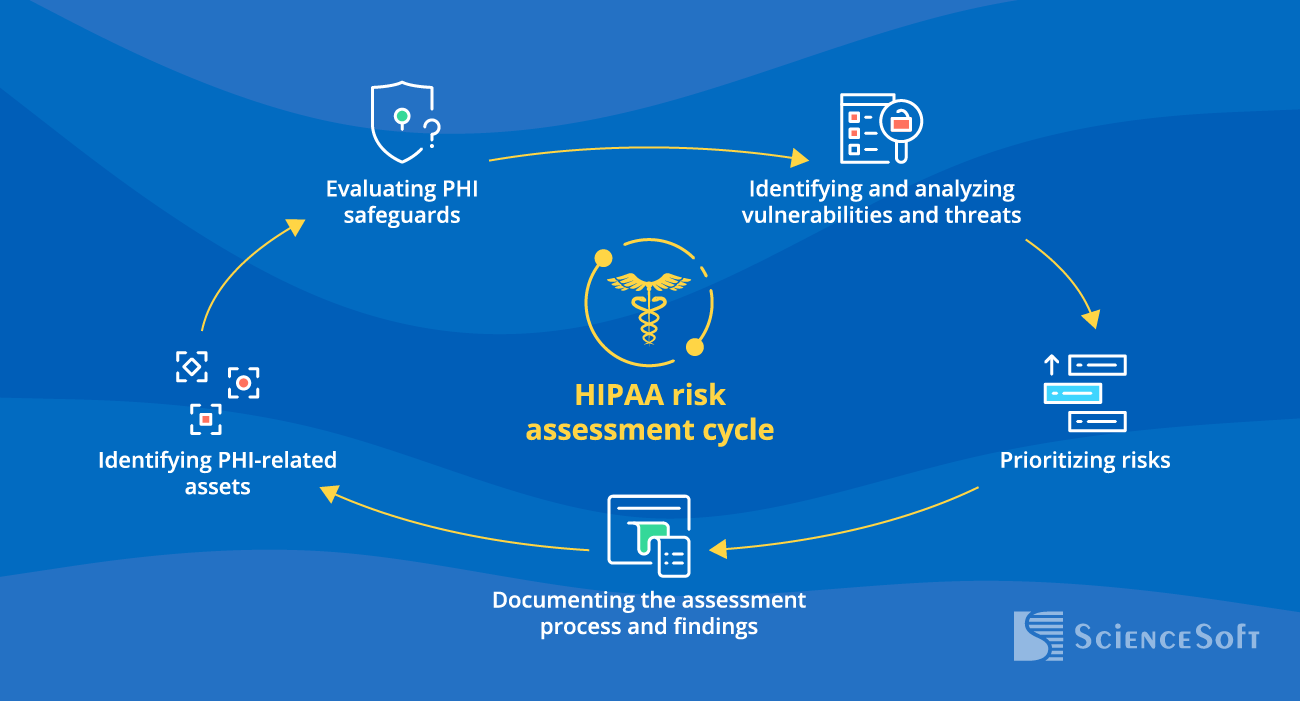
A HIPAA risk assessment identifies vulnerabilities in handling protected health information and evaluates the potential risks associated with unauthorized access, use, or disclosure of PHI.
A HIPAA risk assessment helps healthcare providers and business associates, such as IT contractors, billing companies, accounting service providers and others, evaluate PHI protection and get ready for an OCR audit. Healthcare software product companies and medical device manufacturers can benefit from HIPAA compliance assessment to be sure that their products meet HIPAA requirements before they enter the market.
- A HIPAA compliance risk assessment may include: review of established security policies, procedures, and employees’ security awareness; security testing of software and IT infrastructure involved in storing, processing, transmitting or protecting PHI.
- Steps of a HIPAA risk assessment: planning; resources preparation (assembling an in-house assessment team and preparing required tools or choosing a third-party service provider); assessment launch and execution.
- Assessment team roles: project manager, HIPAA compliance consultant, security testing engineers.
The Risks of HIPAA Breaches
Financial damage
- Regulatory fines.
- Legal expenses.
- Compensation to affected patients.
- Breach recovery expenses.
- Revenue loss stemming from operational downtime.
Reputational damage
- Diminished customer loyalty.
- Missed business opportunities due to decreased trust among investors and business partners.
- Negative healthcare outcomes if patients become reluctant to share health info due to security concerns.
|
|
|
|
|
|
|
|
|
Steps to Perform HIPAA Compliance Risk Assessment
A comprehensive evaluation of HIPAA compliance may require different activities, depending on the type of healthcare services a company provides, the size of the company and its structural complexity, or (for healthcare technology vendors) the nature and complexity of a product. ScienceSoft lists the generally applicable guidelines on how to strategize, prepare resources for and carry out an efficient HIPAA compliance risk assessment.
1. Planning
Duration: 2-3 weeks
- Creating a checklist of security measures for PHI protection applicable for your company. You need to consider the following administrative, technical and physical security controls aimed to ensure PHI protection in line with HIPAA Security Rule and HIPAA Privacy Rule.
Administrative safeguards
- Security management: PHI risks assessment, risk mitigation and incident response plans.
- Security personnel: a security official responsible for developing and implementing security policies and procedures.
- Information access management: ensuring against unauthorized or unnecessary use and disclosure of PHI.
- Workforce management and training: appropriate authorization and supervision of employees; promoting their understanding of existing security policies and procedures.
- Continuous evaluation of security policies and procedures implementation.
Technical safeguards
- Access control: user authorization, password management, automatic log-off.
- Transmission security: encryption of transferred sensitive health data.
- Audit controls: monitoring and logging of all the activities involving PHI.
- Integrity controls: prompt detection of security breaches and protective measures against PHI theft or unauthorized modification.
Physical safeguards
- Facility access controls: restricted access to the facilities containing PHI.
- Workstation and device security measures.
- Identifying applications, databases, and network components that contain, transmit or protect PHI.
- Listing the staff members and business associates who have access to your company’s PHI.
- Estimating financial, time and human resources required for the risk assessment.
- Developing a risk mitigation strategy to deal with unintentional data exposure, downtime, lack of access to the IT infrastructure related to the assessment activities.
2. Resources preparation
ScienceSoft’s experts outline common preparation steps for in-house and outsourced projects.
3. Launch and execution
Duration: up to 10 weeks
To check if a company’s security policies and procedures meet HIPAA requirements, ScienceSoft’s compliance consultants recommend:
- Scrutinizing documentation on all security controls and activities related to PHI protection: risk analysis, breach notification, incident management, HIPAA training for employees, previous security testing for vulnerabilities, etc.
- Interviewing the staff to understand their security awareness level.
To see if the company’s software and IT infrastructure have security loopholes that can endanger PHI, ScienceSoft recommends:
- Running automated vulnerability scanning to find potential entry points to access sensitive health information.
- Reviewing the software architecture and source code for vulnerabilities that can endanger PHI protection.
- Exploiting vulnerabilities and simulate hackers’ attacks to access PHI.
|
|
Best practice: Security testers should try to find out how potential hackers can hide trace of their unauthorized presence in the IT environment. It will help devise measures to avoid a repeated intrusion. |
- Preparing a final report that covers:
- HIPAA compliance assessment scope: e.g., documents on security policies and procedures aimed at PHI protection, components of the IT environment involved in operations with PHI, staff members that have access to PHI.
- Gaps in security policies and procedures or employees' knowledge that can be fraught with PHI exposure.
- Security testing methodology and tools used during the assessment, detected vulnerabilities in software and IT infrastructure endangering PHI, their nature, severity and probability of exploitation.
- Corrective measures for all deviations from HIPAA requirements at administrative, technical and physical levels.
HIPAA Risk Assessment Services by ScienceSoft: We Step In Where You Need Us
We offer expert guidance and end-to-end HIPAA compliance assessments to help protect sensitive health data according to the CIA triad principles. Team up with ScienceSoft to safeguard your information's confidentiality, maintain its integrity, and ensure its availability whenever you need it.
HIPAA risk assessment planning
- Outlining HIPAA requirements applicable for your case.
- Determining the assessment scope: IT assets, users, and security controls to check.
- Defining the required steps.
- HIPAA risk assessment cost calculation.
HIPAA security risk assessment
- Defining the scope based on your company’s type, size, structure, and IT environment.
- Working out an optimal assessment plan.
- Evaluating security policies, procedures, and technology.
- IT infrastructure and application security testing to locate and explore vulnerabilities that may endanger PHI security.
- A detailed report with corrective measures to achieve HIPAA compliance.
HIPAA Risk Assessment Checklist
Use the questionnaire prepared by our experts to evaluate your level of HIPAA breach risk.
Inventory management
Do you keep an up-to-date list of applications, IT infrastructure components, employees, and business associates involved in handling PHI?
Secure operations with PHI
Have you implemented measures for secure storage and disposal of PHI (e.g., data backups, encryption, secure destruction policies and procedures)?
Secure operations with PHI
Have proper authorization and authentication mechanisms been implemented to secure access to PHI?
Secure operations with PHI
Do you use strong encryption and secure communication channels to safeguard PHI transmission?
Secure operations with PHI
Is there continuous logging and monitoring to audit operations involving PHI?
Employee training
Have you provided HIPAA training to all employees who handle ePHI?
Employee training
Have you checked if your employees understand their responsibilities in protecting ePHI?
Vendor and business associate management
Have you assessed the security practices of your vendors and business associates?
Vendor and business associate management
Do you have written agreements with business associates that define their responsibilities for ePHI security?
Incident response and breach notification
Do you have a documented incident response plan in case of a security breach?
Incident response and breach notification
Have you tested your incident response plan to validate its effectiveness?
Incident response and breach notification
Do you have a process to assess and report breaches of ePHI?
Threat and vulnerability management
Do you regularly identify potential internal and external threats to ePHI security?
Threat and vulnerability management
Do you regularly test and review your security technology, policies, and procedures?
Threat and vulnerability management
Do you promptly apply necessary fixes and update your security policies and processes?
Oops...
Sorry, we can't provide the results, unless you answer the questions.
Low risk
Congratulations! Your dedication to safeguarding sensitive health information helps keep the risk of HIPAA breaches low. Team up with ScienceSoft to uphold the highest standards of data protection.
Moderate risk
Your HIPAA compliance efforts show positive outcomes. However, there are vulnerable areas that could potentially result in data breaches. Turn to ScienceSoft to get expert HIPAA gap analysis and remediation.
High risk
Don't let PHI threats evolve into devastating data breaches. Turn to ScienceSoft to promptly level up your data protection and achieve HIPAA compliance.
Talents Required for HIPAA Security Risk Assessment
Project manager
- Plans a HIPAA compliance assessment, calculates costs and estimates time and human resources needed.
- Monitors and coordinates the assessment process.
- Ensures smooth communication between the stakeholders and the assessment team.
HIPAA compliance consultant
- Defines HIPAA requirements applicable for a specific company.
- Reviews security policies and procedures related to PHI protection to detect and document deviations from HIPAA regulations, if any.
- Interviews employees to check awareness of HIPAA requirements and IT security measures.
- Recommends a remediation plan for the company to become HIPAA-compliant.
- Helps prepare or improve documentation on security policies and procedures aimed at HIPAA breach prevention or remediation (incident response plan, risk assessment report, breach notification plan, etc.).
Security testing engineers
- Run automated vulnerability scanners on software, networks or devices involve in operations with PHI.
- Review software architecture and source code to find the flaws that can undermine PHI security.
- Perform white box/gray box/black box penetration testing to find out the most probable ways to steal or modify PHI.
- Advise on fixing the detected gaps to protect PHI.
Why Businesses in Healthcare Choose ScienceSoft
- 22 years in cybersecurity, a solid portfolio of successful projects.
- Multiskilled team, including Certified Ethical Hackers, certified cloud experts, compliance consultants, developers with experience in secure software development.
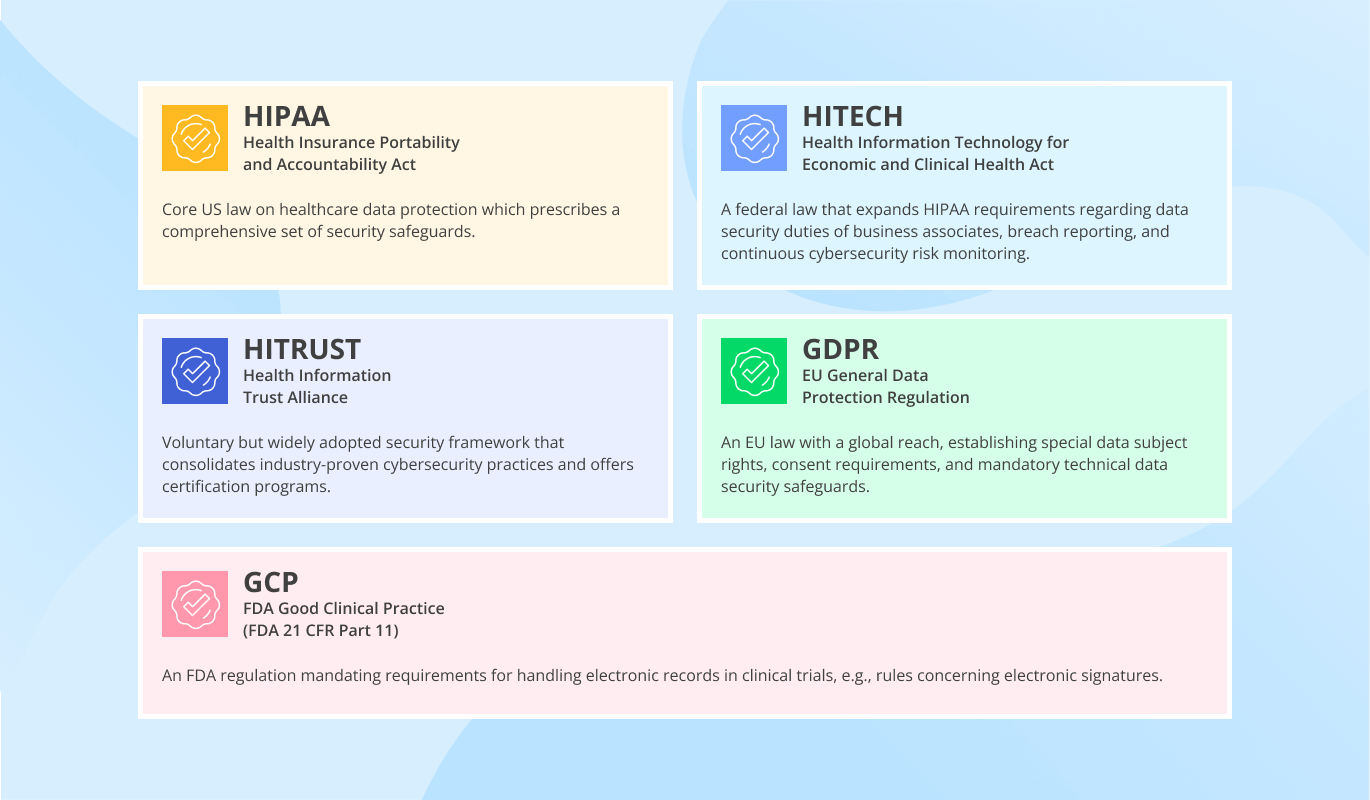
- Equipped with NIST, CIS, OWASP, PTES, and other security best practices.
- Risk assessment based on NIST SP 800-37, ISO 27005, and ISO 31000 standards.
- ISO 27001-certified security management based on field-tested security knowledge, comprehensive security policies, and well-coordinated security teamwork.
- Since 2005, empowering healthcare businesses with software development and IT services.
- Mature quality management system for medical devices and SaMD backed up by ISO 13485 certification.
- ISO 9001-certified to ensure the tangible value of our services, predictable results, and cost optimization that doesn't happen at the expense of quality.
Sourcing Models for HIPAA Risk Assessment
HIPAA compliance self-assessment
- No need to let third parties access your IT environment and sensitive health data.
- The assessment team is familiar with your healthcare service/product and activities involving the use of PHI.
- Possibility to regularly check HIPAA compliance as your corporate infrastructure grows or changes.
- The need to build up a qualified team, including security testing engineers knowledgeable about HIPAA requirements.
- Heavy expenses on salaries and maintenance.
Third-party HIPAA compliance assessment
- An impartial evaluation.
- Expert understanding of complex HIPAA requirements.
- Availability of all the necessary talents for an all-around HIPAA compliance assessment.
- The vendor takes over responsibility for all stages of the HIPAA risk assessment.
- Risks associated with sensitive data exposure.
- The vendor will need time to understand your internal processes and IT infrastructure.
Compliance manager is in-house; security testing team is completely or partially external
- You get skilled compliance talents, while preserving sufficient control over the assessment process.
- Difficulty with finding a knowledgeable in-house compliance manager.
Compliance Assessment Tools Our Team Relies On
Along with manual techniques that we apply to detect compliance gaps, we choose tried-and-true tools to explore weaknesses in software and IT infrastructure.
Vulnerability assessment and penetration testing
Secure code review
Smart contract security review
Common Questions about HIPAA Security Risk Assessment
HIPAA risk analysis vs. risk assessment: what's the difference?
HIPAA risk analysis is a component of the broader risk assessment process. HIPAA risk assessment includes scoping the elements of the IT environment and users involved in handling PHI, conducting security testing, reviewing policies, and generating reports. The specific task of risk analysis is evaluating the probability of threats considering the existing vulnerabilities, as well as assessing the potential impact of a security incident.
Is it mandatory to undergo HIPAA security risk assessment every year?
While HIPAA doesn't specify a required frequency, many organizations find it beneficial to perform annual risk assessments. This practice helps ensure ongoing compliance and keep the risk management strategy up-to-date. We also recommend considering comprehensive risk assessment in the following cases:
- Whenever significant modifications occur in your IT infrastructure, applications, or data flows, it's wise to conduct a risk assessment to identify and mitigate any new risks that might arise due to these changes.
- After a security incident, a prompt HIPAA breach risk assessment will provide insights into the breach causes and help identify preventive measures to avoid similar incidents.
- If HIPAA regulations change, a risk assessment will help you adapt to the new requirements and stay compliant.
What should be included in a HIPAA security risk assessment report?
A HIPAA compliance risk assessment report should be informative, actionable, and easy to understand for technical and non-technical stakeholders. The key components of such a report are the following:
- Concise overview of the assessment's process and findings.
- Targets in scope.
- Employed techniques and tools.
- PHI safeguards in place.
- Potential threats and existing vulnerabilities.
- Prioritized risks.
- Specific measures to address identified risks and vulnerabilities.
HIPAA Risk Assessment Costs
The cost of HIPAA compliance risk assessment depends on the following factors:
- The number and complexity of the targets in scope: documents on PHI protection, the networks and applications involved in operations with PHI, etc.
- The diversity and complexity of applied testing types and techniques: e.g., automated vulnerability scanning, manual penetration tests, black/gray/white box pentesting, security code review, social engineering.
- The efficiency of the vendor’s HIPAA compliance team (in case of a third-party assessment).
- The license costs of scanning and pentesting tools (if these activities are performed in-house).

Depending on the factors described above, HIPAA risk assessment activities may cost anywhere from $4,000 to $50,000.
Sample price: Black box network vulnerability testing of up to 200 IPs as part of HIPAA security assessment may cost $5,000+.
Would you like to find out the cost of your HIPAA risk assessment?

About ScienceSoft
ScienceSoft is a global provider of IT consulting, software development, and cybersecurity services headquartered in McKinney, TX. Since 2005, we've been delivering services for the healthcare industry with a special attention to PHI protection. ISO 9001 and ISO 13485 certifications prove our ability to build mature quality management systems. Being ISO 27001-certified, we guarantee the security of our clients’ data. If you need help with evaluating your HIPAA compliance, you are welcome to contact our team.