Medical Device Cybersecurity Assessment
Guaranteeing Secure Healthcare Technology
With over 20 years of experience in cybersecurity and healthcare IT, ScienceSoft evaluates the security of medical devices, SaMD, and connected device networks. We go beyond surface-level checks to uncover even complex issues and deliver a full account of device cybersecurity and an actionable remediation plan.
Medical device cybersecurity assessment helps medical device manufacturers reveal security gaps in their products before they go on the market, ensuring their safety in the long run, as well as a part of the postmarket management strategy. For healthcare providers, it is a way to verify that the medical devices they employ don’t contain vulnerabilities that could compromise healthcare operations, patient safety, and sensitive data privacy.
Medical Devices and Software We Assess
ScienceSoft finds and helps remediate security issues in connected medical devices as well as software as a medical device (SaMD). This includes:
Class II Medical Devices
- Medical imaging devices: e.g., ultrasound, MRI, and CT scanners.
- Monitoring and diagnostic devices: e.g., wearable spirometers, hemodynamic/pressure monitoring devices, ECG patches.
- Treatment devices: e.g., anesthesia machines, insulin pumps, smart insulin pens, hemodialysis machines, smart intravenous infusion pumps.
Class III Medical Devices
- Implants: e.g., pacemakers, cardioverter-defibrillators, cochlear implants, neural prostheses.
- Emergency and intensive care devices: e.g., cardiac ablation systems, high frequency ventilators.
- Critical obstetric electronic devices: e.g., obstetric data analyzers, fetal EEG monitors.
SaMD (Class I, II, III)
- Software for monitoring and diagnostics: e.g., image recognition software for stroke type identification or cancer tumor localization.
- Software for treatment and disease management: e.g., medication dosing calculators, apps for identification of sleep apnea episodes, AI-driven solutions for disease treatment and patient care planning.
Security Assessment Approaches We Are Confident In
Deliverables You Get Upon Medical Device Cybersecurity Assessment
For devices at any stage of their lifecycle
We provide:
- Security audit reports.
- Vulnerability assessment reports.
- Penetration testing reports.
- Summary of the risk assessment conclusions, including the control level of the revealed risks.
In these reports, we include:
- A summary of the detected flaws, vulnerabilities, risks, compliance gaps.
- Remediation guidelines.
For device premarket submission
To help ensure continuous safety and effectiveness of a medical device, we offer:
- A detailed description of the security controls in place to ensure that the device will maintain its integrity from the point of origin to the point where it leaves the control of the manufacturer.
- A plan for security updates and patches throughout the medical device lifecycle.
- Guidelines on the cybersecurity controls for the intended use environment (e.g., how to place and configure security tools such as antivirus software, firewalls, SIEM).
For devices on the market
If vulnerability remediation resulted in changes to the device software, they need to be reported to FDA or a Notified Body designated under MDR/IVDR. In this case, we provide:
- Detailed description of the vulnerability and the changes made to the device, including the comparison between the current and the previously approved version of it.
- The rationale for making the changes.
- References to other devices that were modified in response to the same vulnerability.
ScienceSoft as a Responsible Healthcare Security Partner
Decades-long experience
- 36 years in IT.
- 22 years in the cybersecurity domain.
- 20 years in healthcare IT.
- 14 years in IoT.
- 13 years in cloud services.
Proven expertise in healthcare security
- A solid portfolio of 150+ successful projects in the healthcare IT domain.
- 200+ implemented projects in cybersecurity.
Consistency in service quality
- Established quality management system for medical devices and SaMD confirmed by ISO 13485 certification.
- ISO 9001-certified to guarantee quality performance and timely project delivery.
- ISO 27001 certification ensuring full security of the sensitive data entrusted to us.
Doubtful About Cybersecurity Assessment for Your Healthcare Device? Let Us Dispel Your Concerns
With so many regulations that may apply to one medical device — FDA, MDR/IVDR, HIPAA, GDPR — can you help prevent all possible compliance breaches?
As an ISO 13485-certified tech partner, we know how to meet the requirements of the FDA and the Council of the European Union. We have hands-on experience with HIPAA and GDPR compliance. Our team of regulatory consultants, security engineers, and healthcare software developers can evaluate, implement, or improve the administrative and technical safeguards as required by these regulations. We are also ready to guide you through HIPAA/GDPR risk assessment and FDA/CE/MDR/IVDR submission process.
A high-level security assessment of our medical device is not enough. Will we get actionable insights to promptly address the assessment findings?
Our security assessments are result-oriented and focused on providing valuable deliverables. The transparent documentation we create helps with market registration, becomes a part of the post-market vulnerability management strategy, and drives the necessary remediation activities.
We Are Here for You at Any Stage of Your Device Life Cycle
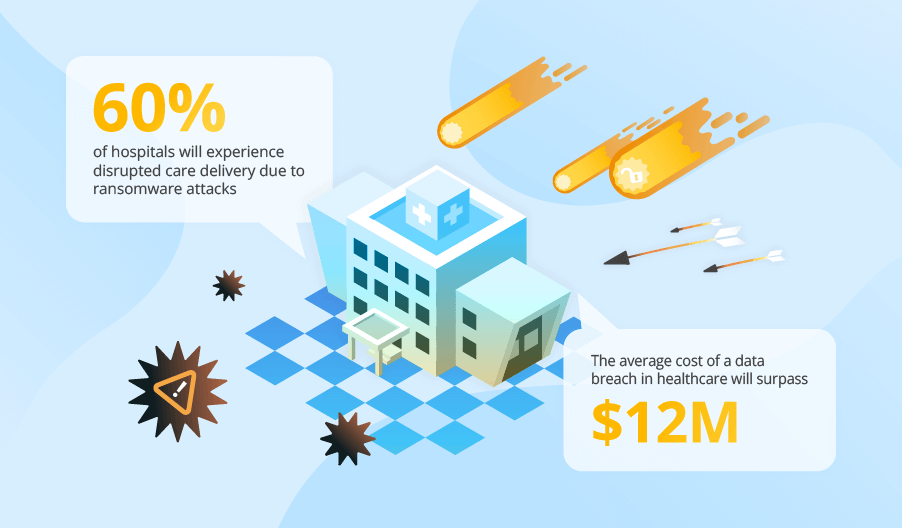
Medical Device Security Statistics You Can’t Ignore
|
93% of healthcare organizations experienced at least one cyberattack in 2025 (Proofpoint). |
99% of hospitals and HDOs are managing IoMT devices with known exploited vulnerabilities (KEVs) in 2025 (Claroty). |