Penetration Testing Services
Pinpointing Vulnerabilities Before Hackers Find Them
With 20 years in cybersecurity, ScienceSoft offers penetration testing services to detect and help eliminate dangerous vulnerabilities. Equipped with OWASP and NIST best security testing practices, our Certified Ethical Hackers confidently handle apps and networks of any complexity.
Penetration testing is imitating the techniques a real-world attacker would use to get hold of a company's data, apps, or IT infrastructure. Penetration testing services aim to identify security flaws in an IT environment, evaluate their potential impact, and offer remediation guidance.
To ensure businesses derive the maximum benefit from penetration testing, ScienceSoft's ethical hackers guarantee:
- A tailored approach to the needs of each customer.
- An optimal blend of automated tools and manual testing techniques.
- Full transparency and support throughout the testing process.
What We Test
Software
We unearth security flaws in the architecture, code, and business logic of applications, including those based on blockchain, cloud, AI, AR/VR and other advanced techs.
- Websites and web portals.
- Web applications.
- Mobile applications.
- APIs.
- Desktop applications.
Our firm helps prevent modern network security risks, including those related to remote work, cloud migration, IoT devices, and BYOD policy.
- Endpoints: PCs, laptops, mobile devices.
- Networking devices and network management tools.
- Email services.
- Security solutions: firewalls, VPN, IAM, DLP systems, and more.
Data security
We reveal security flaws that may enable unauthorized access to sensitive and business-critical data on premises and in the cloud.
- Data storage.
- Data encryption.
- Data in transit.
Cybersecurity awareness
We identify unsafe user behavior and the lack of knowledge about applicable security and compliance requirements.
- Employees.
- C-suite.
- Vendors and partners.
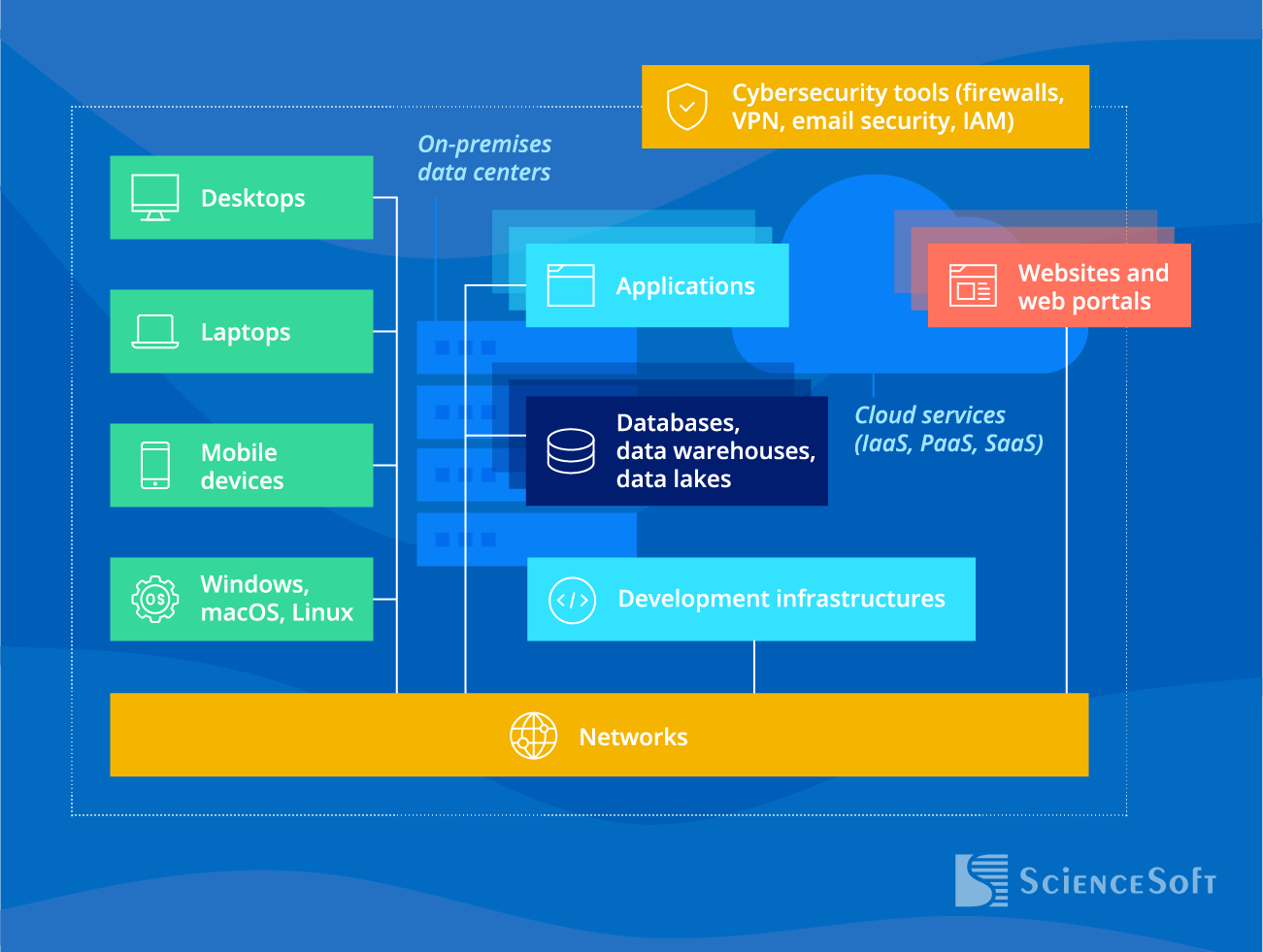
We recommend performing a third-party penetration testing, if:
- Regular security checkups are required by applicable standards and regulations.
- New IT infrastructure components or applications were added.
- Significant upgrades or modifications of your IT infrastructure or applications were made.
- New office locations were established.
- End-user policies were modified.
Penetration Testing Services: Success Stories by ScienceSoft
Why Businesses Choose ScienceSoft as Their Penetration Testing Company
Trusted by famous brands
Expert team
- Certified Ethical Hackers, experienced security engineers, and compliance consultants on board.
- A solid portfolio of successful projects for companies in BFSI, healthcare, manufacturing, retail, and other industries.
- Adherence to the best security testing practices outlined by NIST SP 800-115, OWASP Web Security Testing Guide, and other frameworks.
- Hands-on experience with HIPAA, PCI DSS/SSF, GDPR, SOC 2, NIST SP 800-53, GLBA, and other security standards and regulations.
- Addressing the unique needs of different businesses: the security of remote access, payment gateways, cloud components, IoT devices, blockchain-based or AI/ML-powered solutions, and more.
Certificates and recognitions
- Recognized among the Top Penetration Testing Companies by Clutch.
- An ISO 9001-certified service provider to guarantee smooth cooperation and value-driving results.
- 100% security of our customers' data ensured by ISO 27001-certified security management system.
- A leading outsourcing provider according to IAOP.
-
For the second straight year, ScienceSoft USA Corporation is listed among The Americas’ Fastest-Growing Companies by the Financial Times.
Penetration Testing Types We Provide
To precisely target your security needs, our security testing agency offers a full range of penetration testing services:
External penetration testing
We detect and exploit weaknesses in internet-facing IT assets such as web applications, APIs, email services, websites, firewalls, etc.
Internal penetration testing
We investigate how intruders who got access to your internal network can compromise your IT environment.
Application pen testing
We perform vulnerability scanning and code review to detect security flaws. After that, we attempt to exploit them to evaluate their potential impact. As a result, we identify, prioritize and help fix all the existing front-end and back-end vulnerabilities.
Our team assesses how well your company can withstand widespread phishing and vishing attacks. We imitate the techniques of psychological manipulation that real-life attackers use to trick people into divulging sensitive information or breaking security rules.
Penetration testing for compliance
Our cyber security penetration test experts focus on specific compliance requirements applicable to your company, such as GDPR, HIPAA, PCI DSS, SOC 2, and others.
We detect cloud, VPN, and firewall misconfigurations, access control and RDP flaws, and other vulnerabilities that can compromise the security of remote work.
Wireless penetration testing
We explore your corporate Wi-Fi, WLAN, and Bluetooth connections to prevent piggybacking, evil twins attacks, wireless sniffing, unauthorized access to corporate wireless devices, and other real-world threats.
Open-source intelligence (OSINT)
We investigate what info about your company is exposed in publicly available sources and how hackers may use it to launch their attacks.
We perform a series of real-time attacks without informing your IT team and employees about their scenarios and exact duration. This testing type allows for a comprehensive assessment of preventive security controls, detective tools, cybersecurity awareness, and incident response mechanisms.
Not sure what to choose?
Let's discuss your security needs — ScienceSoft's experts will analyze your case and recommend the optimal pentesting type and approach.
Penetration Testing Approaches We Are Proficient In
Value: best for simulating real-world external hacks, faster and cheaper than other techniques.
Conditions: we have strictly limited knowledge of the testing targets, no information on your security policies, software or network specifics and security controls.
Value: combines the depth of exploration with time- and cost-efficiency.
Conditions: we have some information about the testing targets: admin or user credentials, architecture diagrams, etc.
Value: helps reveal maximum external and internal vulnerabilities.
Conditions: we have full access to and complete information about the apps/IT infrastructure components in scope: e.g., source code or architecture documentation, database encryption principles, credentials for different access levels, etc.
Discover How ScienceSoft's Pentesting Engagement Unfolds
We start with discussing your requirements and concerns to suggest a tailored testing strategy. Throughout the pentesting, our project manager will stay in touch with you to provide updates on the process and align it with your new requirements if they arise. Along with a comprehensive final report, our experts can provide additional explanations on the findings, remediation measures, and the optimal next steps to improve your cybersecurity posture. Our free retesting will help you avoid doubts about the remediation results and confirm your new security level.
1
Pre-attack phase / Planning
- Defining the intruder model (internal or external, enabled rights and privileges).
- Defining goals, source data, scope of work and testing targets.
- Determining the scope of a target environment.
- Developing the testing methodology.
- Defining interaction and communication procedures.
2
Attack phase / Testing
- Fieldwork, service identification.
- Custom scanning or intrusion tools are developed if needed.
- Identifying vulnerabilities and eliminating false positives.
- Vulnerabilities exploit and gaining unauthorized access.
- Utilization of compromised systems as a springboard for further intrusion.
3
Post-attack phase / Reporting & remediation
- Analyzing the findings; designing and prioritizing the optimal remediation measures.
- Performing the needed remediation activities (if required): segregating the network, tuning security configurations across network components and applications, fixing code security issues in software design and code, and more.
- Conducting a follow-up testing round to check if all fixes have been applied correctly.
ScienceSoft: More than Just a Penetration Testing Company
We’ve put a lot of work into our cybersecurity service offer to be able to provide for any security needs our customers may have. We provide cybersecurity consulting to help design and build secure apps and networks, develop and adopt efficient security policies. We offer targeted security testing: vulnerability assessment, source code review, penetration testing, social engineering testing. We also perform comprehensive security checkups, such as risk assessment, compliance assessment, IT security audit and more. Our security engineers can implement and customize security solutions to fit a specific IT environment: firewalls, endpoint protection systems, DLP, IDS/IPS, IAM, SIEM, SOAR, etc.
Penetration Testing Deliverables
|
|
Penetration Testing Cost Factors

The price of a penetration testing project generally starts from $5,000. It may vary greatly, depending on the scope and complexity of the project, in particular:
- Testing type: e.g., red teaming, social engineering testing, an internal pen test.
- Testing approach: white/gray/black box.
- Testing targets: e.g., the number of applications, user roles, API subnets, public-facing IPs or employees to be tested.
- Pentesting team: the number of testers and their qualifications.
How much will penetration testing cost for your project?
Tips on how to reduce the costs of 3rd party penetration testing
- Keep an inventory of your assets and prioritize them. You may want to focus on the data, apps, and IT infrastructure components that are critical to your business, covered by compliance requirements, or that have undergone significant modifications.
- Find a reliable long-term security partner. Some penetration testing agencies, including ScienceSoft, offer favorable terms and a reduced price for repeat business and long-term engagements.
- Ask your pentesting firm to provide a tailored cost optimization plan. Penetration testing consultants can outline an optimal testing scope to avoid extra spending. They can explain how to minimize your company's attack surface, thus reducing the pentesting scope.
Wondering How Much a Professional Pen Test Will Cost You?
Answer a few simple questions about your pentesting needs. This will help our team provide a tailored estimate for your case much quicker.
Our team is on it!
ScienceSoft's experts will study your case and get back to you with the details within 24 hours.

Explore the Advantages of ScienceSoft's Pentesting Services
Complete view of vulnerabilities
We provide detailed information on real security threats, help to identify the most critical and less significant vulnerabilities along with false positives, so that the Customer can prioritize remediation, apply needed security patches and allocate security resources.
Avoiding the cost of system/network downtime
ScienceSoft’s team provides specific guidance and recommendations to avoid financial pitfalls by identifying and addressing risks before attacks or security breaches occur.
Customized Services to Maximize Pentesting Benefits
Our customized approach to penetration testing helps resolve the specific challenges that organizations of different sizes encounter.
Small companies and startups
- Cost-effective security enhancements: a skilled pentesting team identifies critical vulnerabilities and prioritizes remediation measures, enabling organizations to strengthen their cyber defense without excessive security spending.
- Building customer trust, which is vital for small or new businesses that try to establish themselves in the market. Regular pentesting demonstrates a company's commitment to security and helps prevent reputational losses related to security breaches.
Midsize businesses
- Vendor assurance: business partners or clients may require pen testing as part of their vendor risk management, ensuring compliance and demonstrating that the vendor adheres to robust cybersecurity practices.
- Learning opportunity: Seasoned pentesters can offer your IT team valuable insights into security best practices and optimal security improvements, fostering corporate cyber awareness and skill development.
Large enterprises
- A thorough exploration of complex IT infrastructures that are inherently challenging to maintain hack-proof. Pentesters skillfully identify security vulnerabilities across various devices, networks, and applications, and outline the necessary improvements.
- Preventing advanced security breaches. Pentesting helps evaluate if a company is prepared to defend against targeted attacks and sophisticated hacking techniques that traditional security measures may struggle to contain.
Pentesting Tools vs. a Pentester's Intelligence: Which Is Better?
At ScienceSoft, we combine advanced penetration testing tools with manual exploration. As a result, our clients can expect a flexible and cost-efficient service, as well as fast and comprehensive results.
|
|
Automated penetration testing |
Manual penetration testing |
|---|---|---|
|
Pros
|
|
|
|
Cons
|
|
|
Tried and True Tools Our Pentesters Use
For each specific pentesting project, we carefully choose the optimal security tools to ensure fast results and all-around vulnerability exploration.
Tailored Assistance: Service Options We Offer
Frequent Concerns About Pen Testing Services Answered
How can we be sure that a pen test won't expose our confidential information?
We have a solid security management system confirmed by ISO 27001 to ensure full security of our customers' data we access. Also, it is a standard practice for us to sign non-disclosure agreements.
How long does a penetration test take?
The project timeframe depends on its scope and the number of ethical hackers involved. From our experience, the testing phase commonly takes 3–10 days, while the entire engagement (from planning to reporting) may last 2–4 weeks.
How do you verify the effectiveness of remediation measures?
We offer 2 weeks for remediation activities and another testing round to check if all security gaps have been correctly fixed. Don't worry, if vulnerability remediation takes you more time than expected, we'll find the time to do the retesting for you to be sure about your enhanced security level.
Can you fix the security flaws you find?
Yes! We are happy to be a one-stop shop for our client's security needs. Our senior developers and seasoned security engineers are ready to fix any vulnerability to make your IT environment hack-proof.
How Penetration Testing Helps Prevent Major Cyber Threats
Companies must take comprehensive and consistent measures to protect themselves from ever-evolving cyber attacks. Penetration testing is a great way to significantly reduce the risk of security breaches.
Ransomware
- Sending phishing emails with malicious links and attachments to evaluate the risks of ransomware infection due to human error.
- Checking your apps and IT infrastructure for vulnerabilities that allow infection with malicious files.
Phishing attacks
- Checking if your email security tools can recognize and stop suspicious emails.
- Running different phishing attack scenarios to check the cyber resilience of your employees and C-suite.
Remote work security risks
- Identifying VPN and RDP vulnerabilities.
- Checking access controls in place.
- Testing if remote workers can recognize and handle phishing attacks.
Insider threats
- Investigating what security flaws malicious insiders are likely to exploit and what harm they can inflict.
- Conducting social engineering testing to check if your employees can unintentionally break security rules.
Stolen/lost device
- Evaluating authorization and authentication mechanisms in place: e.g., if MFA and strong passwords are implemented.
- Checking if corporate data is properly encrypted.
Compliance breaches
- Testing apps and IT infrastructure components that influence your compliance.
- Social engineering testing to prevent security breaches due to human error.
- Pen testing reports and attestation letters to prove your company's due diligence in case of a compliance audit.
Alarming Stats You Cannot Ignore
|
Over 25K new vulnerabilities were reported in 2022 (CVE Details) |
$4M was the average total cost of a data breach in 2022 (IBM) |

 Schedule a call
Schedule a call







